Cybercriminals prey on fear during the COVID-19 for their own gain.
The global Coronavirus pandemic is a terrible and frightening experience for everyone. But this virus carries its own parasites – an epidemic of cybercriminals preying on the fear of COVID-19.
Just as the speed and effect of the virus expanding across the world has taken everyone by surprise, so the growth of the criminal parasites living off it has been remarkable. Avast has already published numerous reports on Coronavirus-themed attacks, and advice for home workers and others in lockdown – such as an alleged Russian disinformation campaign; advice to hospitals that have come under increased attack; advice on how to stay sane at home (don’t dismiss this – police are already braced for an increase in domestic violence during, and caused by, the lockdown); and the public release of Coronavirus threat telemetry from Avast’s own Apklab.io research facility.
Threat overview
Here we’re going to take a broad sweep of the latest examples of these threats so that people can understand the extent, diversity and danger of the epidemic. The first thing to understand is that most of the threats – not all – include some form of social engineering. Coronavirus is purpose built for this. The most successful social engineering triggers are fear and urgency. Many people are more afraid now than they have ever been, and are urgently seeking anything that might offer news, hope or consolation.
So, here’s the first bit of advice – treat anything offering Coronavirus information with the same caution and social distancing you use for the virus itself. Only if you are 100% certain, after reflection, that the link and source are safe should you even consider going any further.
A second wave of threats Is best described as Coronavirus-related rather than Coronavirus-themed. Working from home (WFH), distance learning and always-on children is something new and strange to many of us. Cybercriminals are taking advantage of that newness and our lack of experience in this new normal. So, the second recommendation is simply, ‘be careful’. Don’t assume the VPN you read about last year or were offered yesterday is safe. Research everything new that you do (and that includes browser extensions where the number of downloads is no indication of security); and if you do need new apps or services, try to get them from a known and trusted source only; such as Avast’s own VPN offering.
The third piece of advice is not to assume that your own common sense will keep you safe from everything – it won’t. If you haven’t got a good and up-to-date anti-malware solution installed on all of your devices, now is the time to get one.
Recent attacks
What follows is a broad overview of some of the recent cyber scams and threats that have evolved on the back of coronavirus. It is only a very small percentage of what is going on, but hopefully enough to give some indication of the depth, range, speed and versatility of the modern cybercriminal.
Working, and studying, from home
Zoombombing
Both working and learning from home in the lockdown have led to a dramatic increase in the use of online video conferencing apps -- such as Zoom. Some of these apps do not have sufficient security, while new users often don't know how to use the apps securely. This has led to a rise in what is known as zoombombing; that is, gate-crashing the video conference and interjecting… well, whatever -- but often pornography or lewd photographs.
The problem isn't limited to Zoom. On March 26, it was reported that Norwegian students on a school video call found themselves watching a naked man engaged in lewd activity. This was not Zoom, and demonstrates that the issue is not limited to Zoom. It can occur whenever an attacker can find or guess the video conference URL. The solutions are to keep the URL private, to apply an access password where possible, to limit video access (the teacher/conference leader does not really need to see the viewers), to disable 'join before host', and to prevent anyone who is removed from rejoining.
Hackers are attacking home routers -- Linksys and probably D-Link -- to redirect people at home to a malicious site that offers a false 'COVID-19 Inform App'. The app claims to be provided by the World Health Organization (WHO), but is an infostealer called Oski. The attack on the router is probably a brute-force attempt at the password; so, it is important to change all passwords associated with your home router to new, unique strong passwords.
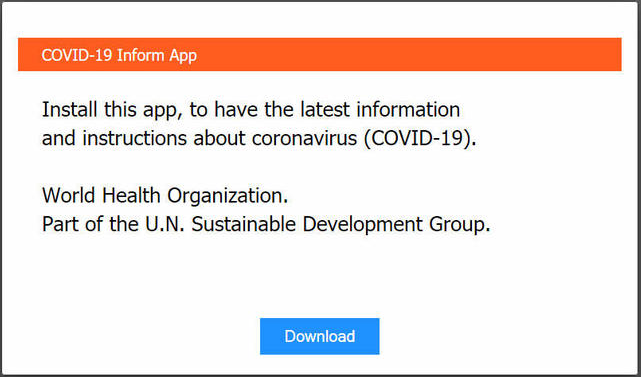 Figure 1. Fake app offered after router compromise
Figure 1. Fake app offered after router compromise
Phishing and malware
A campaign of emails pretending to come from Dr. Tedros Adhanom Ghebreyesus, Director-General, World Health Organization, commenced on March 19. The recipient is addressed by name; but this is simply stripped out of the email address. The email carries an attachment that includes the Agent Tesla malware -- a keylogger and infostealer.
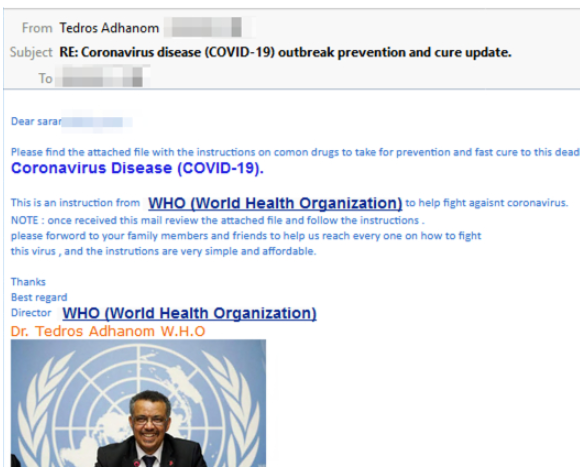 Figure 2. Phishing email that claims to be from the WHO
Figure 2. Phishing email that claims to be from the WHO
A phishing campaign pretending to come from a major bank was reported on March 23. The email offered financial relief on credit card bills. A 'Start Here' button sent victims to a genuine-looking bank landing page. The landing page asked for card details (including CVV number).
