Cryptocurrency mining malware, which also installs a malicious Chrome extension, hosted on GitHub for anyone to download.
Cybercriminals are aggressively uploading cryptocurrency mining malware to GitHub. The cybercriminals fork other projects, which on Github means producing a copy of someone else’s project, to build upon the project or to use as a starting point and subsequently push a new commit with the malware to the project. The projects which have been forked appear to be chosen at random. A list of affected GitHub repositories can be found at the bottom of this blog post.
The cybercriminals behind the malware are hiding malicious executables in the directory structure of the forked projects. People are tricked into downloading the malware through phishing ads shown on online gaming and adult websites, warning users that their Flash Player is outdated, for example, as well as through a fake adult content gaming site. In addition to mining, the malware also installs a malicious Chrome extension, to inject fake ads and to click on ads in the background, allowing the greedy cybercriminals can make even more profit.
Infection vector
Users don’t need to download the malicious executables directly from GitHub. Instead, the malware is spread via a phishing ad campaign. When a user visits a site that displays the phishing ads and clicks on an ad, the executable downloads.
The ads first lead to an attacker-controlled server (http://binqg.xyz/direct.php?sub3=25-114-201802141754224cef0ad22&f=setup_sex_game.exe), which then redirects to the GitHub repository hosting the malware, which is where the malicious executable is loaded from.
In addition to the phishing ad campaign, we found an adult content site spreading the malware by offering site visitors a sex game.
In this animation you can see how the webpage serves the malicious file right after the page is visited. If the user clicks through the page, it offers the same file again, after the user clicks on 'I'M OVER 18 YEARS OLD - LET'S PLAY - DOWNLOAD'.
A closer look at the actual malware
The malware incorporates a Monero miner that is also hosted on GitHub The cybercriminals added malicious functionalities to the miner. One of the functionalities includes terminating Opera, Chrome, and Amigo Free Browser processes. We aren’t sure why Opera and Amigo Free Browser processes are terminated, as the malware targets Chrome users. We suspect this is a bug or maybe the cybercriminals are planning on launching a version of the malware that will also target these browsers.
The first thing the malware does is copy itself to “C:\ProgramData\VsTelemetry\vshub.exe”.
Newer samples of the malware use this path: “C:\ProgramData\WindowsPerformanceRecorder\spyxx_amd64.exe”
Next, it schedules two tasks:
“schtasks /create /tn \SystemLoadCheck /tr "C:\ProgramData\VsTelemetry\vshub.exe -loadcheck" /st 00:00 /sc daily /du 9999:59 /ri 10 /f”
The first task installs a Chrome extension that injects JavaScript into every opened page. The task also loads the malware on a daily basis, every midnight and is set to never end and is set to repeat itself every 10 minutes, unless the process is already running. Even if the infected computer is rebooted, the malware reloads. If the process is terminated by the user, the task schedules it to restart 10 minutes after.
“schtasks /create /tn \Windows\VsServiceCheck /tr "C:\ProgramData\VsTelemetry\vshub.exe" /st 00:00 /sc daily /du 9999:59 /ri 2 /f”
The second task has the process restart two minutes after the process has been terminated.
The second task mines with the following options:
“-o stratum+tcp://vwwvvw.com:3333 -u 39VwaJXhVdJ7pd5XR8D8wubdFfE4dxkDaM -p x -k -cpu-priority=1 -max-cpu-usage=50 -donate-level=1”
The options above are explained on this GitHub page:
-o, --url=URL URL of mining server -u, --user=USERNAME username for mining server -p, --pass=PASSWORD password for mining server -k, --keepalive send keepalived for prevent timeout (need pool support) --cpu-priority set process priority (0 idle, 2 normal to 5 highest) --donate-level=N donate level, default 5% (5 minutes in 100 minutes) --max-cpu-usage=N maximum CPU usage for automatic threads mode (default 75)
A number of things are done in order to avoid user detection. The “max-cpu-usage” is set so that the malware can use a maximum of 50% of the infected computer’s CPU, so the computer doesn’t run too slow. Next the “cpu-priority” gives other processes that need higher amounts of CPU priority over the malware. This allows the victim to use their computer as usual, so the malware can go unnoticed. Another common trick used by mining malware that is also used by this malware, is that once the task manager is activated, the malware stops mining to avoid being caught.
