In February, we looked at the first part of the fake Korean bank application analysis along with Android:Tramp (TRAck My Phone malicious Android application), which uses it. In this blogpost, we will look at another two Android malware families which supposedly utilize the same bunch of fake Korean bank applications. At the end of this article, we will discuss the origin of malware creators.
Analysis of Android:AgentSpy
It is interesting to search for references of bank applications package names - KR_HNBank, KR_KBBank, KR_NHBank, KR_SHBank, KR_WRBank. One reference goes to a malicious application called Android:AgentSpy. The infection vector of this application was described by Symantec, contagio mobile and Alyac. We will not delve into details, we will just mention that the malicious application is pushed to a connected mobile phone via ADB.EXE (Android Debug Bridge). The uploaded malicious file is called AV_cdk.apk.
Android:AgentSpy contains activity MainActivity and several receivers and service CoreService.
BootBroadcastReceiver
Monitors android.intent.action.BOOT_COMPLETED and android.intent.action.USER_PRESENT and if received, starts CoreService. It also monitors attempts to add or remove packages - android.intent.action.PACKAGE_ADDED and android.intent.action.PACKAGE_REMOVED.
CoreService
1) Calls regularly home and reports available connection types (wifi, net, wap), IMSI, installed bank apps
2) Regularly polls C&C and responds to the following commands
sendsms - sends SMS to a given mobile number
issms - whether to steal received SMS or not
iscall - whether to block outgoing call
contact - steals contact information and upload them to C&C
apps - list of installed bank apps
changeapp - replaces original bank applications with fake bank applications
move - changes C&C server
PhoneListener receiver
Moniors new outgoing calls. If android.intent.action.NEW_OUTGOING_CALL is received, information about the outgoing call is sent to C&C.
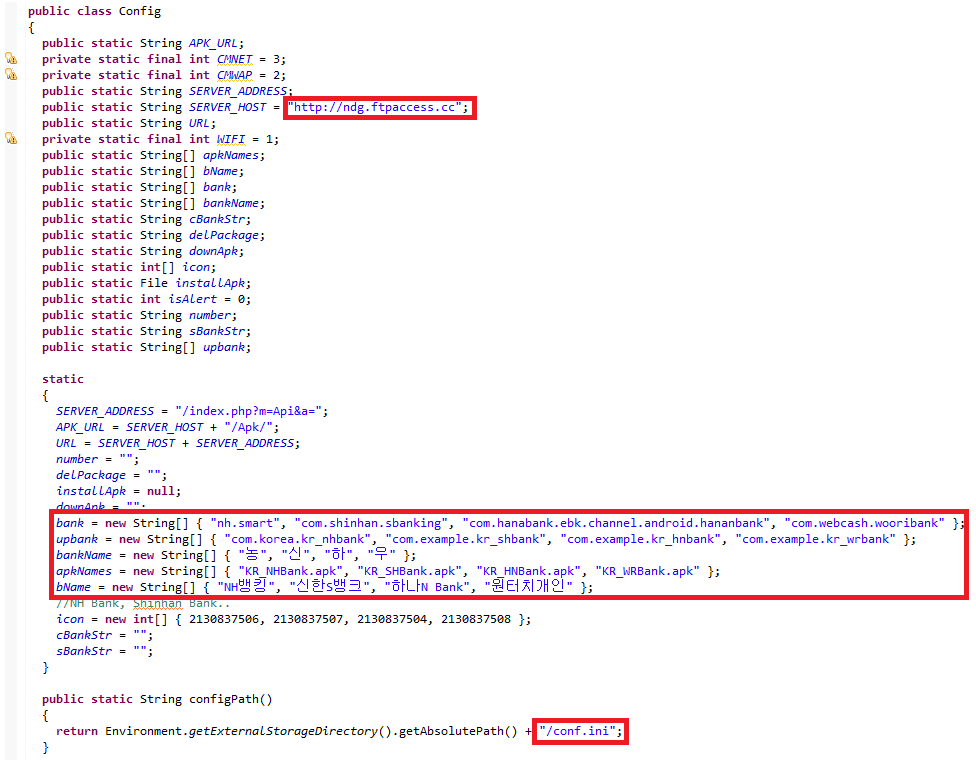
Config class
Contains C&C URL, name of bank packages (String array bank), name of fake bank packages (String array apkNames). It also contains reference to conf.ini configuration file.
Analysis of Android:Telman
One more Android malware family, which uses fake bank applications is called Android:Telman. Similarly to Android:Tramp and Android:AgentSpy, it checks for installed packages of the above mentioned banks. If found, they are replaced by the fake applications. However, bank application names are only one letter long - N.apk. S.apk, W.apk, H.apk. Unlike Android:AgentSpy, uploaded malicious file is called xox.apk.
Android:Telman contains several interesting classes, BroadcastReceiver and services.
BroadcastReceiver monitors android.intent.action.BOOT_COMPLETED and android.intent.action.USER_PRESENT. The first one is "broadcast once, after the system has finished booting,",the second one is sent "when the user is present after device wakes up." As a reaction to both actions, Android:Telman issues "cmd_system_init" command from ClientService.
