Ransomware has been a prominent threat in cybersecurity for more than a decade, but the rates of incidents are showing slight decline. The Avast Q1/2023 Threat Report examines why.
What’s on your computer right now?
Let’s make a list. Start with every work-related document you’ve used or created in the last six months. After that, perhaps your monthly budgets, pictures from your last vacation, all your passwords (in a vault, we hope), email attachments, bank statements, insurance information, your browser bookmarks, and that novel you haven’t finished.
Now let’s say you logged in tomorrow and found all that information gone, with a note on your desktop from a hacker instructing you on how to make payment to get your data back.
This is ransomware, and it’s the category of malware that encrypts a victim’s data and demands payment in exchange for a decryption key. The attack renders documents, photos, videos, databases, and other files on a computer or network useless, and frequently threatens to delete the data entirely.
The rise of ransomware
Ransomware came into popularity for bad actors as our working (and playing) lives became interconnected with technology. Our laptops, tablets, and smartphones became more and more a central part of our lives. The opportunities for cyber criminals grew, so the attacks grew as well.
The first highly successful ransomware technique surfaced in 2012, when the Reveton Trojan infected computers and displayed fake messages claiming to be from law enforcement agencies, accusing the victim of illegal activity and demanding payments to avoid prosecution.
And it worked. That technique netted an average of $400,000 per month for attackers,, and enabled cybercriminals to install additional malware to further steal passwords, data, and sensitive information. As time went on, Reveton evolved into more advanced forms, while other ransomware tools with names like WannaCry, BlackMatter, and LockBit bloomed in popularity and use over the next decade.
As long as it remains profitable, ransomware will continue to be a threat. The way of pushing back against this type of attack is to significantly decrease its effectiveness.
How ransomware spreads
Like many malware attacks, ransomware spreads through a variety of methods, with attackers constantly refining their techniques to maximize impact and reach.
The way hackers find their way into computers and networks is similar to how most viruses spread. Phishing emails, malicious websites, corrupted files and downloads, and social engineering all play a part in how the virus finds its way to your data.
There’s a deeper threat if you’re working within an organization. Ransomware can spread laterally across networks after an individual device is infected. Attackers exploit the connections within unsecured and unpatched systems to spread and infect other devices and servers within an organization’s network.
What’s unique about this attack is that viruses normally attempt to hide their presence while they infiltrate systems and computers. Quite the opposite, ransomware wants users and system admins to know it’s there, and in a big way. The attack changes color schemes of the targeted computer and can leave notes on the infected desktop, making sure the victim knows they’ve been infiltrated and raising a sense of threat and urgency.
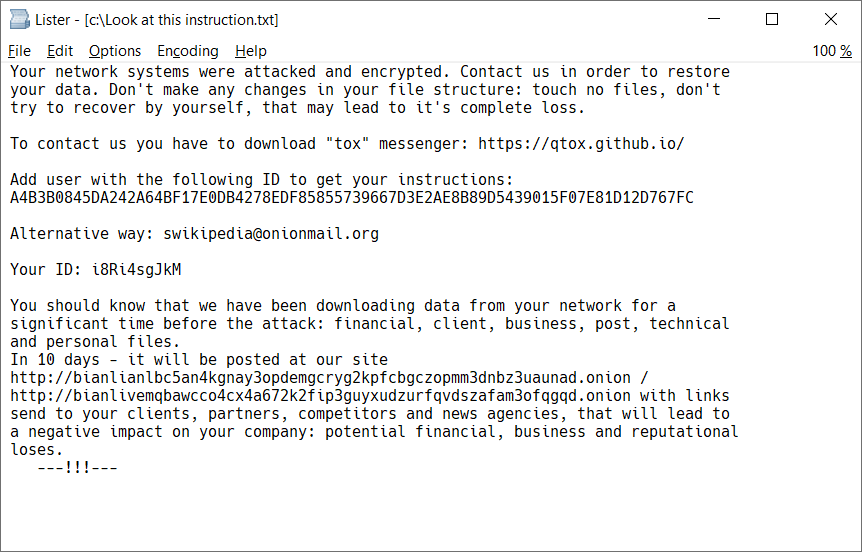
In some cases, like the above, the malware will identify itself, inadvertently giving victims an advantage in fighting back without paying. For example, the BianLian strain shown above can be decrypted using a tool that Avast released in January 2023.
Understanding the escalation of ransomware tools
So what’s at stake? Not just your data. If you fall victim to a ransomware attack, you can suffer financial loss from paying the ransom. The sensitive and private data you have on your device can be stolen in the process, leading to financial fraud and identity theft. Within an organization, the virus can spread deeper, and you could even lose trust among your colleagues and IT administrators.
There are preventative steps any individual or organization can take to head off the need to ever pay a ransomware attacker.
An effective preventative step nearly anyone can perform is to create secure data backups to an isolated server or a third-party service. If a laptop other digital device become infected and are held for ransom, the critical data is safely stored elsewhere, and the affected computer can be cleaned and reformatted.
When infected, the encrypted data should be backed up in the chance that the encryption keys may be made available for free in the future. That was the case with MeowCorp ransomware, which had it’s encryption code leaked. Thus, Avast published the Conti Decryptor in March 2023.
Today’s ransomware statistics
Avast helps detect and block ransomware globally, and we gather anonymous intelligence about what intrusions occur where. Thus, our data is a front-row seat for what attacks are being employed by bad actors.
WannaCry, which infects systems using Microsoft Windows, is still the most common ransomware attack at 18% of the market share, followed by the STOP ransomware attack at 15%. Other attacks such as Thanatos, Hidden Tear, Magniber, and LockBit are also commonly detected.
Overall, the number of ransomware attacks Avast defended against in the last three months has declined, as ransomware authors are switching to more sophisticated attacks that are more targeted and specific than the broad-sweeping attacks seen in the last 10 years.
The rise and fall of ransomware is a testament to the rapidly evolving nature of cybersecurity threats and the need for constant adaptation. While attacks have declined in the last year, the threat remains real, and anyone with a laptop, tablet, or smartphone must remain informed, vigilant, and prepared to defend against this and other types of intrusions. By staying aware, implementing best practices, and working together, we can continue the fight against cyberthreats and build a more secure digital future.
Read more about ransomware, hacker tactics, and financial cyber threats in the Avast Q1/2023 Threat Report.