Petya-based ransomware is spreading and infecting computers around the world.
Further to reports of a massive cyber attack hitting a number of companies in Ukraine, including banks, energy companies and transport services as well as the government. Avast believes this is another example of the Petya-based ransomware, which was first identified in 2016. A few months ago, Petya ransomware was spotted patched and bundled as a different malware strain called PetrWrap. The attack appears to be spreading with incidents being reported in Russia, India, France, Spain and also the Netherlands. Malware writers behind the attack, are demanding a $300 ransom to be paid in the Bitcoin cryptocurrency.
As we analyzed this outbreak, we’ve found an infection vector tied to an updater for Ukrainian accounting software, MEDoc.
Once this modification of Petya infects the network, it continues spreading using two different methods. The methods are: 1. spreading via Windows network shares by using victim’s stolen credentials (this is done via a bundled Mimikatz-like tool, which extracts passwords) and legitimate tools PsExec and WMIC. 2. by abusing two SMB vulnerabilities, EternalBlue (the same vulnerability used to spread WannaCry) and EternalRomance. Microsoft released a patch for both vulnerabilities in March.
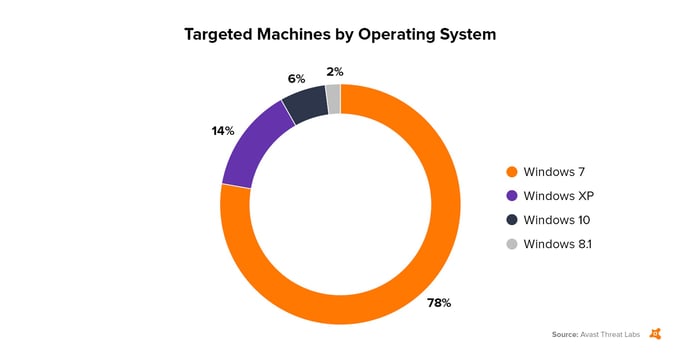
We have seen 12,000 attack attempts today (2017-06-27). Data from Avast’s Wi-Fi Inspector, which scans networks and can detect if an Avast PC or another PC connected to the same network is running with the EternalBlue vulnerability, shows that 38 million PCs that were scanned last week have not patched their systems and are thus vulnerable. The actual number of vulnerable PCs is probably much higher. The top 4 targeted operating systems, according to our data, are (in order): Windows 7 (78%), Windows XP (14%), Windows 10 (6%) and Windows 8.1 (2%).
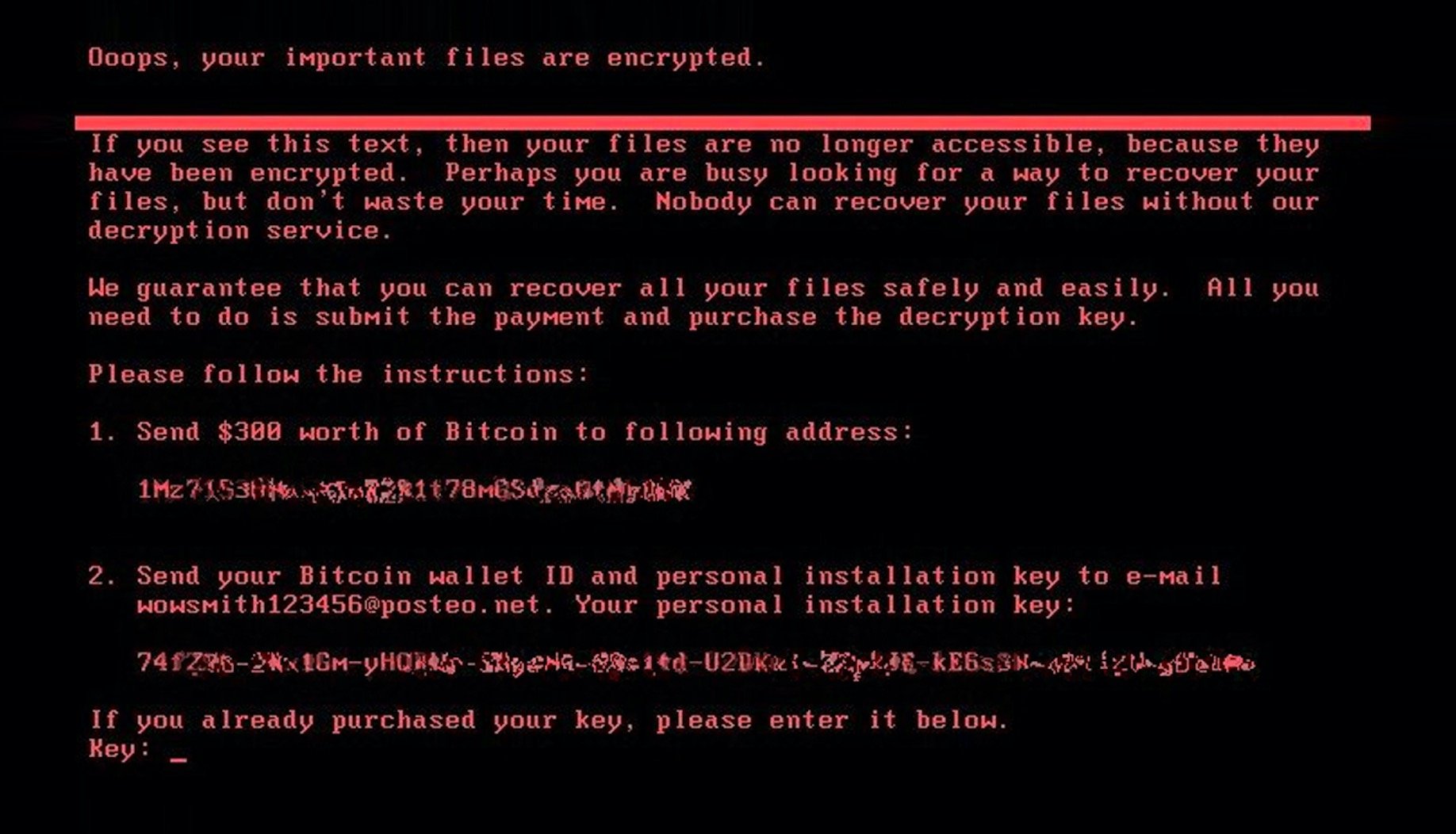
This strain encrypts files with AES-128 encryption (CBC mode) with a randomly generated key. This AES key is further encrypted by using a public RSA-2048 key that is stored in the sample. The resulting encrypted key is stored to the README.txt file together with ransom notes. After the encryption, the ransomware also modifies the Master Boot Record (MBR) of the system drive, which prevents Windows from starting after the next restart, which is invoked by this strain after encryption. At the end, the victim will only see an image similar to one depicted above.
While we don’t know who is behind this specific cyber attack, we know that one of the perfidious characteristics of Petya ransomware is that its creators offer it on the darknet with an affiliate model. This provides its distributors a share of up to 85% of the paid ransom, with 15% retained by the malware authors. The authors also provide the entire infrastructure, C&C servers, and the money transfer method. This type of model is called "ransomware-as-a-service" (RaaS), which allows malware authors to win over non-tech savvy customers to distribute their ransomware.
Avast Protection
Customers using the latest versions of Avast, are protected against the Petya-based ransomware. If your PC is infected with Petya, our antivirus will detect it, quarantine it and destroy it. If it detects Petya is trying to enter your computer, it will block it from getting in. We will provide regular updates to protect against possible future variants. If you are concerned, please ensure your antivirus software is up-to-date. Finally, we strongly recommend that all Windows users, update their systems and applications with any available patches as soon as possible.