As a malware analyst, I sometimes have to deal with files, which cannot be classified as computer virus or malware, but their behavior when executed by user is still considered unwanted or suspicious. In this blogpost, we will look at an adware downloader. It comes in two different versions, one tiny - having only about 17KB and being written in .NET, and the other one bigger, using getrighttogo downloader builder. In user's computer, downloader was found in the following directory.
C:\Documents and Settings\Administrador\Meus documentos\Downloads\filme(1).exe
Users’ computer got infected via one of many sites similar to following ones – websites offering to download movies. After clicking on download links, .exe files were offered to download.
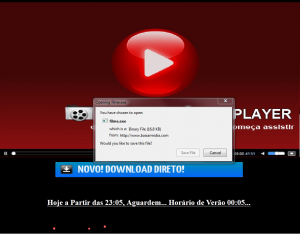
Figure 1 – Example of site the downloader was originally downloaded from
Figure 2 – Another website with possibility do download this downloader
And many more…
However, this analysis was done on programs downloaded from
onlinemidia.com/js/id52/arquivo.exe
baixarmidia.com/ids/id32/download.exe
which were available at the time of writing this blogpost.
It is also worth mentioning that all analyzed samples are signed by BR SOFTWARE LLC and their signatures are valid.
After downloading and executing download.exe, this downloader does not display any information to the user. It immediately starts contacting its server do download another setup file.
GET /baixar/Setupb.exe HTTP/1.1
Host: www.midiasetup.com
The following two sites are contacted to update statistics about installations.
http://www.midiastats.net/js/id52/stats.htm
http://www.midiastats.net/stats/confirma.htm
Another interesting fact is that all URLs downloader contacted are very new, created recently.
midiasetup.com 09-Oct-2012
midiastats.net 08-Oct-2012
onlinemidia.com 03-Oct-2012
baixarmidia.com 03-Oct-2012
There is no GUI (graphical user interface) button, which gives user an option to abort downloading data from internet. See Figure 3.

Figure 3 – Downloader GUI without possibility to terminate the process of downloading
After this new file (setupb.exe) is downloaded, it is executed and several files are copied to c:\Program Files\Acelerador de Downloads\ ( see Figure 4).
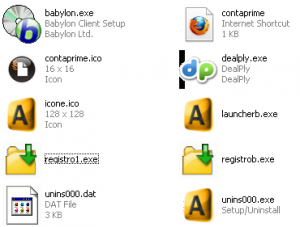
Figure 4 – List of files created in directory “Acelerador de Downloads”
Registro1.exe and launcherb.exe get immediately executed and installation of Babylon toolbar is offered to user.
User is given an option to install or not to install the toolbar.
If user chooses not to install Babylon Toolbar, no toolbar is finally installed, but installation package is being executed, which is shown in Figure 5. In addition log file in Application Data\Babylon\log_file.txt is created and several requests to babylon.com are performed (Figure 6). We consider this as non-standard behavior. If user chooses NOT TO INSTALL, nothing should be installed, no website should be contacted and no files should be left in his/her computer.

Figure 5 – List of running processes after choosing not to install Babylon Toolbar
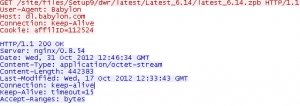
Figure 6 – Proof of contacting Babylon.com
Later, installation of dealply is offered, however there is no option to choose not to install this plugin.
After clicking to continue, new Firefox window is opened and system asks user to confirm installation of DealPly.xpi Firefox extension. User can cancel the installation of plugin and no installation is performed. Dealply.com is website with poor reputation.
There is also one more window caused by program registro1.exe. Window as shown in Figure 7 is displayed to the user. It encourages users to subscribe and receive daily SMS messages to their cell phones, priced at premium cost. When user tries to move window out of the center of the screen, it automatically returns its position back to the center of the screen.
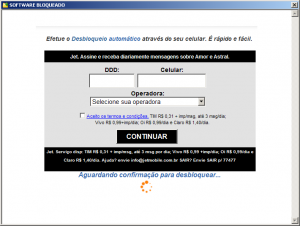
Figure 7 – Offer of subscription to premiums SMS service
When user tries to close this window, he/she is immediately redirected to the website as in Figure 8. This website has also a poor reputation. According to description, it offers the possibility to download at premium speed from various file sharing services.

Figure 8 – Website of file sharing service
As a conclusion, we have presented a simple downloader. It tricks user to download and execute it by denoting itself as “films” or “movies”. It downloads several installation packages from internet and it offers installation of various toolbars and plugins. It seems that the only reason for existence of this adware is to install toolbars/plugins, because each successful installation is monetized on pay per install principle. It also offers registration for premium SMS services and opens pop-up windows. Although not classified as typical malware, programs like this one fills users’ computers with garbage and, therefore, are detected and removed by avast!.
We also tried to contact the other companies whose products or services are used/installed by the malware to try to kill it closer to the source.
a) DealPly - they refused to provide us with any details on the affiliate. We must take in account that this business is good for both the creator of malware, but also for DealPly which then monetizes the ads placed by their toolbar, so it's quite understandable that they don't like such questions.
b) Babylon - their reply was much better and they immediately admitted the software is a fraud. They also acknowledged that this drives them 20k of installs daily. So this is not a small operation.
c) GlobalSign - although the digital signature in fact means only two things - that the binary was not modified after signing and that it was created by the owner of the certificate, it seems to users as more 'legit' than unsigned binaries. We were unable to get any info in reasonable amount of time regarding the identity of the creator of the software. But these guys have many certificates, not only from GlobalSign, also from GoDaddy.
d) Funmoods - the bad guys change from time to time what to install. So sometimes it's Babylon, sometimes Funmoods.
We've been tracking this for several weeks. The number of versions, unique binaries, domains (70+), urls, certificates is growing over time and, as you can see, we are basically powerless and the only thing we can do is to classify this threat and then create signatures again and again (or have it created automatically).
Analysis was done on files with following SHAs:
arquivo.exe B62CB69734067F26773CA53DA3C657670407F1768E689A4E22183CC879C7D1F9
download.exe 1FEE4F8D9C779799DB7EA06E0BFBA542E556FDCC7D853E7C8D37271B1A50CB42
filme.exe 117CF268AA9BE7AD050ACE2E92578A3384A37F66B2EEA687C27943D581296960