Avast update on WannaCry: who was affected, who was targeted, how to remove it, and more.
While last Friday wasn’t Friday the 13th, it sure seemed like it. PCs around the world, including those belonging to hospitals and government agencies, were hit by the WannaCry (AKA WanaCrypt0r, or WCry) ransomware, causing chaos. Up until now we have seen more than 250,000 detections in 116 countries. What this means is that more than 250,000 Avast users had encountered the ransomware but were protected as Avast blocked the ransomware from infecting PCs. As the situation settles, we can conclude that this was the worst ransomware outbreak in history.
Through our Avast Wi-Fi Inspector feature, which users can use to scan their systems for vulnerabilities, we see that approximately 15% of users haven't patched the MS17-010 vulnerability, which would have made them vulnerable to this attack if they didn't have Avast protecting them. This number is a result of data we monitored the past six days, and the actual percentage number of PCs vulnerable could be much higher.
By Friday afternoon we had seen more than 50,000 detections of the ransomware within the Avast user base. Shortly after Friday, around midnight, the number of detections grew to more than 100,000.
Where WannaCry wandered
Below is a chart showing when the detections peaked and dropped.
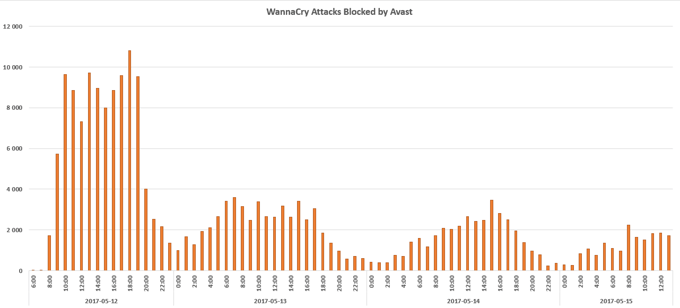
We detect all WannaCry components, not only the variants that include the worm component, but also those that simply encrypt the files and don't spread any further. The worm component determines how WannaCry is spread, which we describe below. Some researchers say the spreading is over, but this is only true for the WannaCry variant that previously spread like a worm.
We observed 10,000 detections per hour shortly after the outbreak, which is a really high number for a single malware strain.
After a malware researcher pressed the kill switch, which we will describe later in this post, the number of detections significantly decreased to approximately 2,000 per hour, late Friday afternoon. The ratio has been decreasing since then and we hope that this trend will continue.
The top 10 targeted countries, according to our data, are (in order): Russia, Ukraine, Taiwan, India, Brazil, Thailand, Romania, Philippines, Armenia, and Pakistan. More than half of the attempted attacks on our entire user base were blocked in Russia.
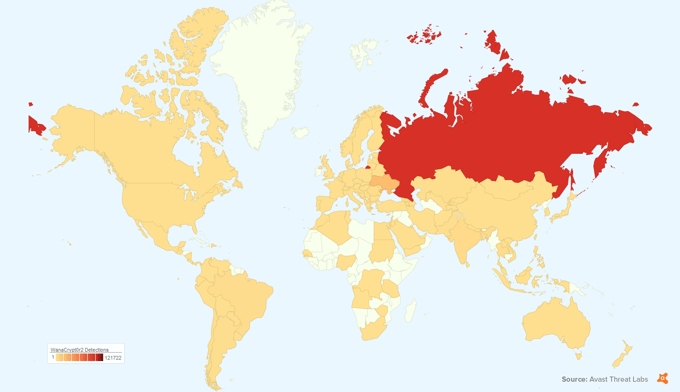
Who was WannaCry targeting?
WannaCry, like most other ransomware strains, didn’t target anyone specifically. The ransomware used an exploit known as ETERNALBLUE, which takes advantage of a Windows SMB (Server Message Block, a network file sharing protocol) vulnerability labeled as MS17-010. WannaCry thus blindly and randomly targeted anyone that didn’t install the patch for the vulnerability, which Microsoft released in March.
WannaCry spread so aggressively because every Windows computer connected to a network, with the MS17-010 vulnerability, can be infected without user interaction. The already-active malware on a PC scans both the local and sub-network and randomly choses IP addresses. Once it finds a vulnerable PC, the ransomware spreads to that PC as well, which is possible because WannaCry contains worm functionality.
Windows XP users were left helpless to the attack. Microsoft cut off support for the old operating system (OS) in 2014, so even if XP users wanted to download the patch they couldn’t. Microsoft has since released an out-of-bound patch for older operating systems.
Despite Windows XP being the most vulnerable, due to the unavailable patch before the attack happened, the majority of attempted attacks we blocked occurred on systems like Windows 7, on computers where the security update had not been installed, although it was available. We urgently encourage anyone who hasn’t yet downloaded the patch, including those using an older version of the Windows OS, to download the patch.
Large companies, like Telefonica and the Deutsche Bahn were affected by the attack, but even worse, hospitals around the world were also affected. Hospitals often lack budget to keep their systems up-to-date and were therefore hit hard on Friday, which greatly affected patient care.
Removing WannaCry
Removing WannaCry from a PC is not difficult, antivirus software should be able to remove the ransomware by quarantining the malicious files, but this does not solve the problem – the files will remain encrypted.
There's no free decryption tool available at the moment and based on our analysis, the encryption used seems to be very strong (AES-128 combined with RSA-2048). The best solution, if your PC is infected, is to recover your files from a backup, if available. You should do this on a clean machine, with all patches applied and for maximum security, you should do this offline to minimize the risk of encrypting the backup storage as well.
