The Avast Guide to Android Apps Part 4 explains what you need to know about permissions.
In the grand scheme of all things security, app permissions are generally treated as the least important. After all, who hasn't felt that pang of impatience when shown one yes-or-no option after another, when all we want is to start using that cool new app? Indeed, many of us skip right over reading the permissions page when installing an app, but doing so, as we shall see, can be a (very) costly mistake.
While it is extremely important that you take the time to know whether or not an app is safe to install, understanding how app permissions work can also help you circumvent many threats out there. Let’s get started.
Normal vs. dangerous permissions
Some permissions carry more weight than others. Certain permissions — like accessing the internet, killing background processes, and reordering tasks — are classified as “normal” because they do not pose a threat to the user. Others, such as accessing the calendar or contacts, recording audio, using body sensors, and reading external storage are considered “dangerous” permissions. Check out the full list of Android permissions.
While users of Android 6.0 and onwards can decide what permissions to give an app after it has been installed, those on operating systems prior to that have to use an all-or-nothing approach. In other words, they have to agree to allow an app access to all permissions it requests, or they can not install it. Cybercriminals used to be able to get around permissions by creating apps that require these older API (application programming interface) levels to download.
That loophole has since been closed, and Google now requires apps to comply with Android 8.0 or later as of August 1, 2018. App updates are required to do the same as of November 1, 2018.
Avast Guide to Android Apps
Part 1: How to tell if an Android App is safe to install
Part 2: How to detect and remove a virus from your Android phone
Part 3: Why is my Android phone heating up?
Understanding dangerous permissions
Because you grant permissions to an app before installation, it’s best to know how permissions affect your privacy. Dangerous permissions are categorized into nine groups. When you grant or deny a group permission, your action encompasses all permissions within that group. The nine groups are as follows:
 Body Sensors — These permissions relate to heart rate monitors, fitness trackers, etc. While they enable fitness devices to track your health, a malicious app could record the same information from your device and send it to its C&C.
Body Sensors — These permissions relate to heart rate monitors, fitness trackers, etc. While they enable fitness devices to track your health, a malicious app could record the same information from your device and send it to its C&C.
 Calendar — These allow apps to read, edit, create, and delete calendar events. Calendar permissions are used by social networking apps, and they are very useful for managing appointments. But they open the door to a whole lot of very personal information you may not want falling into the wrong hands.
Calendar — These allow apps to read, edit, create, and delete calendar events. Calendar permissions are used by social networking apps, and they are very useful for managing appointments. But they open the door to a whole lot of very personal information you may not want falling into the wrong hands.
 Camera — These permissions allow apps to take pictures and record audio and video. The very thought that a malicious app may be sending the device’s photos to a cybercriminal should send a chill down anyone’s spine.
Camera — These permissions allow apps to take pictures and record audio and video. The very thought that a malicious app may be sending the device’s photos to a cybercriminal should send a chill down anyone’s spine.
 Contacts — This permission set gives apps the power to create, edit, store, and delete contacts in your phone. Malicious apps may try to collect phone numbers and emails from your contacts, which could then be used as targets for phishing scams or other attacks.
Contacts — This permission set gives apps the power to create, edit, store, and delete contacts in your phone. Malicious apps may try to collect phone numbers and emails from your contacts, which could then be used as targets for phishing scams or other attacks.
 Location — These permissions manage a phone’s GPS and Wi-Fi hotspots. If misused, they can tell a cybercriminal where you are and track your motion.
Location — These permissions manage a phone’s GPS and Wi-Fi hotspots. If misused, they can tell a cybercriminal where you are and track your motion.
 Microphone — These permissions let an app use the device’s microphone to record audio. If bad actors get in, they’d be able to turn on the microphone even when you’re not using it, record audio, and send it to their creators.
Microphone — These permissions let an app use the device’s microphone to record audio. If bad actors get in, they’d be able to turn on the microphone even when you’re not using it, record audio, and send it to their creators.
 Phone — This set of permissions let an app access your phone number, your cell network info, call status, voicemail, VoIP, read and edit calling logs, and even redirect calls to another number. Malware, if given this permission, could spy on your phone usage behavior and even make calls without your approval.
Phone — This set of permissions let an app access your phone number, your cell network info, call status, voicemail, VoIP, read and edit calling logs, and even redirect calls to another number. Malware, if given this permission, could spy on your phone usage behavior and even make calls without your approval.
 SMS — These permissions allow an app to read, receive, and send SMS, as well as receive WAP push-messages and MMS messages. Malicious apps are known not only to spy on existing messages, but also to use your phone to send out spam and subscribe your phone to unwanted paid services.
SMS — These permissions allow an app to read, receive, and send SMS, as well as receive WAP push-messages and MMS messages. Malicious apps are known not only to spy on existing messages, but also to use your phone to send out spam and subscribe your phone to unwanted paid services.
