Discover how cybercriminals are using fake online forms to steal personal data. Learn how phishing scams mimic trusted brands and how you can protect yourself.
Online threats have become increasingly sophisticated, and phishing attacks are no exception. Among the many tactics cybercriminals deploy, developing phishing campaigns by mimicking well-known companies and duplicating their online forms has emerged as a quick, cost-effective, and deceptively simple method for stealing sensitive user information. The alarming rise in the success of these campaigns, uncovered in the Q1 Gen Threat Report, speaks volumes about how cybercriminals are exploiting weaknesses in both technology and human trust. This article explores how these attacks work, why they’re so effective, and what you can do to protect yourself.
Understanding phishing through online forms
Phishing preys on the very human - and often essential - trait of trust. These attacks lure users into providing personal information by mimicking legitimate, and trusted, websites or services. Phishing through online forms takes advantage of tools like website builders and dynamic DNS (DDNS) services to create fake login or data submission pages that appear genuine.
An unsuspecting user might click on a link in an email, claiming their account has been blocked or urging immediate action to avoid service interruption. These emails direct users to counterfeit forms that ask for login details, payment information, or other sensitive personal data.
Once the victim enters their information, it’s collected by the attacker and used for purposes such as identity theft, financial fraud, or even further cyberattacks.
How attackers exploit online website builders
Online website builders, like Weebly and Wix, are popular tools for creating websites without coding skills. Their accessibility and user-friendly drag-and-drop interfaces make them appealing not only to legitimate users but also to cybercriminals.
Phishers exploit such legitimate platforms because they offer advantages like trusted hosting domains and customizable subdomains. These elements make phishing pages harder to detect and allow them to bypass email spam filters or antivirus software.
Attackers often create subdomains that mimic well-known brands to appear more legitimate. Common examples include:
- updatefacebookmeta[.]weebly[.]com
- outlookauthenticationmicrosoft[.]weebly[.]com
These URLs might look legitimate at a glance, especially to someone who is busy or unfamiliar with spotting phishing attempts.
Beyond website builders, attackers are increasingly using dynamic DNS (DDNS) services and subdomain providers like DuckDNS. These services allow the creation of subdomains that mimic major companies in an attempt to deceive users. By leveraging DDNS, attackers add flexibility to their campaigns, making it easier to scale operations with minimal effort.
Why these pages are deceptively effective
Some phishing pages are shockingly sophisticated, closely mimicking the legitimate login forms of major companies or institutions. Others are poorly constructed, with red flags like inconsistent layouts, mismatched fonts, or visible passwords. However, even low-effort phishing pages can succeed because they’re often hosted on trusted domains, making them harder for filters to detect.
Common warning signs
Here are a few indicators of a phishing page to watch out for, even when hosted on trusted platforms:
- Mismatched or unprofessional design
- Login pages that don’t mask passwords
- Irrelevant or suspicious menu items
- Subdomain names that seem odd or contain typos
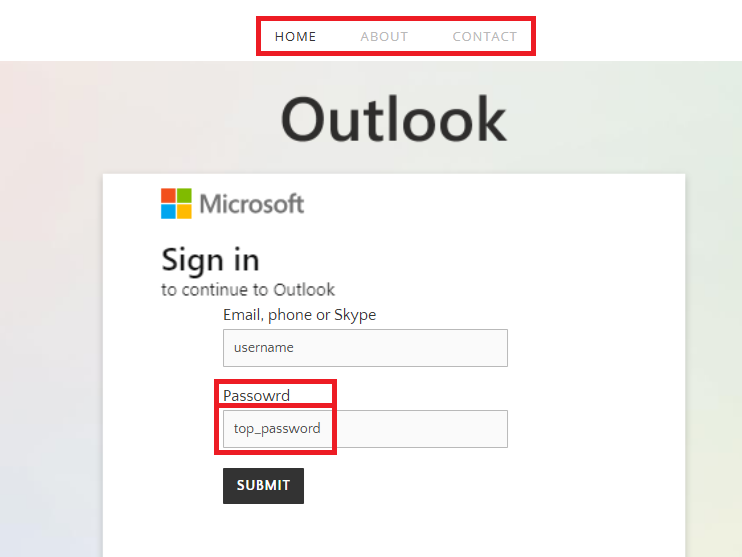
Example of an obvious phishing page, showing common warning signs
Protecting yourself from phishing attacks
While phishing campaigns are becoming harder to detect, there are clear steps you can take to protect yourself and your personal data:
- Examine URLs carefully: Check subdomains and domain names for typos or irrelevant elements. A login page hosted on something like "weebly.com" is a major red flag.
- Enable two-factor authentication (2FA): Even if your credentials are compromised, 2FA adds an additional layer of security, preventing attackers from accessing accounts.
- Look for secure indicators: Ensure that the website displays a padlock icon in the address bar and that the URL starts with "https." However, remember that even secure connections do not guarantee legitimacy.
- Be cautious with urgent emails: Most phishing emails rely on urgency to trick unsuspecting victims. Think twice before clicking links in emails that demand immediate action.
- Use reliable antivirus and anti-phishing tools: Security software with updated phishing detection capabilities can help identify malicious links before you fall victim.
- Report suspicious pages: If you come across a phishing page, report it to the hosting platform or security organizations.
Staying ahead of emerging threats
The bottom line is that phishing campaigns leveraging online forms will likely remain a popular tactic for cybercriminals due to their speed, affordability, and effectiveness. However, increased awareness, combined with smarter security measures, can help mitigate these threats and keep users safe online.
Every user holds the power to disrupt the success rate of phishing scams. By staying vigilant and informed, we can collectively make it harder for attackers to exploit trust in an increasingly digital world.