Based on analysis of past Locky ransomware attacks, experts in the Avast Threat Labs predict that another attack is imminent.
Locky ransomware, a variant of ransomware that scrambles your files, changes all the names, and then demands payment to unscramble them and release them back to you, has taken a holiday of sorts. Avast detection of Locky shows that attacks have slowed down considerably during the days before Christmas through New Year and leading up to Eastern Orthodox Christmas, which is celebrated in Russia on January 7.
The Avast Threat Lab analyzes the lifecycle of Locky, and we can see small peaks, new spread methods, new binaries etc., usually occurring before a new campaign starts. This graph shows data for the last one hundred days based on the number of users who saw the Locky downloader. Notice that a slow-down occurs for several days before a new round of attacks; but this time it’s been more than 15 days, which doesn’t fit the pattern. The drop between attacks is not typically as significant as it has been during the 2016-17 winter holiday period.
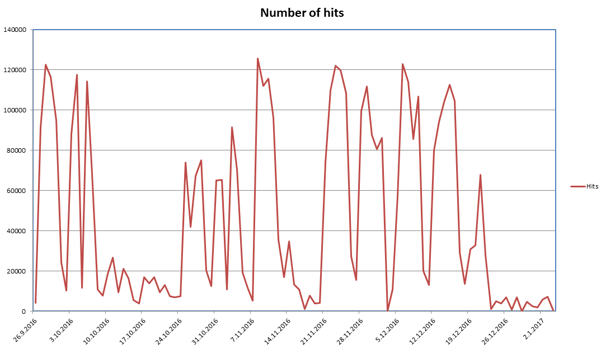
When we consider why the incidents of Locky dropped during the last 15 days we have to wonder:
- Are ransomware attacks down over the holidays because business users, those victimized the most, are not at work?
- Did the attackers decide to reduce the number of overall attacks?
- Are they preparing a new campaign?
- Could they just be celebrating Christmas?
- Like the Grinch, did their small hearts grow three sizes and they abandoned the ransomware business?
My personal guess is there will be a new Locky ransomware campaign, starting after January 7.
How to protect yourself from Locky ransomware
- As always, don’t open suspicious attachments (e.g. .doc, .xls, and .zip files)
- Disable Microsoft Office macros by default and never enable macros in strange/unknown attachments that you receive via email
- Keep recent backup copies of important data in a secure place either online or offline
- Ensure that your system and applications are fully updated and patched
You can read more about Locky ransomware in our previous blog posts:
Locky’s JavaScript downloader
A closer look at the Locky ransomware