The program developer has issued a fix, and users should update immediately.
Recently, an interesting vulnerability was discovered by French security researcher, Elliot Alderson, in the Android app ES File Explorer (version 4.1.9.7.4 and below). ES File Explorer is a file manager, which has been downloaded more than 100,000,000 times from the Google Play Store. The older versions of the app start an unauthenticated web server, typically after the app is opened by the user at least once, and allows anyone connected to the same network, which can include public Wi-Fi networks and business networks, to interact with the application and access all files on the Android device’s file system.
The vulnerability was patched via an update issued by ES File Explorer, yet Avast data shows more than 60,000 users still running a vulnerable version of the app. Avast PC Antivirus users can scan their network using Avast Wi-Fi Inspector to help them discover devices running a vulnerable version of ES File Explorer on a mobile device connected to their home network.
The server listens on TCP port 59777 and allows potential attackers to not only transfer files, including photos and videos, from the device, but also run installed applications and exfiltrate information about the device, installed applications and default apps by sending specially crafted JSON requests to the target. Attackers can send the following commands to the victims’ devices which have the vulnerable app installed:
-
List all files on the device
-
List all pictures on the device
-
List all videos on the device
-
List all audio files on the device
-
List all apps installed on the device
-
List all system apps installed on the device
-
List all apps installed on the internal memory of the device
-
List all apps installed on the SD card of the device
-
Get device information
-
Pull an app from the device
-
Launch an app of the attacker’s choice
-
Get the icon of an app of the attacker’s choice
In addition to the commands, the web server also allows the attackers to download any file they know the path to. Some of the commands conveniently enable the retrieval of the paths to interesting files such as personal photos, videos, music, and voice recordings. A CVE number, CVE-2019-6447, has been assigned to this vulnerability.
This issue has been fixed by ES File Explorer on January 18, 2019 in an update to the app:
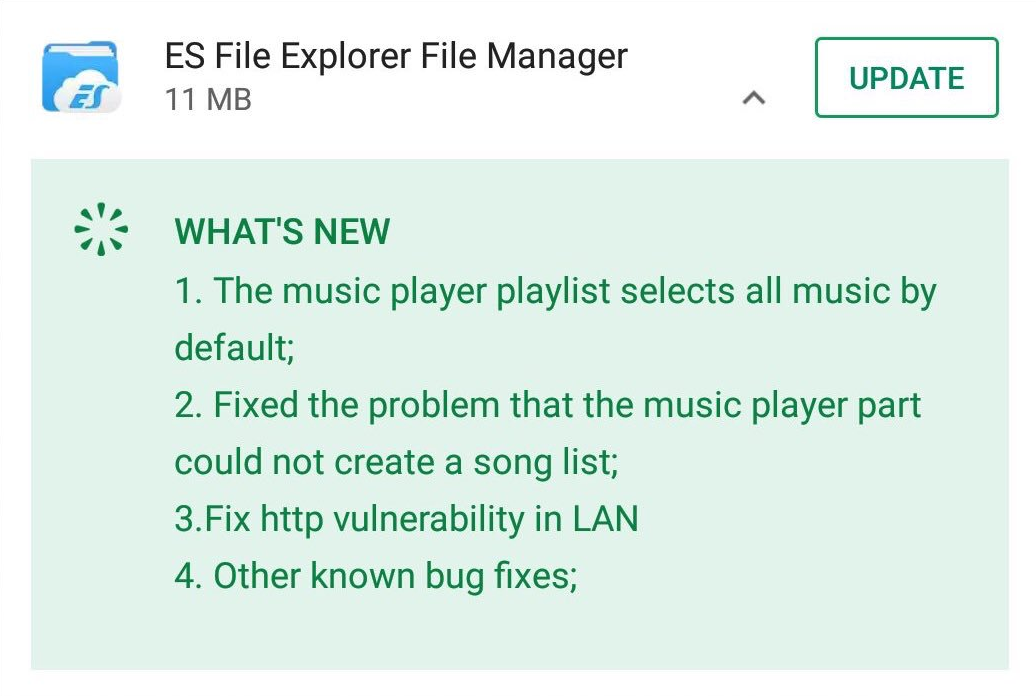
What can users do?
1- Immediately update your ES File Explorer app to the latest version in the Google Play Store to avoid unwanted data leaks, which may occur on public Wi-Fi networks, private networks, and business networks.
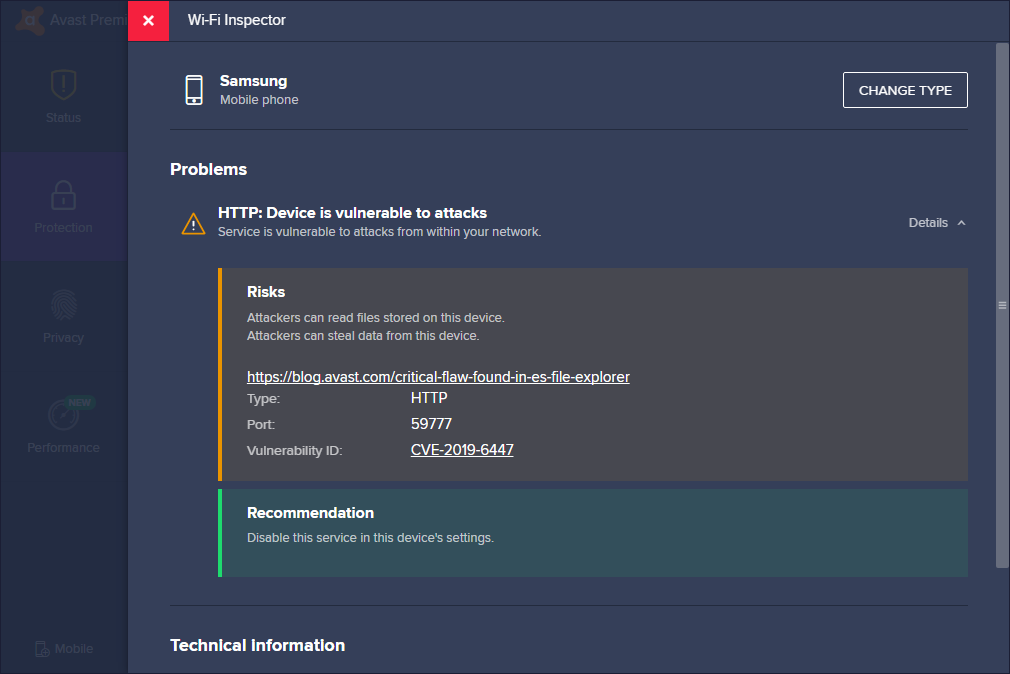
2 - Test every connected mobile device on your home network by running the Avast Antivirus’s built-in Wi-Fi Inspector feature on a PC. In case a mobile device connected to your network is vulnerable, Avast Wi-Fi Inspector will display a warning similar to the one in the image below:
3 - Always update all of your apps to the latest version to protect you, your family, and your businesses from security threats.