The malicious Chrome extension
The malware also installs a malicious Chrome extension to Chrome browsers, which is where things get interesting. The malware exploits an old version of the AdBlock Chrome extension, which Chrome loads as if it were the real deal. As mentioned earlier, the malware terminates all Chrome processes. This is done, to trick the victim into re-starting Chrome, activating the new extension. Even if the user visits the Chrome extensions page, rather than seeing their extensions, they see the extensions page, including the malicious extension, for a split second, before the page redirects to another page. This prevents users from removing the malicious extension.
Above is an animation we created to show the redirect process, which in reality is 10 times faster (we slowed it down when creating the animation), that essentially prevents users from removing the malicious extension.
The following files are installed to the Chrome extensions folder:Extensions\gighmmpiobklfepjocnamgkkbiglidom\449_0\_metadata\computed_hashes.jsonExtensions\gighmmpiobklfepjocnamgkkbiglidom\449_0\_metadata\verified_contents.jsonExtensions\gighmmpiobklfepjocnamgkkbiglidom\449_0\icon128.pngExtensions\gighmmpiobklfepjocnamgkkbiglidom\449_0\manifest.jsonExtensions\gighmmpiobklfepjocnamgkkbiglidom\449_0\contentscript.js
The last extension file includes a malicious script, contentscript.js, which is loaded by Chrome thinking that it is loading the AdBlock extension.
Obfuscated version of contentscript.js
In the unobfuscated version of contentscript.js above, we can see that the malware is targeting Google and Yahoo searches.
What’s interesting is that Google Chrome loads this plugin without any problems, on the other hand, when someone wants to load a custom Chrome extension, they have to enable the so called “Developer mode” in order to run the extension.
Once the malicious script runs, it’s business as usual:
The malicious script from the extension injects ads into victims’ Google and Yahoo search results, to make money from clicks.
The search terms entered by victims on Google and Yahoo are leaked to a non-Google and non-Yahoo website. This is most likely done to better target them with ads.
Stathat.com and yandex.ru pages are visited by the browser in the background. The pages can include ads, which means the cybercriminals could also be receiving revenue shares from the clicks.
The malicious extension can be removed by uninstalling Chrome and deleting user data when uninstalling.
Signed Certificates
The cybercriminals were smart enough to digitally sign the mining malware executable, because once it’s digitally signed, it magically becomes clean, right? RIGHT?! Wrong. Very wrong. Sorry cybercriminals.
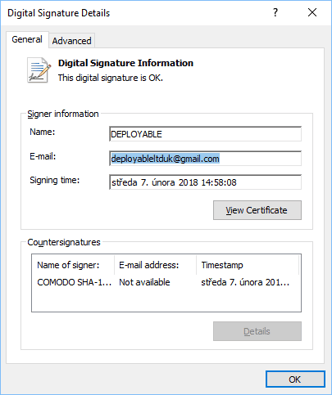
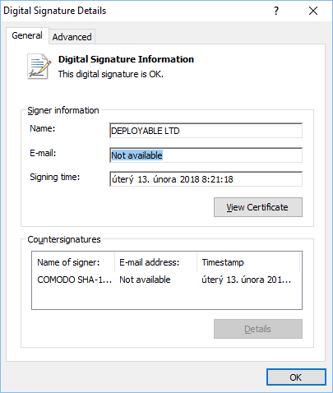
By signing the executables, the cybercriminals actually made our job of detecting this malware as malicious much easier, which was probably not what they were trying to achieve. Our machines automatically mark all files with the certificates in the screenshot above, as malware.
The cybercriminals didn’t seem to be happy about us detecting their certificates as malicious. In some cases, we noticed clean files signed with their certificate uploaded to the GitHub repositories. We suspect this was their way of trying to get us to falsely detect clean files as malicious.
Nice try.
Russian speakers likely behind the malware
The authors behind the malware probably speak Russian, or expect their victims to be Russian speaking
The first clue that suggests the authors are targeting the Russian market or are Russian, is that the function “SetThreadLocale” is called with the Locale argument set to 1049, which is the code for the Russian locale.
