Several months ago I wrote a blog post about an adware downloader which after execution downloaded a few adware programs and installed them on the computer, giving no chance for the user to skip or bypass their installation. This time, we will analyze an application, which installs similar types of adware programs on user computers.
We received a file which appeared to be a crack of Pinnacle Studio HD Ultimate. After displaying the initial splash screen, it offers the user to install Pinnacle Pixie Activation 500. After confirmation, the crack is installed, but in addition to the crack, other programs and toolbars unexpectedly appeared on the compromised computer. Pinnacle was not the only target of this kind of attack. Cracks for programs like Sims, Nero, Rosetta Stone, and Pro Evolution Soccer 2013 were also used in distribution.

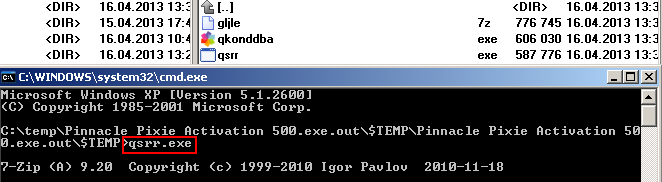
Let's look deep into the crack file. After unpacking, we can notice three files with random alphanumeric names: gljle.7z, which is a password protected 7-zip archive, qkonddba.exe, which is an original crack, and qsrr.exe, which is a console version of 7-zip application.
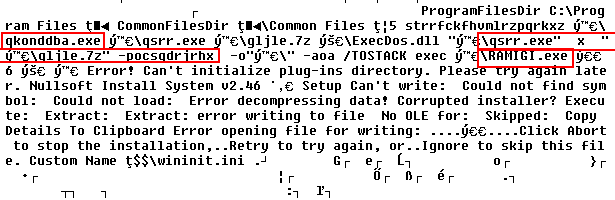
Our crack file is a Nullsoft Installer archive and after extracting its header, we can observe a few interesting text strings. Notice the red boxes in the figure below. We can see 7-zip console application(qsrr.exe) executed on file qljle.7z with parameter -pocsqdrjrhx, where -p means password and ocsqdrjrhx is the password. The extracted file from qljle.7z arvhive is named RAMIGI.exe and is later executed. File qkonddba.exe is also executed. We can see that the original crack file qkonddba.exe is bundled with 7-zip application and .7z archive, from which the payload is extracted and executed.
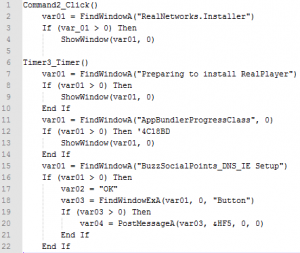
RAMIGI.exe is a downloader, written in Visual Basic, compiled with Visual Basic P-Code. The size of the downloader is 806912 bytes. After decompiling, we can observe similar code snippets as in the figure below. It searches for a window with certain names, and when these windows are found, they are hidden by calling system function ShowWindow with parameter 0. When necessary, it can find a button via FindWindowEx and "press" the button by calling the system function PostMessage.
Inside the RAMIGI file, we can notice two URL addresses in plaintext.
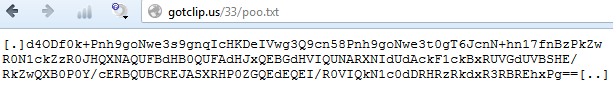
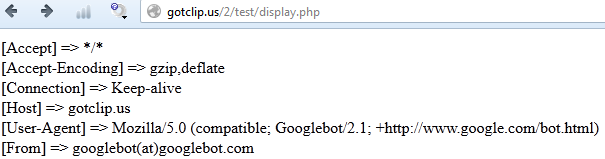
File poo.txt contains some text between "[.]" and "[..]" signatures. This text is encoded in base64. At first it must be decoded, then a value of 0x0f is subtracted from each of its characters and finally we can get the URL of the file which will be downloaded by RAMIGI downloader.
Before looking into the downloaded file, I have to mention an interesting Easter egg in RAMIGI.exe downloader. The downloader itself is quite simple, it does not offer too many functions, just download, decode and execute another file. However, its size is (as mentioned above) 806912 bytes. When I looked again in the RAMIGI.exe, I noticed a binary blob starting with GIF89 marker, which is a magic signature of a GIF picture. I therefore extracted this file, which is called Goooooooooogle_img and you can see it below. It is an animated GIF displaying Victoria Coren, famous writer, presenter and poker player, from British TV show "QI Series J Episode 1 - Jargon", time around 5:00, Youtube link here, in which she says the following sentences "People do complain that there aren't any good words for vagina. There's no way of saying it that sounds nice."


