 The path from the creation of malicious program to its delivery onto victims' computers is long nowadays and involves many different players with the same goal - to make a financial gain. Malware authors usually offer their software to cyber criminals who in turn distribute it via underground forums. This is the how they keep their anonymous status. We have previously seen many famous malicious programs start this way.
The path from the creation of malicious program to its delivery onto victims' computers is long nowadays and involves many different players with the same goal - to make a financial gain. Malware authors usually offer their software to cyber criminals who in turn distribute it via underground forums. This is the how they keep their anonymous status. We have previously seen many famous malicious programs start this way.
In the past, the Russian banking Trojan Carberp was heavily advertised on shady forums. In the beginning of the year, an attempt to sell a new ransomware called Prison Locker was reported. Last year, we blogged about Trojan Solarbot which choose to promote itself through a well- designed website, appearing very official.
However, we don't always know all the details about every piece of malware, from the code to how it is being distributed. The Trojan dubbed i2Ninja, for example, made headlines last year, but we never received a real sample containing all the functionalities the media reported on. Or do you remember the Hand of Thief Trojan for Linux desktops? Its variant for the Android platform was also advertised, but again, we never encountered it in our Virus Lab. These advertisements could have lacked the real code behind them or may have gone under in the pile of cyberthreats.
In March 2013 a new banking Trojan dubbed Minerva was introduced on a Russian forum. We will see that it is awfully successful in what it promised to do. 
Features
The Minerva Bot is primarily a banking Trojan based on its form grabbing capabilities. Supported commands promoted in the advertisement (vweb & vstealth for visiting web site; update & down for new malware downloads) are visible in the resources of the binary: 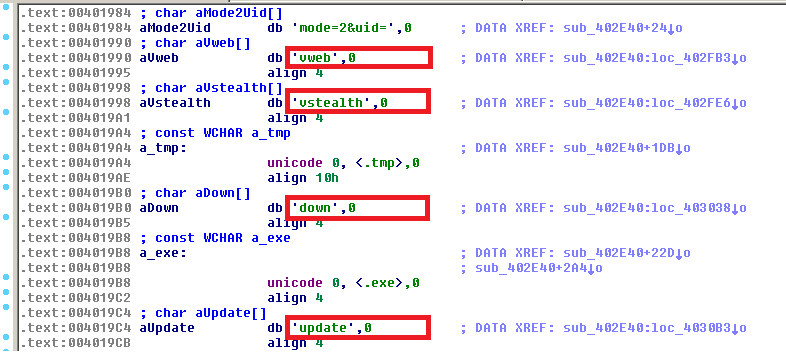
Jungle of POS Trojans
Here is a brief summary on the malware in this area:
Recently we have pointed out that most ATMs are running Windows XP. The Target attack was performed by a Trojan containing the string "KARTOXA" (means potato in Russian) that is connected to many similar point of sales (POS) Trojans (BlackPOS, VSkimmer/Hesetox etc). The Minerva Bot is often distributed with some of these POS Trojans, e.g. Alina, JackBot, VSkimmer, etc.
Minerva Bot's Structure
This Trojan was very likely written directly in assembly, because it contains only one section .text with both 32-bit and 64-bit code. Its form grabbing functionality is the core of the modules. However, the POS stealing feature is a part of the x86 module only. 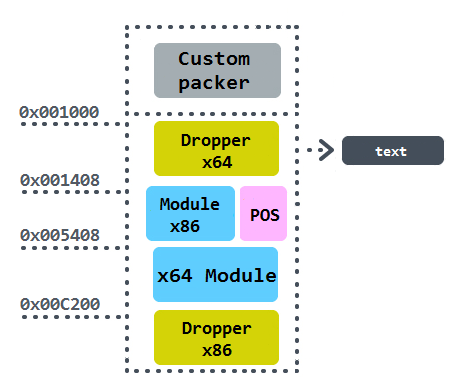
The value of the code segment (CS ) register is tested. If the code runs in 32-bit WOW64 process then CS equals 0x23 and the switch to 64-bit code becomes available in the DecideArchitecture procedure. The mode of the process is then double-checked by calling on the IsWow64Process API function. 
The switch between x86 and x64 execution is performed by the retf instruction with two arguments on the stack: The segment selector (0x33) and the 64-bit address (0x40C3E1). The internals behind this far jump execution are explained here. 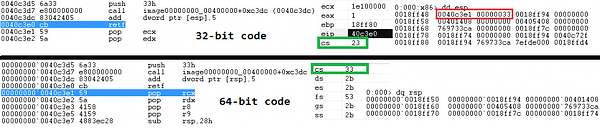
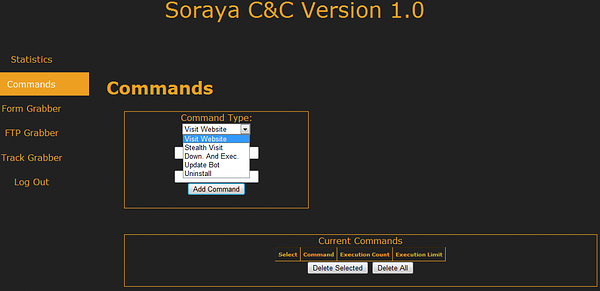
C&C panel Soraya
There is a Command & Control panel available for a botnet operator. The panel itself together with statistics of origin of stolen data are provided in the blogpost by ArborNetworks.
Acknowledgement
Thanks to my colleague, Jaromír Hořejší, for cooperation on this analysis. The front picture was created by the independent digital artist Veronika Begánová.
Sources