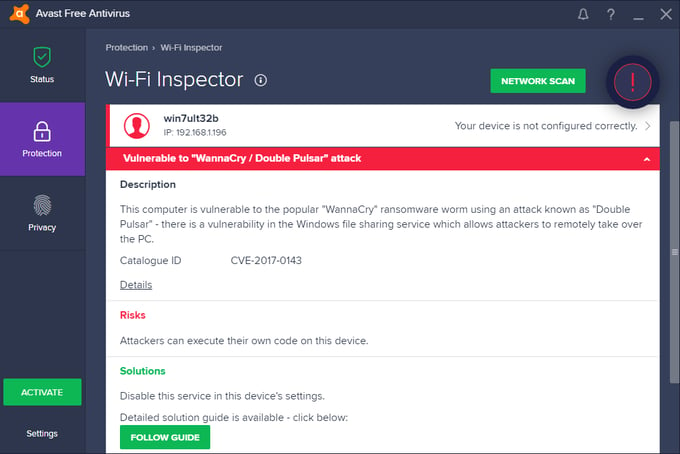
Avast Wi-Fi Inspector scan alerts users if their PC or another PC on their network is vulnerable to being exploited by WannaCry or Adylkuzz.
Blog post and research by Pavel Sramek, David Jursa, and Lukas Rypacek
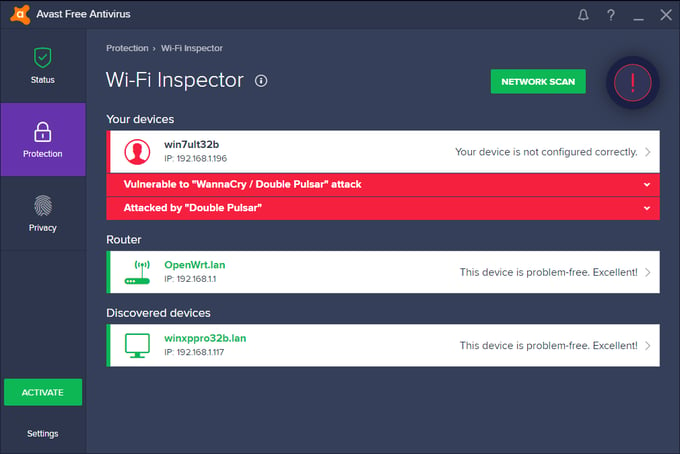
Scanning a PC using Avast Wi-Fi Inspector can reveal if the PC is vulnerable, has been infected via an exploit, or if a PC within the network is infected, regardless if that PC has Avast installed or not.
The recent WannaCry and Adylkuzz outbreaks were made possible by an exploit known as EternalBlue. The exploit takes advantage of the MS17-010 vulnerability in the Windows File and Printer Sharing feature (SMB protocol implementation). WannaCry and Adylkuzz targeted anyone that didn’t install the patch for the vulnerability, which Microsoft released in March.
Windows XP users were especially vulnerable to the attack, asfor the operating system in 2014, leaving them patchless, until Microsoft released an out-of-bound patch for older operating systems.
Many of the world’s Windows PCs are still vulnerable
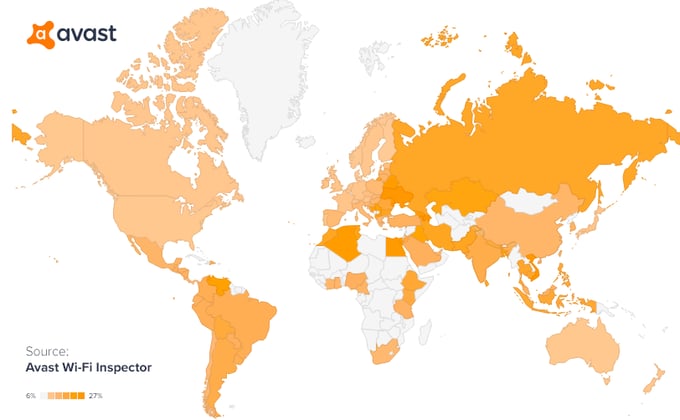
Data from Avast Wi-Fi Inspector scans (from May 8th - May 18th) show that PCs around the world are still running with the EternalBlue vulnerability (see map above). Since last Friday, the number of PCs with the vulnerability has decreased, but there are still a lot of PCs out there that are vulnerable. Computers with the EternalBlue vulnerability are in danger of being infected with malware, like WannaCry ransomware and Adylkuzz.
Here is a breakdown of the global average over the last weeks of the vulnerability’s presence on different Windows operating systems:
- Windows XP: 74.23%
- Windows Vista: 68.11 %
- Windows 7: 54.84%
- Windows 8: 21.89%
- Windows 10: 4.22%
What are EternalBlue and DoublePulsar?
EternalBlue refers to a critical bug in Microsoft’s Windows code that is at least as old as Windows XP. The bug allows attackers to execute code remotely by crafting a request to the Windows File and Printer Sharing request. The bug, or exploit, was likely discovered by the NSA, who gave it the name “EternalBlue” and kept it secret. Since it was disclosed to Microsoft, the vulnerability is also known by its CVE ID, CVE-2017-0143.
The NSA created a backdoor tool to exploit EternalBlue, with the intention to keep PCs "tapped" and to check on them from time to time, but leave no trace of doing so on the systems. With DoublePulsar, which our data from Avast Wi-Fi Inspector scans shows is present on 22,814 PCs visible to us, attackers can infect a PC that has the EternalBlue vulnerability over the network the PC is connected to. No user action is needed for a PC to become infected; the device just has to have the File and Print Sharing feature enabled and be connected to a network. DoublePulsar sits on the infected PC and listens for commands from basically anyone who accesses it and can download and execute any spying tool or malware it is commanded to run.
You can think of the bug in the File and Print Sharing protocol like a mistake in a door’s design, which causes there to be a gap between the door and the door frame. This door is installed in millions of homes around the world. The mistake makes homes vulnerable. The exploit (EternalBlue) is the crowbar that fits in the gap and can pry the door open. The backdoor (DoublePulsar), is a door stop that can be wedged in the gap, while prying it open, to keep the door open indefinitely. This allows any outsider to open the doors and gain access to the homes.
DoublePulsar and EternalBlue were leaked out from the NSA on April 17th, 2017. Prior to that, in March, Microsoft issued a security advisory (MS17-010) and a patch, which closes the EternalBlue vulnerability.
Last Friday, May 12th, 2017, the WannaCry ransomware, spreading as a worm, made its rounds using EternalBlue and DoublePulsar to rapidly spread around the world
What should you do?
To find out if your PC is vulnerable, download Avast (if you don’t use it already) and run the Avast Wi-Fi Inspector scan. To do so, open your Avast Antivirus, click on “Protection”, then “Wi-Fi Inspector” and click on “Network Scan” to run the scan.
If the scan shows your PC or another PC on your network (even PCs that don’t have Avast installed on them) as “Vulnerable to ‘WannaCry / DoublePulsar’”, click the “Follow Guide” button or visit the Avast help center for a step-by-step guide on how to patch Windows, to fix the vulnerability.