The Ginp banking trojan has a new functionality. If installed, it can receive a command from the hackers to open a webpage called 'Coronavirus Finder'. This offers details of nearby locals who have been infected with the virus, for just €0.75. If agreed, a page is opened for payment. The victim neither receives any information nor is charged the €0.75 -- but that doesn't matter because he or she has already handed over full credit card details to the hacker.
An Android app titled as a Coronavirus Tracker is really scareware. It pretends the hacker has stolen the user's contacts, photos and videos, and will release them to the internet unless $250 is paid. There is no evidence that this malware has been very successful, but it should be considered as a typical coronavirus-themed threat.
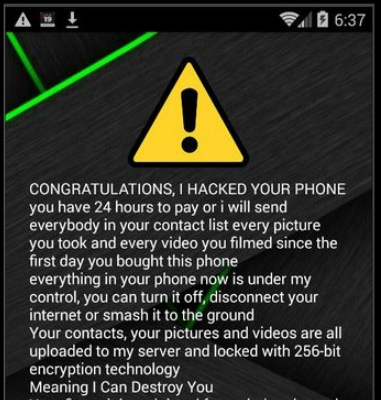 Figure 3. Scareware delivered from a fake 'Coronavirus Finder' web page
Figure 3. Scareware delivered from a fake 'Coronavirus Finder' web page
The Ryuk ransomware is being used to target healthcare organizations, which might feel they have no choice but to pay up in the coronavirus health emergency. There have been ten known instances in the last month.
The Czech Republic reported a ransomware attack on Brno University Hospital which forced the hospital to shut down its entire IT network, postpone urgent surgical interventions and re-route new acute patients to a nearby hospital. Brno is a major coronavirus research center.
Most cybersecurity experts expect to see a rise in ransomware attacks during the pandemic, simply escalating a problem that according to underwriters increased by 131% in 2019 over 2018. It is true that some criminals have they said they won’t attack health institutions during the crisis – some might not, many others will and already are.
Scams
The website coronavirusmedicalkit[.]com, which was shuttered by the FBI on March 22, had been offering free vaccine kits -- falsely claiming they came from the WHO -- for just the shipping charge of $4.95. There is no WHO vaccine, but the website gets $4.95 (small change) and your card details (big change).
On March 25, the FBI arrested a California man engaged in an investment scam. He claimed he had developed a coronavirus prevention pill and an injection cure, and was seeking investors. It was a lie -- but more than 2 million people saw his claims on YouTube and Instagram.
On March 27, the Federal Trade Commission (FTC) issued a warning that scammers are using the pandemic in illegal robocalls (an automated call with a pre-recorded message). Just hang up. Pressing a button to talk to a live person merely tells the scamming industry that you are potentially susceptible to other robocalls.
Rogue hardware
Rogue hardware is any unsanctioned hardware surreptitiously attached to a system or network. Examples in the past include swapping a legitimate keyboard for a same-make one that has a malicious implant. During increased work from home and the lockdown, this will be harder in a home -- but what about the now-empty offices? There are criminal gangs and old-fashioned nation-state agents quietly breaking into empty offices right now to install rogue hardware ready for when the pandemic ends.
The future
Things are going to get much worse before they get better. The UK deputy chief medical officer Dr Jenny Harries has warned it could be up to six months before life returns to ‘normal’. That’s the medical crisis, which will be followed by the results of a severe economic crisis. A $2 trillion bill to stimulate the U.S. economy and respond to the coronavirus outbreak has been signed into law by President Trump. Other countries are doing similar, albeit on smaller scales. With such huge amounts of money moving from governments to companies and individuals affected by coronavirus, the parasites will do as much as possible to divert it into their own hands.
This has already started. On the day of compiling this post, two such phishing campaigns have been detected – one in Canada headed ‘COVID-19 Relief’ and offering an immediate payment of $2,500, and another in Australia offering a payment of 2,500 Australian dollars. Such attacks will grow and continue throughout the year.
Other new campaigns detected today include one claiming the recipient has been infected with coronavirus and needs to complete an attached form and proceed to hospital. Opening the attached form drops a trojan on the victim.
The phishing parasites have followed the spread of the virus, starting in China where it all began, following into South Korea and other Asian countries, and moving into Europe via Italy. With the U.S. now the most infected country, it should brace itself for an imminent barrage of coronavirus-related phishing and scam campaigns.
With the situation getting worse, we all need to exercise extreme caution and heightened vigilance over anything received by email, and everywhere we go on the internet. This requires greater phishing and scam awareness. Do not assume that because you can easily detect a badly written, typo-ridden phish from a Nigerian princess that you will be able to detect all phish – you won’t. For that reason alone, it is imperative we all install and maintain a good anti-virus product.