Now that 2018 is underway, the Avast Threat Labs takes note of what’s trending in cybercrime.
Cyberattacks are continuing to increase in number and severity every year, and 2018 will be no exception. We believe that many of the threats we observed in 2017 will, unfortunately, appear in evolved forms this year to continue threatening our businesses, personal data, and privacy via attacks on our PCs, smartphones and IoT devices. After all, as trends in politics, society, and technology evolve, so does cybercrime.

But if knowledge is power, then we have the insight and the might to fend off the most likely attacks headed our way in the new year, especially the nine we predict below.
1. Machine learning attacks
The use of machine learning technology by antivirus companies has become commonplace in recent years, and the bad guys are starting to take note. At first machine learning was mainly used by universities and large corporations, but things have changed. There are now more than 15 open source machine learning frameworks publicly available and being widely used. The price of powerful hardware (using GPU acceleration) dropped significantly, opening the door for the bad guys to use the opportunity to start using machine learning to circumvent a security company’s machine learning algorithms--essentially fighting fire with fire.
In 2018, we believe cybercriminals will attempt to find the blind spots in machine learning detection systems and start to poison machine learning systems. They will also leverage AI tools not only to launch malware attacks, but also to perform highly sophisticated spearphishing attacks—for example, by creating a fake “intelligent” persona that can give people the feeling they are communicating with somebody they know, to trick them into sharing personal details.
2. Ransomware as a weapon
In the past, ransomware has been used by cybercriminals solely for financial gain, but in 2017 we saw several major attacks where the purpose was not entirely clear. There were signs that these could have been deployed to cover up nation-state attacks or used to commit industry espionage. WannaCry and Petya were two ransomware attacks that spread across the world. They have many similarities, the most notable being that they all used ransomware that was flawed, poorly coded and recovering files was impossible in some cases. This leads us to believe that the real intention might not have been to collect money, but instead to infect the computers to launch another campaign, e.g. to spy on users.
 Avast has blocked more than 122M WannaCry attacks in 194 countries since its outbreak in Spring 2017.
Avast has blocked more than 122M WannaCry attacks in 194 countries since its outbreak in Spring 2017.
In 2018 we expect attackers will continue to use ransomware to conceal spying activities. If attackers continue to use newly discovered vulnerabilities for worm-like spreading of their malicious software, fighting ransomware will remain a significant challenge around the world.
3. The weakest link: IoT devices
In 2018 we expect to see further abuse of vulnerable IoT devices to create and use botnets to attack servers and steal users’ personal information. This happens when a cybercriminal gets in and hijacks the IoT device, using it in a botnet. While IoT devices performing tasks as a botnet may not seem critical to an individual who may not even realize their webcam or router has been hijacked, the results can be devastating. We predict these botnet attacks will be used to disrupt smart city life, targeting people’s personal data stored or transferred via IoT devices, and taking smart home devices for ransom. There isn’t much stopping cybercriminals from taking these attacks to the next level.
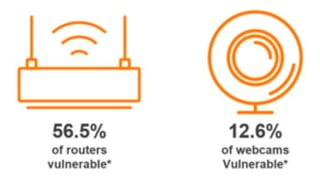 Avast research March 2017 - Check of more than 1.8M home networks in the US
Avast research March 2017 - Check of more than 1.8M home networks in the US
4. Cybercriminals jumping on the cryptocurrency bandwagon
Cryptocurrencies are currently a big trend, and it’s no surprise that cybercriminals want to become rich by taking advantage of digital currencies. We expect they will continue spreading cryptomining malware, stealing coins, and using phishing attacks and fake cryptocurrency investment, wallets, and exchange scams to get their hands on cryptocurrencies and people’s money.
5. Next up: Blockchain
Blockchain is mainly used to keep record of cryptocurrency transactions. In 2018, we might see the use of blockchain to expand to document other types of records, like digital identity management or voting. The more blockchain is used to safeguard valuable records, the more we will see cybercriminals attack services built on blockchain. For example, the year already kicked off with a newly detected vulnerability in the Electrum wallet, discovered by security researcher Tavis Ormandy.
6. A shift in attack vectors—the emergence of high-profile supply chain attacks
Cybercriminals are always on the lookout for new ways of making or obtaining sensitive information. They react to new security technologies, constantly trying to find ways of circumventing new innovations. One threat growing in prevalence in 2017 was the supply chain attack, where attackers inject malicious code into a component such as a library or code snippet of a legitimate, open-source or commercial application. As users install or update the affected applications, they also infect their systems with the malicious payload. We expect to see these attacks increase on a much larger scale in 2018, as traditional means of spreading malware are expensive and more difficult for cybercriminials given the recent innovations in the security industry. We may even see attackers using supply-chain attacks for cyberespionage and nation-state activities.
7. Going fileless
In 2018, we will see more attacks using fileless malware, which resides in a computer’s RAM and does not install anything on the victim’s machine. This, in addition to using Windows tools like Powershell to execute, allows fileless malware to better circumvent antivirus protection, as well as diminishing the amount of traces it leaves behind. This makes it an attractive tool for cybercriminals. Fileless malware can also move laterally to infect further machines within a network, making attacking an entire network easier.
8. Data breaches part X
Data breaches have become the leading risk to data and privacy for the past 10 years and it is showing no signs of slowing down. Compromised data can be used by cybercriminals to perform various types of attacks, even years later. They use stolen login credentials to steal data and money. An existing trend that can facilitate data breaches, if not properly secured, is Software as a Service (SaaS). While SaaS is very popular among businesses, poorly secured data stored on the side of the service provider can instantly leave the business using the service and their data vulnerable. Data breaches will continue in 2018, and more data could be compromised by way of SaaS weaknesses.
9. A rise in mobile threats
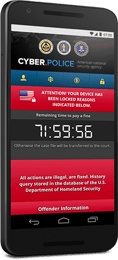 As we live so much of our digital life on our phones, it’s no surprise that cybercriminals want to compromise them. Our banking info, credit card details, precious photos, and critical emails are just a password away, and cybercriminals want in. Downloaders posed the biggest threats for smartphone users in 2017, and we predict they will continue to persist throughout the next year. We also expect to see an increase in mobile banking threats, mobile ransomware, and fake apps in 2018.
As we live so much of our digital life on our phones, it’s no surprise that cybercriminals want to compromise them. Our banking info, credit card details, precious photos, and critical emails are just a password away, and cybercriminals want in. Downloaders posed the biggest threats for smartphone users in 2017, and we predict they will continue to persist throughout the next year. We also expect to see an increase in mobile banking threats, mobile ransomware, and fake apps in 2018.
At Avast, we are constantly enhancing our threat detection and blocking technologies, and in 2018, we will continue to innovate and stay true to our mission of being the guardians of the digital world. Learn more about all the threats mentioned above by reading our full report of the 2018 threat landscape.