ClientService class
cmd_system_init - uploads phone info to C&C
cmd_query_phone_list - uploads phone contact list
cmd_update_phone_number - updates phone number
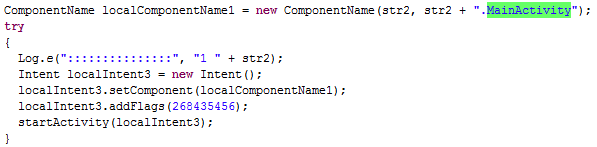
This service also schedules several timer tasks with a repeatable period of 12 seconds. It periodically calls the above mentioned commands. In addition, it calls bankHijak function, which monitors the most recent running tasks. If a regular bank application task is found, and if a fake bank application has not been downloaded yet, it starts BKMain activity. BKMain activity attempts to uninstall the real bank application and replace it with the fake one. The task is accompanied with the prompt "Notifications:", "The new version has been released. Please use after re-installation." If the fake bank application is successfully downloaded, it attempts to start it by invoking its main activity (named MainActivity). All leaked fake bank applications have the main activity called MainActivity, Android:Telman malware downloads, installs and invokes MainActivity activity from fake bank applications.
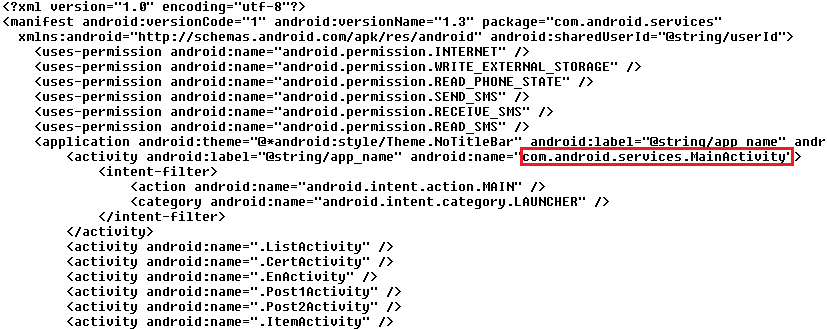
CallService class
It registers a broadcast receiver which monitors these actions: android.intent.action.PHONE_STATE android.intent.action.NEW_OUTGOING_CALL.
This service can modify call logs and terminate outgoing calls.
ContactsService class
It reads and parses all phone contact via accessing contacts provider URI content://com.android.contacts/contacts.
ProcessRemoteCmdService class
In 5 minute intervals, it queries command from C&C server. The received command may schedule SMS messages to be sent with given contents to a given list of phone numbers.
SMSService class
It registers a broadcast receiver which monitors android.provider.Telephony.SMS_RECEIVED. It uploads received SMS messages to the C&S server. It also parses contents of the received message and depending on that, it performs one of the following functions:
cmd_get_phone_number
cmd_forward_phone_number
cmd_update_ip
cmd_sms_intercept
cmd_phone_intercept
cmd_remote_control
cmd_start_bank
cmd_bank_Intercept
cmd_send_sms
Device administrator
Both Android:Telman and Android:AgentSpy have the same main activity named MainActivity, which performs the same action - it asks the user to give it a permission to run as device administrator. It is done by creating a new intent ACTION_ADD_DEVICE_ADMIN. String EXTRA_ADD_EXPLANATION misleadingly informs the user that the currently installed application is Google Search App, which "offers location-based personalized search results."
 The figure below shows the screen which appears to the mobile phone user.
The figure below shows the screen which appears to the mobile phone user.

