Avast’s Jakub Kroustek answers open questions about Petna, the Petya-based malware that spread and infected computers around the world
Earlier this week, we saw another mass ransomware attack happen, less than two months after the WannaCry outbreak. In the hours and days after the attack, this strain was given many different names, including Petya, Petna, NotPetya, EternalPetya, Nyetya, and many more. We originally referred to it as Petya-based, but for simplicity, let’s call it Petna.
There is a lot of uncertainty around Petna, not just around what it should be called. Is it Petya ransomware or a variant of Petya? Should Petna be considered ransomware or a wiper? Was Petna designed to destroy or was it spread for financial gain?
Let’s clarify some things based on currently available information:
Is Petna still spreading?
Not really. Petna peaked three days ago. The spreading started early on June 27. Petna peaked on that day, with thousands of attack attempts every hour. After this peak, the intensity of the attacks significantly dropped on the same day and since then, we have been observing a very low prevalence.
Can this attack be compared to WannaCry?
Not as far as our user base is concerned. We observed about 20,000 attacks over the world, which is way lower than the 1.5 million WannaCry attacks we’ve stopped so far.
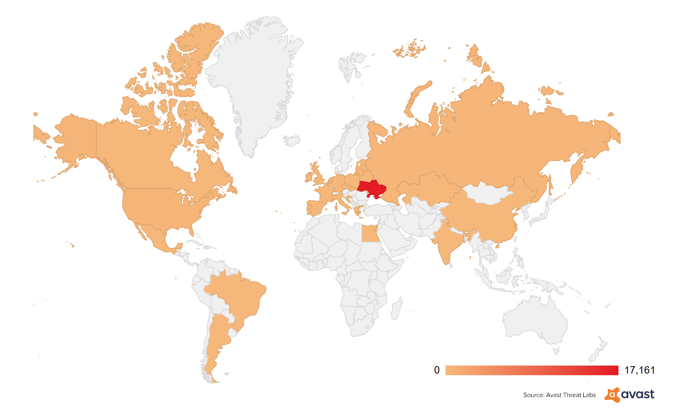
Which countries were affected the most?
Based on our telemetry, the Ukraine was most impacted by far, with more than 90% attacks detected there. The others were the US, Russia, Lithuania, Belarus, Belgium, and Brazil, with dozens to hundreds of attacks attempts in each of these countries.
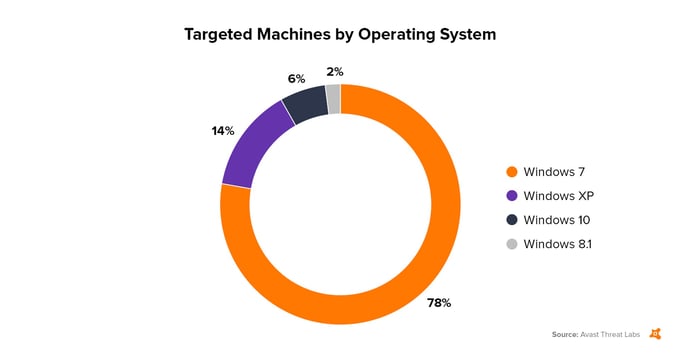
Which operating systems were affected?
Most of the attacks observed by us occurred on Windows 7 PCs (78%), followed by Windows XP (14%). The number of attacks on more modern systems was much lower.
How did Petna get onto PCs?
As we analyzed the outbreak, we’ve found an infection vector tied to an updater for the Ukrainian accounting software, M.E.Doc, which is the reason why the Ukraine was hit so badly.
This is a bitter paradox, as users are always advised to update their software, but in this particular case, a trojanized updater of this software started the infection chain.
However, there is still an ongoing investigation of other possible infection vectors.
Why were computers outside of the Ukraine also affected?
One of the reasons is that some of the companies affected have subsidiaries in the Ukraine. Once Petna infected a computer, it spread within the network, which is how Petna was able to reach computers in other countries. We are still investigating the other possible infection vectors.
What happens after Petna infects a computer?
After infecting a machine, Petna tries to encrypt files with specific extensions. The list of targeted files is not as long as the target list of usually used by ransomware strains, nor is it as long as the original Petya, but it contains formats used for things like photos, documents, source codes, databases, disk images, etc. Apart from file encryption, Petna also acts as a worm, meaning it tries to self-replicate on other machines connected to the local network. As we described in our previous blog post, it employs three different spreading methods: exploiting EternalBlue (known from WannaCry), exploiting EternalRomance, and a spreading via Windows network shares by using victim’s stolen credentials (this is done via a bundled Mimikatz-like tool, which extracts passwords) and legitimate tools like PsExec and WMIC. Finally, after encrypting files and spreading itself, it tries to prevent Windows from booting (by changing the Master Boot Record – MBR) and after a forced restart, it encrypts the Master File Table (MFT) of the system drive. This prevents the computer from booting back into Windows and thus makes the computer unusable.