I have no idea what the purpose of this included image is, maybe just a joke, or so called Easter egg, but this animated GIF image has 770049 bytes, which is about 770049/806912 = 95 percent of the size of the entire RAMIGI downloader. Maybe the author of RAMIGI downloader is a big fan of Victoria. Aside from writing and presenting she is a famous professional poker player and maybe the author of RAMIGI likes poker too. Devoting 95% of the downloader size to Victoria may be considered as a tribute to her. Only he knows why this animated image is included. Malware creators often try to write their programs as tiny and as efficient as possible to stay less suspicious, but it seems that RAMIGI downloader is an exception. It could have had only a few tens of kilobytes, but thanks to its Easter egg, it has almost 1 megabyte :-).
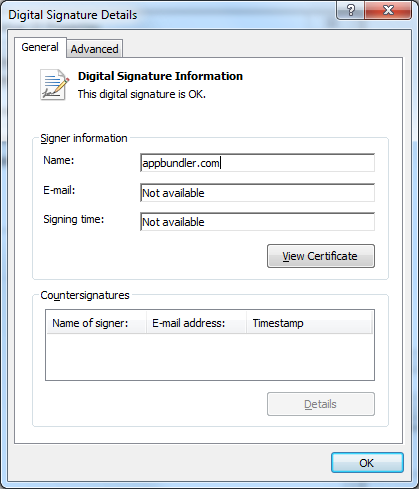
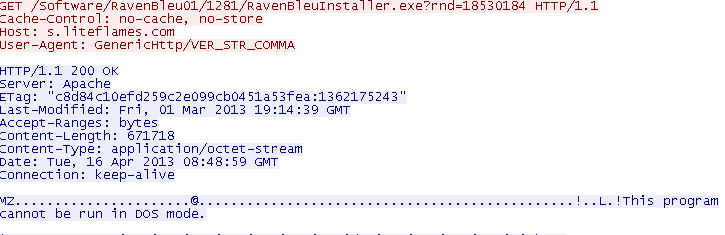
RAMIGI.exe downloads and executes another file called XvidSetup.exe. As mentioned before, RAMIGI.exe is active in memory; it searches for windows with certain names and hides them, therefore the following screenshots are not visible to the user on a compromised machine. The RAMIGI application emulates user clicks so quickly that the following windows immediately disappear. However, for better illustration, I will show you all these screenshots as you would see them if you downloaded and executed XvidSetup.exe manually. This installer has one interesting property - it is digitally signed by appbundler.com and its signature is valid.
Xvid is a video codec which can be downloaded for free from the original website. However, in our XvidSetup.exe we are told that we have a premium Xvid version, with sponsor offer from RavenBleu. I did not want to install anything but Xvid codec (or at least I wanted to choose what I wanted to install), so I chose "Custom xvid Installation with RavenBleu" and pressed "Next". First, XvidSetup.exe dropped and executed check_offer_rp.exe, which is a checker of offers from RealNetworks affiliate program. However it neither downloaded nor installed anything from this affiliate program. Maybe this affiliate ID is already blocked.

The installer did not offer me any choice and immediately started downloading and installing BasicScan, then RavenBleu, and finally it offered to install Xvid codec.
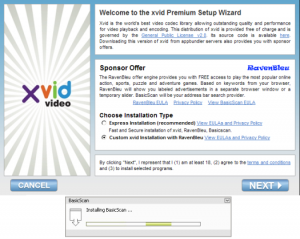
The Xvid codec itself is a legitimate application. The distribution is done without the permission of the publisher.
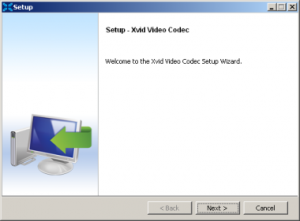
Both RavenBleu as well as BasicScan got executed.


BasicScan even appeared as an extension in Firefox and it's dll was also mapped into Internet Explorer address space. It allows BasicScan to track search queries the user entered into the address bar and receive a list of URLs received from basicscan.com server.
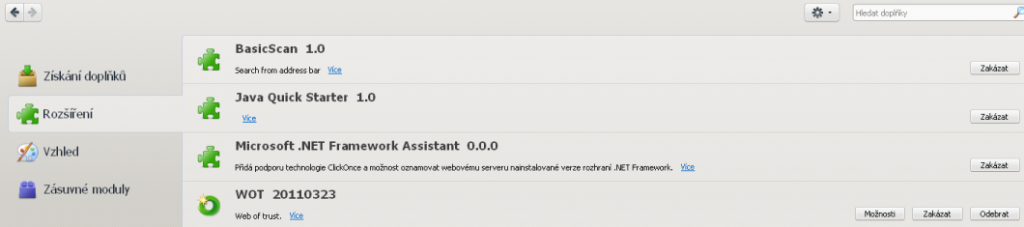
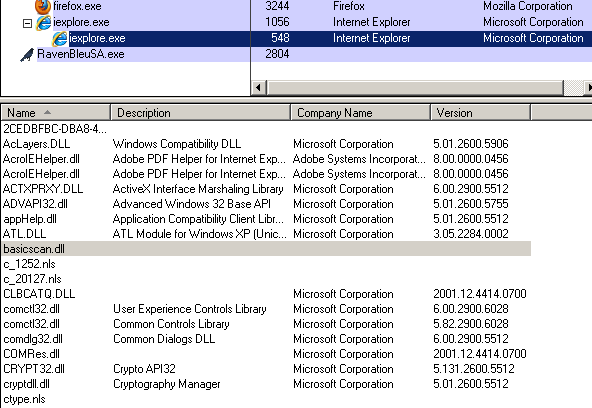
BasicScan was executed as a system service, it loaded basicscan.dll and called its export function named jocodefo.
