Locking down school environments is virtually impossible with BYOD and BYOA, so school administrators need best practices to secure their students and staff.
With schools opening their doors for a new academic year, administrators need to pay particular attention to best practices for securing their faculty, students, and staff and processes and technology, particularly when Bring Your Own Device/Bring Your Own Application (BYOD/BYOA) means completely locking down school environments is virtually impossible.
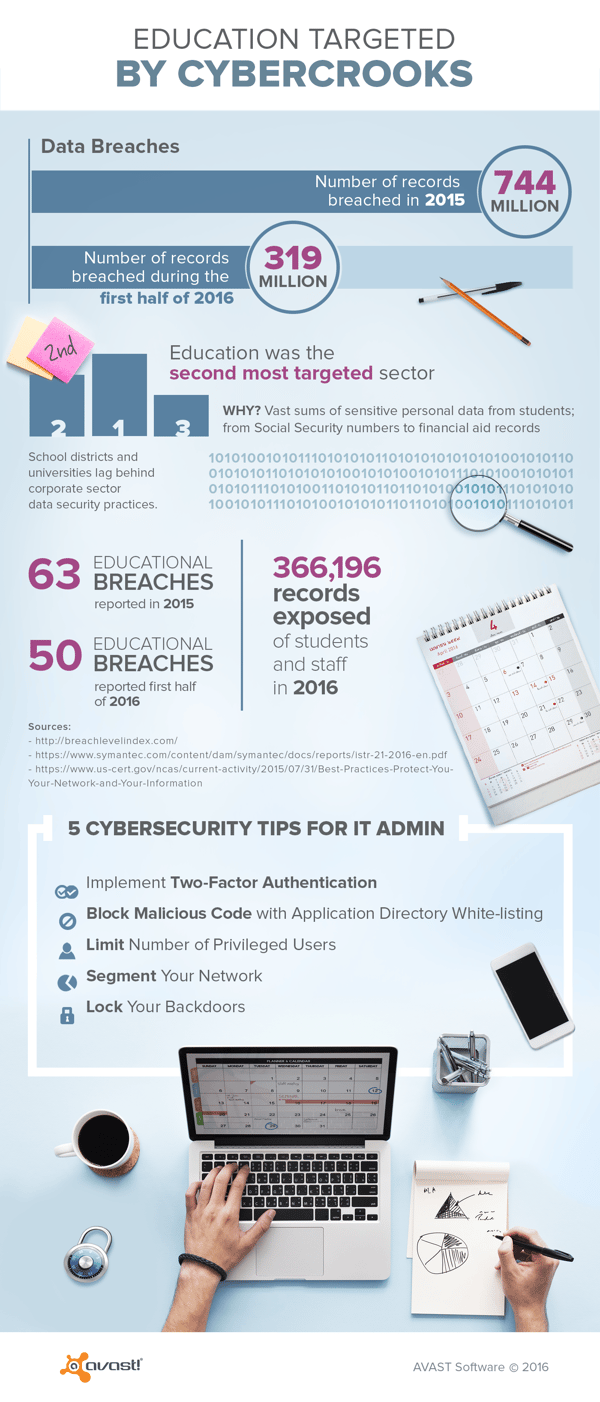
Viruses, malware, botnets, ransomware, denial of service attacks, APTs and worms: the list of real and potential threats is long, and growing. There were 744 million records breached, as a result of cybercrime, reported in 2015, and almost 320 million for the first half of 2016. Given that it can take organizations up to 6 months or more to identify a data breach, it's expected that we'll see a lot more breaches as the year progresses.
Educational institutions are not immune to cyberattacks, inadvertent or deliberate. In fact, the numbers would indicate that attacks on schools are on the rise. For the first half of 2016 education was the second-most targeted sector, up from third place in 2015. Additionally, more than 50 educational breaches were reported in the first half of 2016, exposing as many as 366,196 records of students and staff. This is compared to a total of 63 educational breaches in all of 2015.
Administering cybersecurity involves a number of responsibilities, including setting policy and procedures, providing training and support to users and staff, protecting systems against unauthorized access and alterations, and preparing backup and recovery capabilities.
The other, perhaps the major, consideration, is that security is a 24-7 exercise. New threats and problems are constantly emerging, and the optimal cybersecurity solution(s) must work around the clock, all year round, and be able to respond immediately to new attacks as they occur, with frequent and automatic updates.
Education is a unique environment
In and of itself, a school is a much different place than any other workplace, specifically for cybersecurity. When you bring together teachers, students, and administrators, there are a lot of moving pieces and endpoints to protect. Mix in BYOD/BYOA, and you have a scenario in which anybody can have any data on any device – desktop, notebook, tablet, or smartphone, even a USB stick. Obviously, this can cause major issues when trying to secure the environment.
The ability to police – and troubleshoot – endpoint devices is essential. For example, Web-based consoles can enable secure access to laptops and computers throughout a school's network quickly and with minimal resources, and mitigate problems remotely, instead of wasting time and resources to resolve issues one-by-one on-site.
The following are five cybersecurity best practices recommended by National Cybersecurity and Communications Integration Center (NCCIC):
- Implement two-factor authentication. Two-factor authentication works to significantly reduce or eliminate unauthorized access to your networks and information.
- Block malicious code. Activate application directory whitelisting to prevent non-approved applications from being installed on your network.
- Limit number of privileged users. System administrators have privileged access that gives them the “keys to your kingdom.” Limit system administrator privileges only to those who have a legitimate need as defined by your management directives.
- Segment your network. Don’t put all your eggs in one basket by having a “flat network”. Use segmentation techniques so that if one part of your network is breached that the integrity of the rest of the network is protected.
- Lock your backdoors. Third parties that share network trust relationships with you may prove to be an Achilles heel by serving as an attack vector into your network. Take action to ensure that all network trust relationships are well-protected using best practices. Have a means to audit the effectiveness of these defenses. Consider terminating or suspending these relationships until sufficient controls are in place to protect your backdoors.