After the user activates the device admin, the installed application cannot be uninstalled as simply as regular (non-device admin) applications. The uninstall button is disabled as shown in the figure below.

If the user wants to uninstall the application, he first needs to remove it from the device administration apps and then uninstall it.

After choosing Device administrators menu item, we can remove the application from device administrators by unchecking the check button. At this moment, it is possible to uninstall the application regularly, because the Uninstall button is now enabled.

Origin of authors
When analyzing the source codes, it seems that the authors are Chinese-speaking individuals. In several places of the source code, we can see logs and debug comments written in Chinese language. The code below shows a piece of code which tests whether the entered bank card number corresponds to the expected pattern. Depending on the length of the given inputs, the application issues debug information via (System.out.println). These messages are in Chinese. The figure below is from fake Hana bank application.
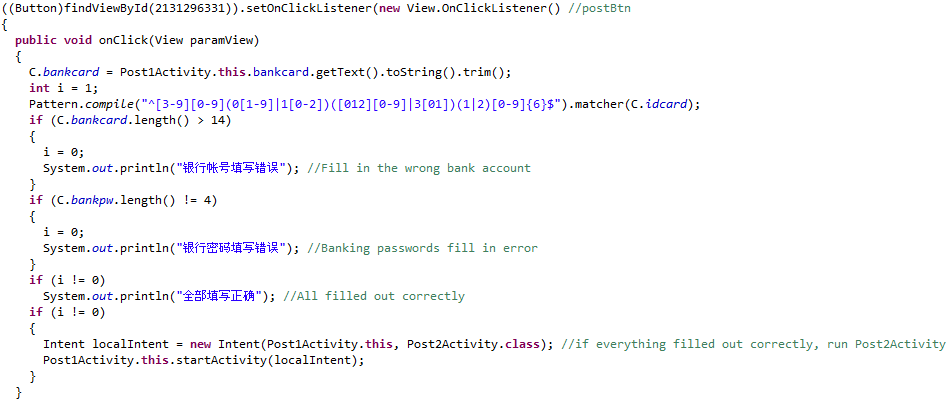
Figure below is from Android:Telman. These two characters mean "Unknown."
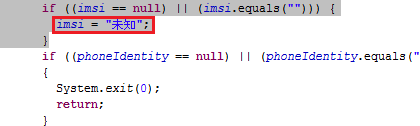
Figure below is from Android:AgentSpy, CoreService class. Similarly to other pieces of malware, this one also contains Chinese debug information not displayed to the victim. Messages displayed to victim are in the Korean language. This figure shows decompiled source code where you can see both Chinese and Korean characters.

Finally, it should not be surprising that all the samples were detected in South Korea, as confirmed by our telemetry system.
Conclusion
It seems that there is one version of fake banking applications which is shared and downloaded by several Android malware families. We presented three different Android malware families. Although their code and structure is very different from each other, they share some common features - probable origin of their authors, Korean texts, Chinese debug information, active in the same geographical location, target the same banks, the same principle of replacing regular bank app with fake bank app, steal contact info, intercept SMS and phone calls, etc.
Sources and Avast's detections
Android:Telman
418BB26B95608538E43BC505C0A4EBD136B2309DCE2C4B13B47FB56BF1335434
F0D19D696E3B767FB9C230BDA12EDC815276F1535DAA6CDAE349299F04956D2E
Android:AgentSpy
0840925753FBC8C68938090E5954ED289F6525CD29D8CF371A92D0839DCB8133
2528E2BA0049CFBCD9D7D1AF81CD75AAEBAA479482F3A8C97011540EE0B380BF
279AF458993ACBB78FCF67A8049089538DE7A7E26716EAA9430749681AE91BE2
Acknowledgement:
The author would like to thank to Peter Kalnai and David Fiser for their help and consultations related to this analysis.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.