Can I be infected with Petna even if my computer is fully patched?
Yes, you can because of a lateral movement of the malware, described above. If both EternalBlue and EternalRomance are patched on a particular machine, it can still be infected by the third delivery method.
Is it Petya, WannaCry 2.0, or something else?
Petna is definitely based on Petya, for example the MFT encryption part is almost identical to the previously seen “Golden” Petya. However, it is not identical and there are some differences that were previously unseen in past versions of Petya. The modifications suggest that they might have been done by someone other than the original authors of Petya, Janus, who also commented that on Twitter.
The main similarity between Petna and WannaCry is that they both used the EternalBlue exploit to spread.
There are rumors that this Petna isn’t encrypting anything and just wipes drives?
This is not true. This strain is encrypting files and MFTs. However, whether these files can be decrypted or not is a different question.
Is there a free decryptable tool available?
Unfortunately no. The encryption used is strong enough to be unbreakable. In addition to encrypting files, Petna also encrypts MFTs, which makes the decryption process very hard.
Should you pay the ransom demand?
No! We never recommend paying ransom, because paying the ransom supports criminals, which could encourage them to continue. Further, there is a high chance that you will not get your data back even if you pay. In this particular case, it is more obvious than ever before. Why, you ask?
- The official email address wowsmith123456@posteo.net, shown in the ransom screen, where victims were told to send the ransom, was shut down by the email service provider shortly after the outbreak. So, Petna’s operators cannot know who paid and who didn’t.
- Decrypting the MFT part is not even possible, because the key is lost after Petna encrypts the MFT. In previous versions of Petya, this key was stored in the victim ID, but in Petna’s case, this is just a random string.
- Furthermore, the encryption used for the files is pretty messy. As we previously pointed out, there is a bug in the implementation, which can make some of the files unrecoverable.
- Even if we put the above points aside, it would be really tough for Petna’s operators to fully decrypt the computers they infected. The decryption would involve multiple iterations of communication with victims, so that the MFT could be decrypted first, followed by the files.
As you can see, the chances of fully decrypting an infected computer, even if done by Petna’s authors, are close to zero.
Nevertheless, Petna victims are still paying the ransom. At the time of writing this post, Petna’s bitcoin wallet contained nearly 4 Bitcoins, ~$10,000. Not so much compared to damage done.
Was this a test run? Can we expect more attacks like this?
Many speculated that WannaCry was a test run, but there are no indicators that this is true. However, it is highly likely that we will see more and more wormable ransomware strains, especially given that WannaCry and Petna have confirmed this concept to be viable.
What was the intention behind this attack? Was it a state-sponsored attack?
(Searching for a crystal ball ... ). Let’s sum up the facts. This attack, as well as multiple others spotted during last months, has most heavily targeted the Ukraine. This recent attack used a modified version of one of the most advanced and also most destructive ransomware strains seen so far – Petya. The modifications and additions of Petya are more than suspicious – the people behind these modifications crippled a working ransomware into an undecryptable one. Furthermore, they made paying the ransom senseless, which is abnormal for ransomware, as the motivation behind spreading it usually to earn money. The payment was not associated with a Tor site, but with an email address hosted by a common provider and it became quickly known that Petna was not decryptable, which resulted in a relatively low ransom payments.
If we step aside for a moment, we can say that we've already seen dozens of poorly coded ransomware strains that made decryption nearly impossible and these flaws were almost certainly unintentional by their authors. We’ve also seen other criminals taking existing ransomware binaries and just patching payment instructions to display their own wallets, again resulting in victims with unrecoverable files. And finally, we see test versions of new ransomware strains released in the wild almost on a daily basis – often with fatal flows in encryption algorithms and/or without any payment instructions.
If we continue to think about Petna as a ransomware, we will find many similarities with the previous cases – and we could conclude that the flaws in Petna were probably the result of simply sloppy work.
However, because of Petna’s impact, we must also think about Petna outside of the box. One of the possibilities is that the primary purpose was to “just” cause some damage. In this case, we must admit that its authors were successful. Based on a publicly available information, hundreds of machines were infected, and useless, bringing companies to a stand still. From this point of view, the ransomware story would be just a cover maneuver with a nice side-effect for its authors – $10K in their Bitcoin wallet. And finally, there’s also a working theory that all of the mess done by Petna was to cover up other (stealthy) attacks that were carried out at the same time.
Avast detects and protects its Avast and AVG users from all known variants of Petna by using our multi-layered protection shields including File Shield, Behavior Shield, and Ransomware Shield, as well as firewall-capable detecting exploits.
Image: Reuters