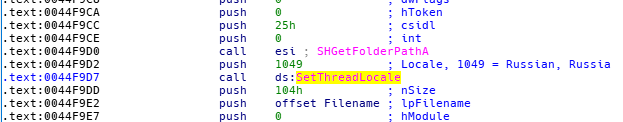
The function SetThreadLocale is called with the Locale argument set to 1049 which stands for the Russian locale.
The second clue that makes us think the cybercriminals behind this malware are either Russian or targeting Russians, is that the malware checks the following path when it tries to inject a browser extension: “\Хром\User Data\Default\”. “Хром” stands for “Chrome” in Russian. The code set to the Russian locale lets Windows know the text encoding used by the program, allowing the program to properly decode bytes D5 F0 EE EC into “Хром”.
Another clue was found in the the git commit log where all commits were done in the UTC+03:00 timezone (Moscow Time), which can be seen in the screenshot below
Benefits to hosting malware on Github
Hosting malware on GitHub is unusual, but we have to admit, we see some of its benefits. The malware is hosted for free, on a reliable platform with unlimited bandwidth. The version history is available for malware researchers, like us, to view and on top of that, we can see the malware in real-time. Thank you very much!
An update on GitHub, showing that three files had changed
Updates made to the malware on GitHub
Bitly stats:
The cybercriminals behind this campaign cleverly shortened the links visited by the malware, using Bitly:
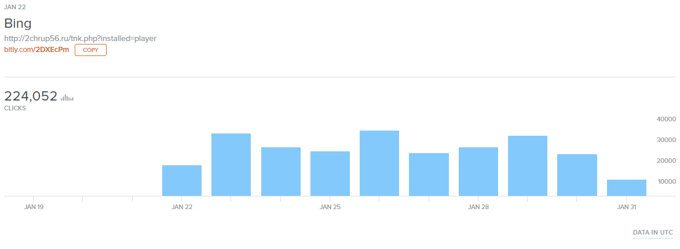
Yay, free stats for everyone!
Avast stats:
From our backend systems, we can see how many Avast users we protected from downloading the malware:
Conclusion
The malware is still live and being hosted on GitHub. GitHub has removed many forked projects hosting the malware, but the cybercriminals are very determined and continuously upload the malware on GitHub again and again. We are working together with GitHub, supplying them with new repositories containing the malware, which GitHub is removing.
As for the malicious Chrome extension, we have reached out to Google, notifying them of the extension. At the time of publishing this post, the extension has not been blocked by Google. Users infected can uninstall Chrome, selecting “delete browser data” in order to remove malicious extension.
We aren’t sure how much the cybercriminals behind this campaign have earned through the malicious extension and the mining malware. We tried looking up their Monero account balance, but sadly, Monero said “no!”:
Avast detects and protects its users from this malware.
How to protect yourself from malware
- Use antivirus, which will act as a safety net and protect you, should you ever accidentally fall for phishing scams, like the one described above.
- Be suspicious of offers that seem a bit off, like games and software updates that appear while browsing the web, especially if they appear on somewhat shady sites.
- Visit software sites or trusted download portals directly to download software or update software from within the software itself.
- Only use official repositories or trusted forks on GitHub, don’t blindly compile or execute sources from GitHub.
