Locky is a considerable security threat that is now widely spread.
Locky ransomware is a considerable security threat that is now widely spread.
It seems that Locky’s authors are now predominately using one campaign to spread the ransomware. Last week, we published a blog post about Locky Ransomware, the ransomware that is most likely being spread by the infamous Dridex botnet. In our last blog post, we described three campaigns the Locky authors are using to spread their malware. Now Locky’s authors are mainly using the campaign with javascript packed into a zip file sent to people through phishing emails.

We further analyzed the third campaign version we mentioned in our last blog post and discovered that each email contains unique javascript obfuscation, to circumvent email client spam filters.
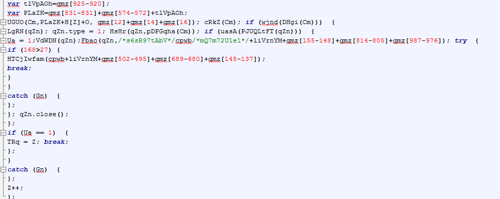
The script above downloads and runs the cryptolocker.

The JavaScript opens a website, like the one highlighted above and then the Locky file is downloaded and executed.
From March 9th - March 14th, 163,746 of our users encountered a total of 208,000 emails with the Locky downloader.
In the graph below there is a noticeable drop during last weekend, but we expect this to increase again. From the graph we can also see a quarter of people saw more than one phishing email.

The Y axis shows the number of users and the X access the date in YYMMDD format.
New domains hosting Locky’s executable ransomware are created everyday and some of the domains are used other ransomware as well, for example the subdomains of spannflow are used as payment sites for TeslaCrypt, which makes us believe their is a close relationship between TeslaCrypt and Locky.
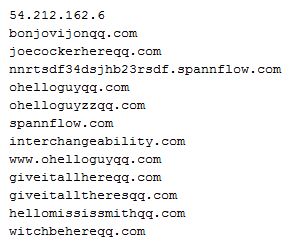
Ransomware attacks not only put data at risk, but can also costs victims a lot of money and stress. Locky’s ransom demand starts at 0,5 bitcoin, which is about $200. We expect that around 10% of people confronted with ransomware pay to get a decryption key.
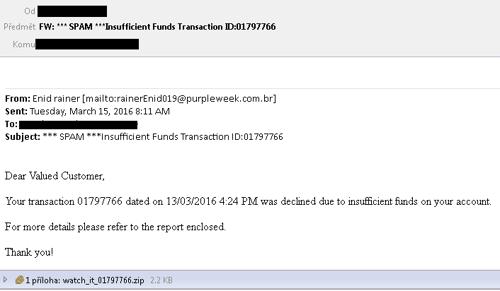
An example of a Locky phishing email

Map showing which regions Locky is targeting.
We can only speculate that Japan, France and the USA are being targeted the most, because they are wealthy countries.
How to prevent a ransomware infection
- Make sure you have antivirus installed
- As always, don’t open suspicious attachments (e.g. .doc, .xls, and .zip files)
- Keep recent backup copies of important data in a secure place either online or offline