Internal and external threats proliferate and evolve, challenging businesses large and small.
In the second of a three-part series on the state of cybersecurity, we take a closer look at the threat environment, and how internal and external factors can impact - if not cripple - an organization. Part one discussed the basics of cybersecurity, the five core functions (Identify, Protect, Detect, Respond and Recover) and the requirement to combine all elements (people, products and process) in a holistic manner that evolves with the threat environment. Part three will look at why the size of your organization doesn’t matter in cybersecurity.
Data breaches are the new normal for businesses large and small. There are a myriad of factors and trends driving the need for a new approach to cybersecurity, the most important being that the preferred method, protection, isn’t working. While more than half of organizations blame a security incident or data breach on a negligent or malicious employee, the threat environment includes a growing number of external challenges, i.e. viruses, malware, botnets, ransomware, denial of service attacks, APTs and worms.
“Breach is the new normal,” according to IDC. By 2020 1.5 billion people, or 25% of the global population, will be affected by data breaches, said the research company.
There were 744 million data breaches reported in 2015, as a result of cybercrime, and almost 320 million for the first half of 2016. Most breaches (89%) had a financial or espionage motive, and in 93% of cases, it took attackers minutes or less to compromise systems and data exfiltration occurred within minutes in 28% of the cases. Most alarming: 95% of all security breaches were caused by human error.
While both the time to identify and time to contain were highest for malicious and criminal attacks (229 and 82 days, respectively), data breaches caused by human error (162 and 59 days, respectively) are still cause for great concern, according to another recent study. The mean time to identify (MTTI) was 201 days with a range of 20 to 569 days, and mean time to contain (MTTC) was 70 days with a range of 11 to 126 days.
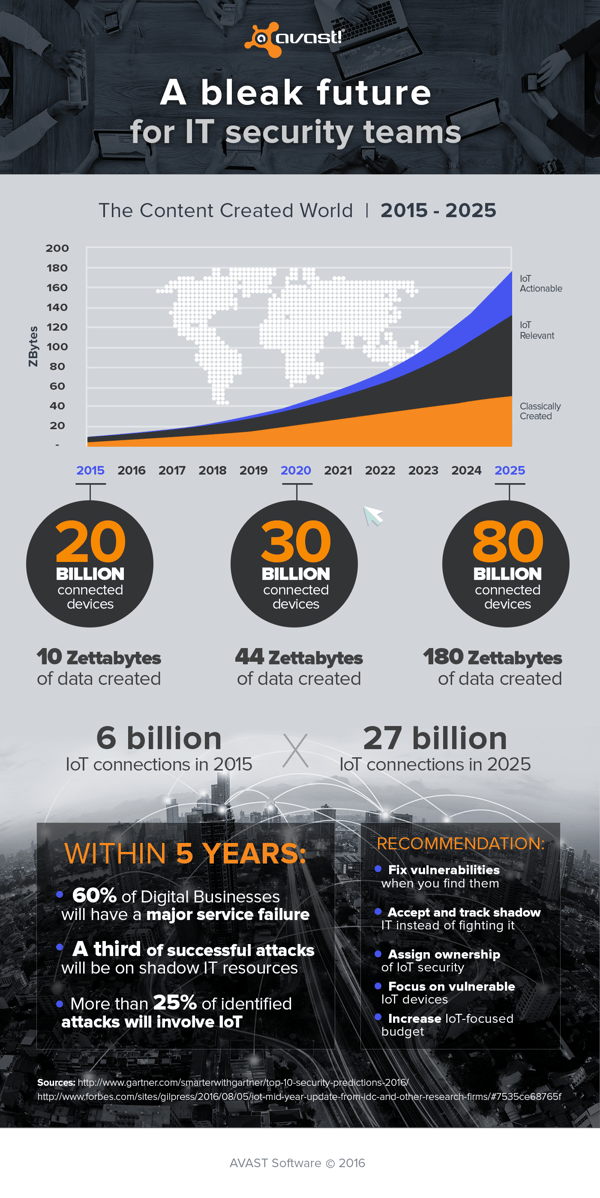
A bleak future for IT security teams
By 2020, 60% of digital businesses will suffer major service failures due to the inability of IT security teams to manage digital risk. ‘IT, operational technology (OT), the Internet of Things (IoT) and physical security technologies will have interdependencies that require a risk-based approach to governance and management.’
By 2020, 99% of vulnerabilities exploited will continue to be ones known by security and IT professionals for at least one year. In a recent healthcare survey, 78% of respondents reported that the most common security incident is the exploitation of existing software vulnerabilities greater than three months old.
By 2020, a third of successful attacks experienced by enterprises will be on their shadow IT resources - IT hardware, software and services not owned or controlled by organizations. That’s a huge concern, as most organizations (92%) are currently experiencing the effects of shadow IT.
By 2020, more than 25% of identified enterprise attacks will involve Internet of Things (IoT), though IoT will account for only 10% of IT security budgets. “The IoT redefines security by expanding the scope of responsibility into new platforms, services and directions,” said Ganesh Ramamoorthy, research VP at Gartner.
These risks and threats are escalating because of the move to a digital world, which is being driven by the growth in volume, velocity and significance of data, devices and people requiring access to this digital deluge. Between 2020-2025 the volume of traditional data will grow by 2.3x; the volume of data that can be analyzed will grow by 4.8x; and the actionable data will grow by 9.6x. Connected devices will grow by more than 50% between now and 2020, to 30 billion, and then more than double again by 2025 (80 billion).
The threat environment is getting more threatening
Cybersecurity is becoming the bad news/good news story of IT and digitization. On the one hand, the threat environment is becoming more hostile, with organizations having less direct infrastructure and their biggest security concerns will come from services outside their control. The good news is that cybersecurity is becoming the foundation of digital business and innovation, and can be a competitive advantage.
“Protecting information alone isn’t enough, and ensuring the confidentiality, integrity and availability of that information isn’t enough,” said Tom Scholtz, VP and Gartner Fellow. “Risk and cybersecurity leaders must now assume the responsibility of providing safety for both people and their environments.”
In Part 3 we’ll examine how small and medium businesses face an even more daunting cybersecurity threat environment, and how they can protect their organizations from internal and external threats.