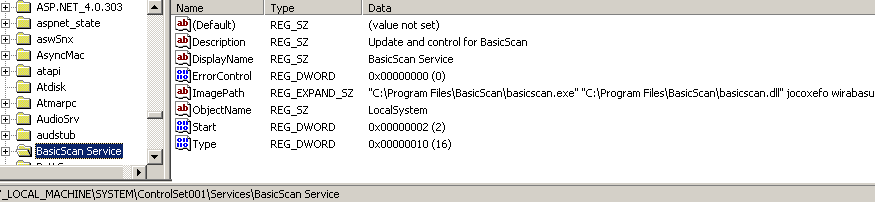
When I later typed a word into the Firefox address bar, it redirected me to www.basicscan.com, which contained advertisement links.
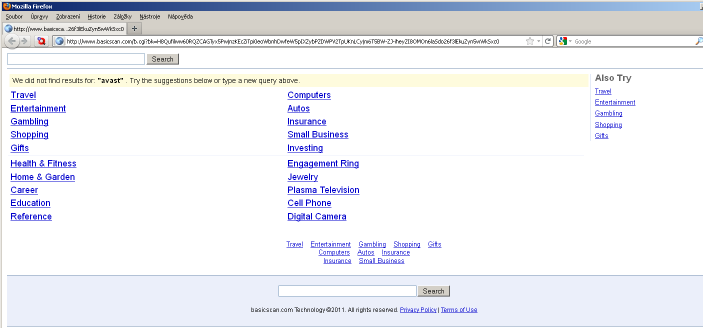
It also modified "keyword.URL" item in user_pref file. Keyword.URL preference enables to add a default search engine in Mozilla Firefox. This item was also changed and replaced with BasicScan.
Monetization is based on pay per install scheme. Many companies offer affiliate programs, where anyone can register and begin promoting their products. In this example, RealNetworks affiliate program use was attempted, http://www.realnetworks.com/affiliate-program/products-payouts.aspx . If the promotion is successful, the company pays its affiliate a certain amount of money for each install. Attackers therefore try to install the application to as many computers as possible to maximize their profits.
A second possibility of monetizing can come from the BasicSearch plugin, which may redirect or mislead victims to visit unwanted websites, or offer them sponsored links instead of the most relevant links. This behavior generates traffic, which may later be sold or misused for various purposes.
Who is behind this deceptive way of distributing unwanted programs to user computers? One of the installed applications, Raven Bleu (in English: Blue Raven) contains file copyright.txt, in which the first lines say: "Seekmo Search Assistant", "Copyright (c) 2000 - 2007 Zango Technologies LLC. All rights reserved.". According to Wikipedia, in 1999 a company called ePIPO was established, later it became 180solutions, Zango and nowadays it operates under name Pinball Corporation.
Conclusion:
Downloading cracks from torrents of file sharing servers is a popular method that many computer users try to save money by getting full licenses of paid commercial products for free. Aside from violating license rules, downloading files from untrusted and suspicious sources often leads to compromising user machines. Computer program cracks are often bundled with additional malware or adware downloaders, so an attempt to save a few dollars on a computer license may lead to much higher losses when malware gets installed or privacy is lost when applications like BasicScan are installed.
SHAs:
Pinnacle Pixie Activation 500.exe
E0B46F79C8A815C4E3267853719D2FC684C94B45546D433BAE0A4EE3F586B2B9
RAMIGI.exe
9B33E6831EDA8A9CCDE0CD02E728BAEF30A2239B696E6F2CCD992AF3224020B7
XvidSetup.exe
5F68D0E4F1C9C8442AEB424F851BDEA36802B6BCC3F00B4E9ADBBAAEFCBD3CEE
BasicScan.exe
292C07DCD772F00677FBF069BCAD8ADB38ED0917A645D470525D9A0B06256AB7
BasicScan.dll
2EC6292A89CCE33D3390E5B1230118D2D8AEE361D15D1B1D24191186B691B119