The Kill Switch
A researcher known on Twitter as MalwareTech, discovered a kill switch, which stopped the most prevalent variant of WannaCry from spreading any further.
The motivation behind including a kill switch is still unclear. We believe the kill switch was included in the ransomware, in case the group behind WannaCry wanted to stop it. The kill switch worked like this: If WannaCry made a request to a specific domain, www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com, (we dare you to try to memorize the domain name) and if a response was received, showing the domain is live, the malware would just exit and stop spreading. Before the kill switch was activated, the domain wasn’t registered and WannaCry therefore spread uncontrollably.
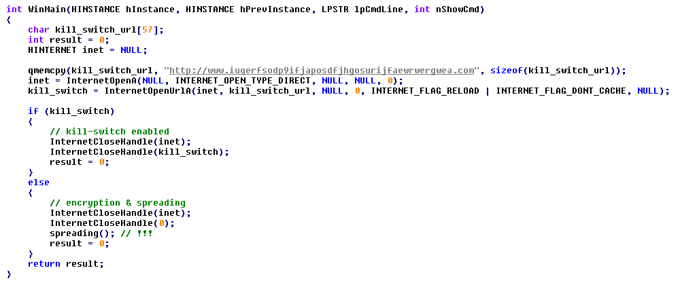
In other words, think of the kill switch like the hand-brake in your car. You can use it in emergency cases, to stop your car, but you cannot use it to control your car. The same applies to a kill switch – it can immediately stop the spreading.
It’s important to note that the kill switch only stopped one variant of WannaCry from spreading, but won’t do anyone whose PC was already infected any good. Furthermore, the inner components of WannaCry, like the file-encryption part, do not contain the worm functionality (which is what allowed it to attack so many computers) and therefore are not controlled by the kill switch and can still cause harm. So, if you encounter the ransomware itself, like from an already infected device, via a copy file on a USB stick for example, you can still become infected.
Since the kill switch has been put into effect, the spreading of WannaCry has slowed down significantly. However, we’ve noticed at least six other variants of WannaCry that contain different kill switches (i.e. URLs). We’ve even detected multiple samples where the kill switch has been removed, which means the people behind these variants want their versions to spread uncontrollably. Based on the similarities of all the variants, we think that the later versions are just modified versions of the original variant of WannaCry and have probably been modified by other groups or individuals.
How much the cybercriminals earned
The ransom demanded by WannaCry is between $300 - $600 ($300 = 0.17222 Bitcoins, as of May 16, 2017) and the demand increases over time. The threat the ransomware makes, claiming it will delete the encrypted files if the ransom isn’t paid within seven days, is fake.
We’ve been monitoring the Bitcoin payment addresses used by the group behind the attack and there have been more than 260 payment transactions, making the total money sent 41 BTC at the time of writing this blog post. That’s approximately $70,000, which is not that much considering the damage that has been caused.
However, as the countdown within WannaCry’s window is ticking, counting down the time victims have left to pay before they supposedly lose their data (which is fake, remember), we’ll likely see more payments being paid within the next day or two. We highly recommend against paying,because there’s no guarantee that your files will be decrypted, and it encourages the ransomware authors to launch more ransomware campaigns.
It looks like WannaCry, it acts like WannaCry, but it’s not WannaCry
As soon as WannaCry became “popular,” other cyber crooks started piggybacking on the trend to earn their bucks. We’ve started detecting multiple low-quality malicious applications impersonating WannaCry, such as the one in the screenshot below.
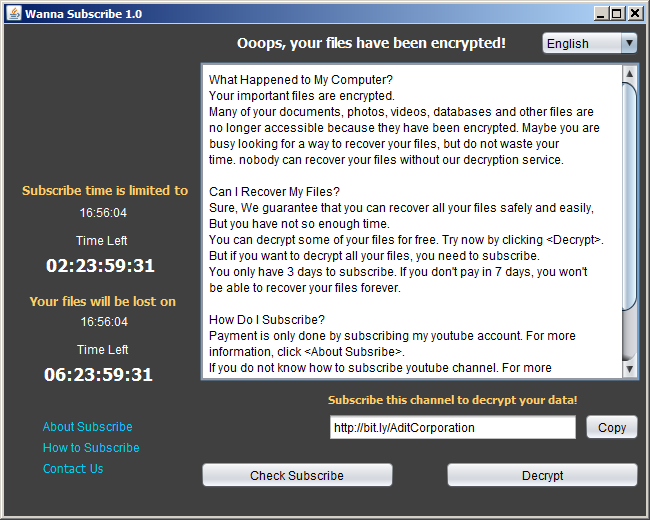
(sample source: Karsten Hahn https://twitter.com/struppigel)
Final thoughts
Back on Friday, my colleagues and I were attending the CARO workshop, a great Antivirus conference, with a talk about the recent ransomware, Spora, which is also spreading as a worm. During the workshop, we were chatting with researchers from the other companies about the latest trends and outbreaks from the last years, such as Loveletter, Blaster, or Nimda.
All the looking back suddenly ended when this Wannageddon occurred. It’s hard to describe the buzz that appeared as all of us started doing our best to deal with the outbreak. At the end of the day it was already obvious that we had just encountered the worst ransomware outbreak in history.
We’ll see what the next days will bring. There are already speculations about the origin of this attack and there are also other threats using the same infection vector.