 Storage — These manage the device’s internal and external storage. Malware with this permission can read, write, and edit documents, photos, music, and other files on your phone.
Storage — These manage the device’s internal and external storage. Malware with this permission can read, write, and edit documents, photos, music, and other files on your phone.
Administrative and root privileges
Besides the regular permissions you will be faced with, there are two deeper levels to understand.
Device administrator privileges
These allow you or an app to make changes to a device at the system level. This includes editing a password, locking the phone up, and even wiping all the data off of it. Admin privilege is used by security apps such as Avast Mobile Security for Android to remotely lock up or wipe your device, should it be stolen. Of course, should a malicious app get the same privilege, it could totally compromise your phone.
Device root privileges
The highest level of privileges known to Android. Root privileges give a user access to the device’s most basic functionality, and whosoever has it can do whatever he/she/it wants. While these are disabled by default, cybercriminals are known to be working on a way in. For instance, a puzzle game called “Colorblock,” found in the Google Play Store, turned out to be a rooting Trojan horse.
How to check an app’s permission request
While Android will display the permissions required before installing an app, there are several other ways you can find that out.
Seeing app permissions before installation
Firstly, each app’s page in the Play Store has a list of the required permissions. Scroll down to Developer Info and tap on Permission Details to see which permissions the app requires.
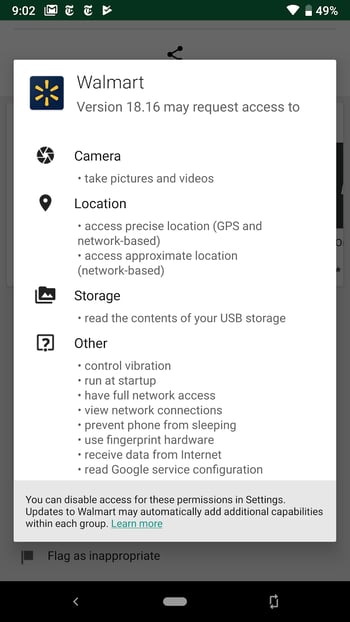
Managing app permissions after installation
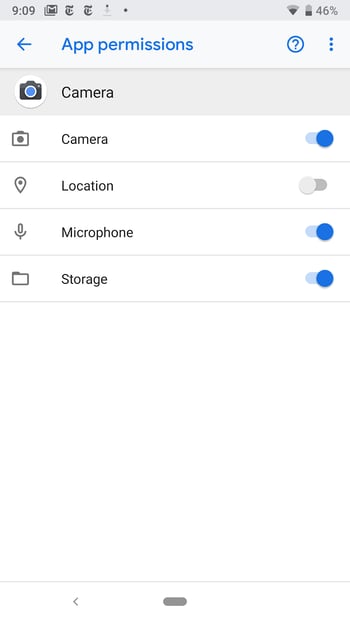
As stated before, now you can both see and manage an app’s permission after installation in Android. Go to Settings > Apps > Downloaded Apps > [the app you want to check] > Permissions. You can manually turn a permission on or off from here.
Managing Multiple Apps Using the Same Permissions
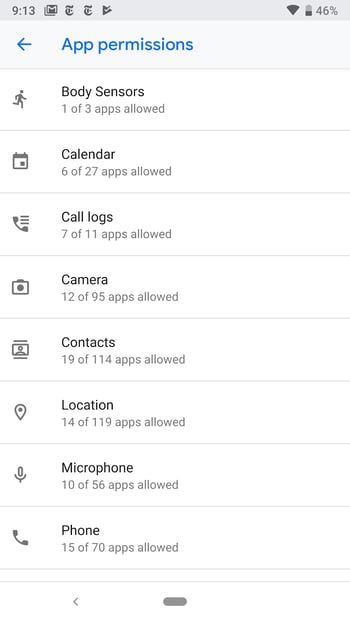
Android has a specific screen for each permission, which allows you to check which apps use which permissions. Go to Settings > Apps > [gear icon at top] > App permissions.
What’s with the two permissions I get during installation?
Often during an app installation, you will see the same permission request twice. The first one is the app letting you know it needs that permission, while the second one comes from Android, asking you to actually give the permission. Only if you allow the second permission will the app gain access to it.
Take permissions seriously
There are two components to security — the technical and the human. The technical component is your automated cybersecurity software — your antivirus, firewalls, etc. These protect your device by spotting malware and blocking it.
The human component all rests with the user. As the user of the smartphone, it is on you to oversee the power you grant other apps and software. Be aware. Be permissions woke.
If you end up granting malware the permission to access your device, there is precious little any security measure can do to avert disaster. Ultimately, it’s in your hands.
Always take the time to read through the permissions you are about to give. It may seem like a nuisance at first, but it fills you with the knowledge you need to ensure your device remains safe.