SHA256:
3F108915B8B76AB97BA1DF218D9D5DAEA6E8D9FF0A66228855777A75C125C518
8D1F269D0991513E3F471CDE239EA1C101FE44E92331CF3DF977B4937C7AA9B8
AEB1E544B8B7EC5A742C42F2C2FC35E67F14E9A5004F45A7DD2C3F89BFCD13C2
628718571F843F61A5911A102737C3E199C3DF7D1A27CD57D5E87B2869927612
0C8258768E1218CB8C6416BC32EBABF187B8A0306178D314FD7F36587752C380
343A4FEE8A3EC8B1D38BBCA137FDC76EE98E5A52CDC84E6107806EEAD95657FB
72A8325E27B88863DD57AF41816A032EF0BAE3CFCB1854F2EC0D0C7A198276C9
01E023FB753B32073FFCDF7F320F2B582B2F9DCBBB76171C514A79F2B42CF732
51F89E3E19261FC1BFE1A4B1ECFA5C9CC4029D741C66D74629205FAA41C57265
57353DF34D61AE3E8855E6F3F725AAF2FCC9609FDDFFD2ABEDADDD3D0695C56B
bit.ly addresses
bit.ly/2Bez5ee
bit.ly/2DXEcPm
bit.ly/2mrr5gZ
bit.ly/2n8aKhi
bit.ly/redir3352
List of abused GitHub repositories:
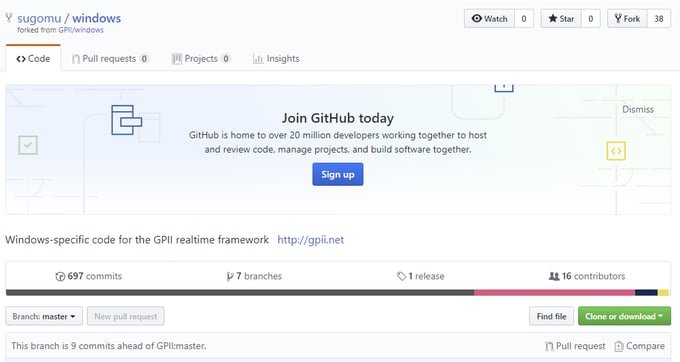
GitHub project (one of) malicious fileszopihafo/smppclientSMPP\SmppClient\flashupdate.exesugomu/windowslisteners/setup_sex_game_xp.exebuwewevew/yelp-apiv2/objective-c/flash_update_xp.execilmenupse/downtimetest/file/flash_update_xp.exedizovoz/rui2flash_update_xp.exegitoruma/proflash_update_xp.exeikpt/Exflash_update_xp.exenotdude/lemonaiddiagrams/setup_sex_game.execogocoze/resbin/setup_sex_game.exesloup0k/sloup0ksloup0k/sloup0k setup_sex_game.exesojujelin/profilegit/setup_sex_game.exeuxm1rk/gameaxns/exmoetc/setup_sex_game.exezb97/zb97SexGame.exeyogalix/localturkmaster/sample/sexGame.exenarexo/ggtest/sex_game.exedsdf4sf/olosex_game.exezijama/pullreqsbin/sexgame.exenufosaka/relicsex_game_18.exemewoko2/mewoko2sexgame.exeavui/opomnikiprintscr/sexgame.exehevicevog/zingersex_game_a.exesolgoodman/ivankasex_game_a.exebendjamin8/bendjamin101001.github.ioarchives/2018/02/sex_game_a.exe
List of malicious urls:
101games.xyz
2chrup56.ru
adobe.flashplayer.bx6tok.xyz
adobe.flashplayer.mp2pzq.xyz
adobeflashplayer.ki1ahb.xyz
adobeflashplayer.ma8cfl.xyz
adobeflashplayerb.xyz
adobeflashplayerc.xyz
adobeflashplayerq.xyz
adobflashplayerx.xyz
affshopcj.com
am9ozs.xyz
best-game.xyz
biggame1.xyz
binary-flash.xyz
binqg.xyz
bitly.wa4eri.xyz
chr0xy.xyz
flash-player.xyz
flash-update.akva-komptlt.ru
flash.or5sgw.xyz
flash.vtb-karta.ru
flashplayer-adobe64.xyz
flashplayer-win10.xyz
flashplayer.chickenkiller.com
flashplayer.chrm1.xyz
flashplayer.nb6ret.xyz
flashplayer.oi1ljg.xyz
flashplayerb.xyz
flashplayerd-4.com
flashplayerdownloadvip.com
flashplayeru.xyz
flashplayerv.xyz
flashplayupdate.xyz
go.seoclubs.pw
in-games.xyz
isb2.xyz
ki1ahb.xyz
mnmnnm.com
mp2pzq.xyz
needgames.xyz
online-game-18.xyz
qs3gas.xyz
red1r.xyz
red1r2.xyz
rp5jxi.xyz
s-games.xyz
sb1xju.xyz
setup-game.xyz
ui2ulh.xyz
update-flash-win64.xyz
updateflash.pb6xny.xyz
updateflash.xyz
ush1.xyz
win-flash.xyz
win64-flash.xyz
win64-flash.xyz
win7flash.xyz
worldonsearch.com
flashplayerd-4.com
online-game-18.xyz
xg3s.xyz