Protect yourself and your business from this troubling new trend.
Microsoft included Remote Desktop Protocol (RDP) with its offerings for the first time in 1996. Since then, cybercriminals have been trying, sometimes with success, to hack into machines via this protocol and we’ve seen countless RDP attacks done by different malware types. But a troubling, growing trend of this brand of cyberattack, that started a few years ago, has been locking up systems with ransomware, crippling the targeted business temporarily at best. The Internet Crime Complaint Center (IC3) along with the US Department of Homeland Security recently released an alert stating, “Remote administration tools, such as Remote Desktop Protocol (RDP), as an attack vector has been on the rise since mid-late 2016 with the rise of dark markets selling RDP Access.“
Let’s look at this RDP threat, see what happens when an RDP is exploited, and learn how to stay protected from RDP attacks.
RDP has been used as a trusted tool since its inception. The usefulness of connecting remotely to a desktop has literally changed the way much of the world conducts business. Every version of Windows from XP onwards has been equipped with a Remote Desktop Connection feature. The business world quickly adopted the technology, before long relying on its convenience. Unfortunately, when not managed and configured correctly, it also opened a new infection vector for attackers.
What is RDP?
Remote Desktop Protocol (RDP) is used to allow remote access from one machine to another, e.g. an employee working remotely can access a workstation or server located in his company. It could be as simple as running RDP client software on a laptop and connecting to a machine with RDP server counterpart. RDP then provides an encrypted connection between both endpoints.
How is RDP vulnerable?
A vulnerability in RDP implementation and its following exploitation happens from time to time and this type of attack is mostly effective against older and unpatched systems.
However, it is not the primary type of RDP attack that we are witnessing in-the-wild. A brute-force attack on weak login credentials happens far more often. In this type of attack, the attacker automatically and tirelessly tries multiple password combinations until the correct solution is found. Weak passwords, and of course leaked passwords, can also be leveraged to get inside.
The most notorious fails, however, occur when the RDP access is opened to the whole internet (specifically, port 3389). If the security settings at either endpoint are misconfigured, it leaves a doorway for interceptors to find and hack into the targeted machine.
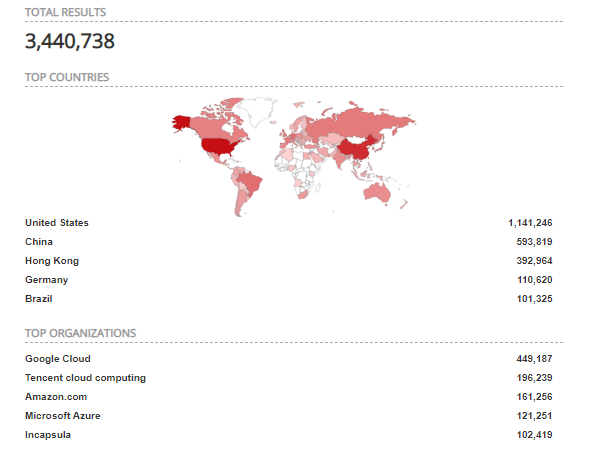
Latest data from Shodan.io showing devices that
are most probably running RDP open to the internet
Recent RDP attacks
The attacks that we’ve been seeing lately in greater numbers involve a cybercriminal hacking into the RDP (using one of the methods described above), then logging in as a regular user, oftentimes with admin rights. He or she then simply disables any installed antivirus, and manually uploads and runs the ransomware.
For example, the ransomware strains ACCDFISA, SamSam, and CrySiS (aka Dharma) have been spreading almost exclusively via RDP for years. In the Avast Threat Labs, we’ve recently discovered new CrySiS variants Brrr, Gamma, and Monro, which confirms that these strains are still actively developed. Furthermore, we have noticed a change in the preferred delivery methods of multiple ransomware strains including Rapid and GlobeImposter — they are all now being delivered primarily via RDP attacks.
The results of a successful ransomware attack can be devastating. We’ve seen such cases, where RDP has been used as an infection vector, in the entertainment industry, the garment industry, logistics companies, NGOs, and more, from all over the world. Medical centers losing access to their patient records. Individuals losing access to their own family photos. Nobody likes to be a victim of ransomware — it’s a horrible experience, which is why we are urging you to protect yourself against it.
RPD protection
The key takeaways here are these:
1) Make sure your RDP connection is not open to the internet. Configure the settings so that it is only accessible through an internal network. The traffic in the default ports can be blocked at the firewall level.
2) Disable RDP if your business does not need to use it. If you do need to use an RDP, we recommend you use Remote Desktop Gateway.
3) Always use strong passwords, especially on administrator accounts. Remember to make each one complex and completely unique. Consider using multi-factor authentication.
4) Back up, back up, and… BACK UP!
If you ever get infected with ransomware, we strongly suggest you do not pay the ransom, as all-too-often the ransomers never deliver the decryption key. Check our free decryption tools — one of them may help.
As with all cybercrime, the best protection is proactive defense. We protect our business clients from cyberattacks and ransomware with Avast Business Antivirus, as well as our premium business AV suites. Let us help you save yourself from falling victim to RDP attacks, ransomware, and whatever they think of next.