About a year ago, we published this analysis about a pharming attack against Korean bank customers. The banks targeted by cybercriminals included NH Bank, Kookmin Bank, Hana Bank, ShinHan Bank, and Woori Bank. With the rise of Android-powered devices, these attacks now occur not only on the Windows platform, but also on the Android platform. In this blogpost we will look at a fake bank application and analyze several malware families which supposedly utilize them.
Original bank application
We will show just one bank application for brevity. For other banks the scenario is similar. The real Hana Bank application can be downloaded from Google Play. It has the following layout and background.

Notice the layout and background of the application.

Fake bank application
Now we are ready to look at the fake banking application. The initial screen looks very similar to the screen of the original bank application displayed above. Whenever a user clicks on any image in bordered table, he is immediately redirected to an activity which asks for his certificate password. Figures below show the initial screen from the fake application and the activity asking for certificate password.

When an incorrect password is entered, an error message is displayed. The application checks whether the password length is greater or equal to 5 characters. The application then asks for an account number and a 4-digit PIN number.

For entering the PIN number, the application displays another keyboard where the user enters his credentials. The last window to appear is the window asking the user to fill in the numbers from his security card.

When completed, all the gathered information is put into a JSON object and sent to the C&C server. The dumped JSON object containing all the data looks like the following:

It contains all the gathered information which allow attackers to send and authorize payments.
Analysis of Android:Tramp
Let's look at the GoogleService application first. The manifest contains suspicious permissions for processing SMS messages, outgoing calls, recording audio, gathering user location, etc...
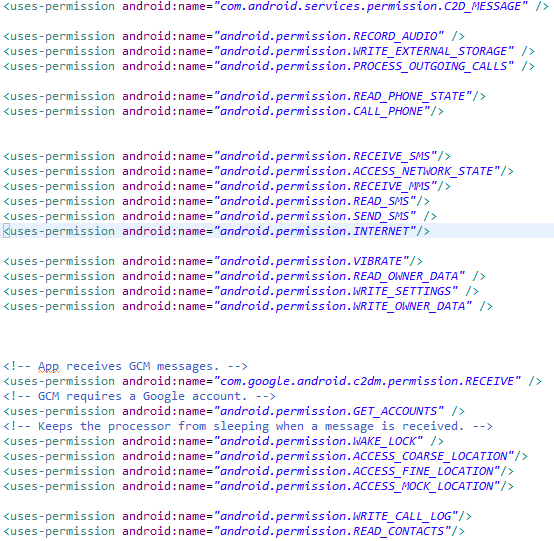
The important part of the application is class SMSBroadcastReceiver which extends BroadcastReceiver. Depending on received intent, it calls corresponding functions from the GoogleService class (described below):
1) Handles incoming SMS messages using intent android.provider.Telephony.SMS_RECEIVED
2) Handles Google Cloud messages
3) Handles incoming calls using intent TelephonyManager.ACTION_PHONE_STATE_CHANGED
The main functionality is implemented in class GoogleService. Depending of received Intent, GoogleService provides the following functions:
1) Sends POST request to a given URL
2) Registers a cloud message
3) Sends SMS message
4) Sends SMS messages in batch
5) Sends cloud message
6) Gets phone locations
7) Blocks calls
8) Gets contacts
9) Reads SMS messages stored in phone memory
10) Records outgoing calls
11) Uploads a file (previously recorded phone call)
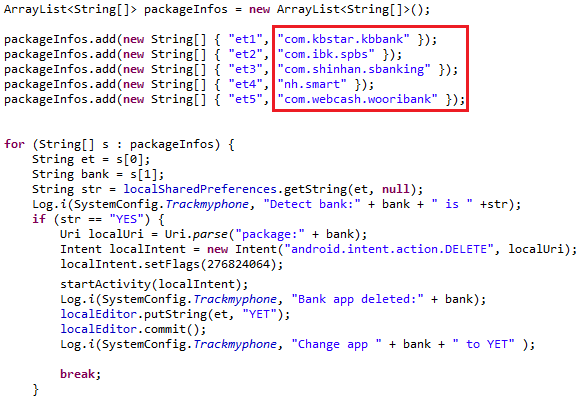
However, the most important class related to fake banking is called Mainservices. When executed, it checks if any of the predefined packages are found (com.kbstar.kbbank, com.ibk.spbs, com.shinhan.sbanking, nh.smart, com.webcash.wooribank). If found, it attempts to uninstall these packages (android.intent.action.DELETE) and replace them with the malicious ones.
When we look for similarities of this malicious GoogleService to other malware, we find that the GoogleService application is detected as Android:Tramp (TRAck My Phone). There is a writeup from F-Secure confirming our above mentioned analysis.
In the next part, we will look at other malware families utilizing the mentioned fake bank applications, and we will try to determine the origin of attackers based on artifacts found in malicious archives.
Sources and Avast's detections
Android:Tramp
05E16A68A7393C90334CF98C4C390DB67F2316126014DF1508CC8170025CE150
13226FA12F991ABAE16AC3308B7AAE6E55B6C4520A9E15E7BCECB9D4EF3015AD
Acknowledgement:
The author would like to thank to Peter Kalnai and David Fiser for help and consultations related to this analysis.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.