Cybercriminals are using a copycat version of WannaCry ransomware to target Android users in China.
Avast is now detecting mobile ransomware, which we will refer to as “WannaLocker” from now on. The ransomware is targeting Chinese Android users. WannaLocker’s ransom message screen may look familiar to you and that’s because it looks just like the WannaCry ransomware screen, the ransomware that spread like wildfire around the world mid-May. Another interesting aspect is that WannaLocker encrypts files on the infected device’s external storage, something we haven’t seen since Simplocker in 2014.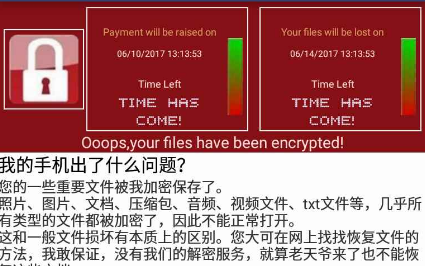
The ransomware is imitating the ransom screen shown by WannaCry.
The mobile ransomware has been spreading on Chinese game forums, imitating a plugin for the popular Chinese game King of Glory (王者荣耀), which is how victims are being tricked into downloading the ransomware.
It starts by hiding its icon from the app drawer and changing the main wallpaper to an anime image. Then, it starts encrypting files stored on the device’s external storage.
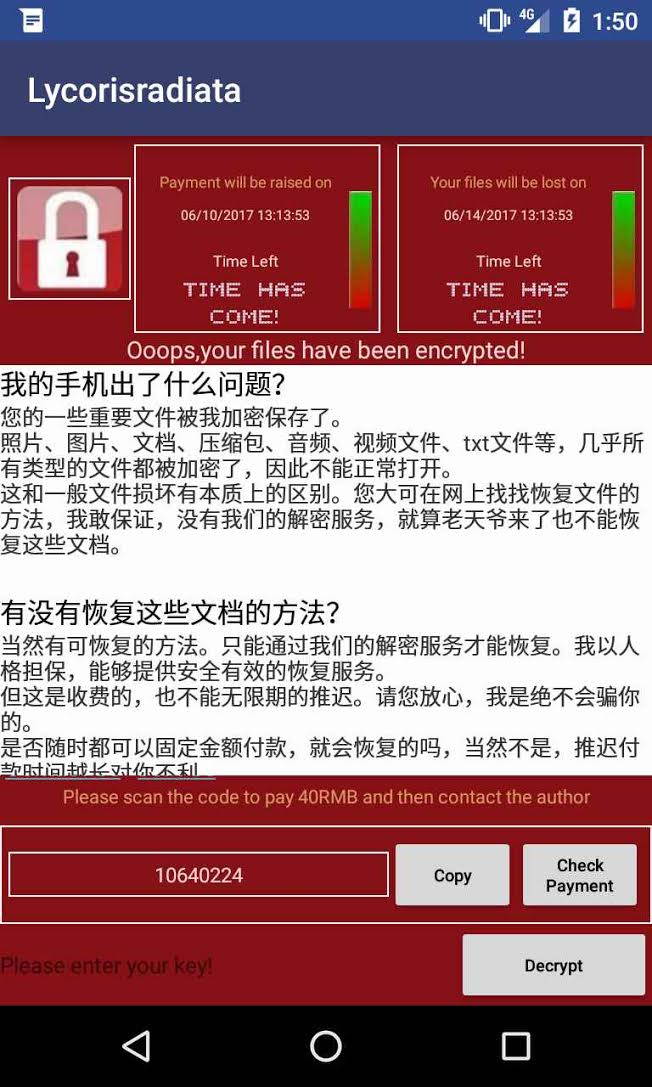
The ransomware then demands a ransom of 40 Chinese Renminbi, which is equivalent to about 5-6 US dollars. This is not much compared to what other mobile ransomware has demanded in the past. The fact that the ransom is being demanded in regular currency and not in cryptocurrencies makes me think the people behind this are trying to make money, and fast. This is, however, risky as the money can be easily traced, unlike when sending cryptocurrencies.
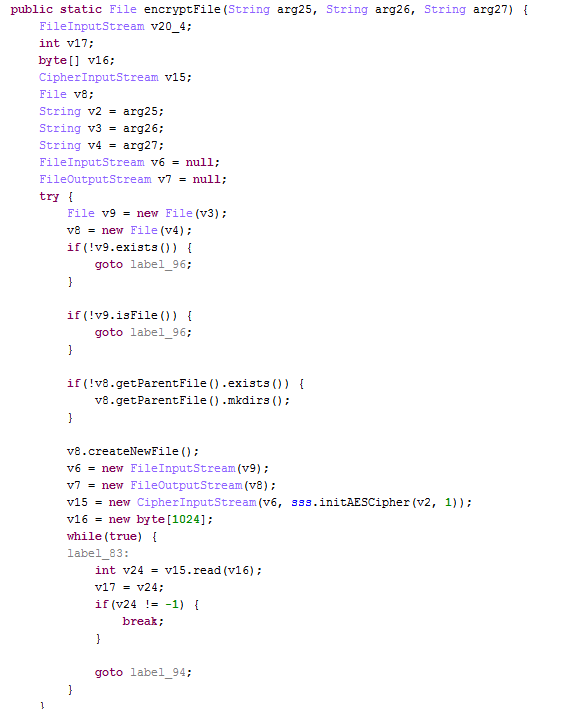
The code below shows that the files are encrypted using AES encryption. It only encrypts files whose names don’t begin with a “.” and does not encrypt files that include "DCIM", "download", "miad", ”android" and "com." in the path or files that are smaller than 10 KB.
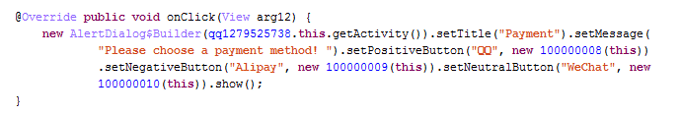
The ransom can be paid using the Chinese payment methods QQ, Alipay and WeChat, which can be seen from the code below.

Victims can scan QR codes to pay the ransom
The ransomware adds the highlighted extension, which can be seen below, to the encrypted files.

To protect your phone and valuable photos, videos, contacts stored on it from ransomware, make sure you frequently backup your data and install antivirus on all of your devices.
The ransomware was first reported by Chinese security company, Qihoo 360.
Hashes:
36f40d5a11d886a2280c57859cd5f22de2d78c87dcdb52ea601089745eeee494
200d8f98c326fc65f3a11dc5ff1951051c12991cc0996273eeb9b71b27bc294d