In October we wrote on our blog about a spreading Russian Trojan horse named the Bicololo. Since that time, the malware has continued to evolve and spread even further. Nowadays avast! saves several thousand PCs every day from its infection.
Short characterization
The Bicololo is characterized by its unique attack vector, which remains unchanged. It's primary objective is to inject the victim's etc/hosts file and redirect traffic of the most used Russian social sites into its phishing servers. The most frequent targets are vk.com, odnoklassniki.ru and mail.ru. Once the victim with infected system types these addresses into the browser he/she is presented with a fake log-in form. And because none of the targeted services uses secure connections via HTTPS by default there is no simple way for user to know about the posing danger and he willingly give his password to hackers.
Currently the malware spreads mainly in two forms which changed dramatically since our previous blog and is quickly mutating, releasing two to four new versions per week. This could have been caused by our active effort to fight it the best way we could, so the authors were forced to add heavy randomization and strip all unnecessary parts.
Current versions
The most common "stable" version comes in a self-extracting Cabinet container. Once executed, it drops four files into some strangely named Program Files subfolder, and runs them. The first dropped file is obfuscated and randomized BAT which does the actual etc/hosts injection. The other two files are Visual Basic scripts. One of them loads a text file with URL of an infection counter and sends there a message of successful infection. This way the authors keep track of their malware activities. The second one makes the infected hosts file hidden and creates an empty file etc/hOst where the 'O' is a cyrillic letter. This way the infection is invisible if the Windows is set to its default setting and does not show hidden files.
The second, and we believe still an "experimental" new version, is a bit more advanced. It comes as a self extracting RAR and drops into a Program Files folder as well. It usually contains two executable files. One of them tends to be some clean program freely available at the internet. For instance we saw a Filezilla FTP client, Minecraft game or Windows 8 activator last week. The other executable is compiled by Visual Basic and it does the main job - infects the hosts file by running a BAT, hides it and notifies the infection counter. It is worth noting that BAT of this version is even more randomized. Furthermore this version infects Windows registry and does a check at system start whether the infected hosts file is still in place.

Obfuscated Bicololo BAT file
Methods of spreading
The old versions spread by downloading from hacked websites, significant part of them WordPress or Joomla! powered. The download links look like these:
http://***estylehostel.ru/media/file/index.php?q=%D1%81%D0%BA%D0%B0%D1%87%D0%B0%D1+windows+8&zip=1
http://***enn.ru/blogs/file/?q=%FE%E0%F0+%F1%EB%E0%E9%E4%FB+%F0%E5%F4%E5%F0%E0%F2%2D55479%2D55479&zip=1
http://srv16499.***nkddns.com/download.php?q=asku_na_telefon_ldzhi.zip
The query string can contain URL-encoded name of the container file as well as some simple commands for the generator. This way the final appearance of the virus depends on the URL query and more slightly different version can be downloaded from just one generator which makes the detection more difficult.
The most interesting thing about the newer version is the use of very effective way of spreading. It utilizes hijacked websites as well, but in a different way. If a single URL is used to distribute the virus it can be easily blocked. The problem comes when there are many of them. Malware authors discovered this weakness and used it their advantage. They modified a default site HTTP 404 error (Not found) handler to send the virus. This gives the attackers virtually infinite number of possible URL which downloads the virus! All they have to do is to post some broken links. Here are the examples of such infected sites.
http://***smeigh.com
http://***sgrisparlour.com
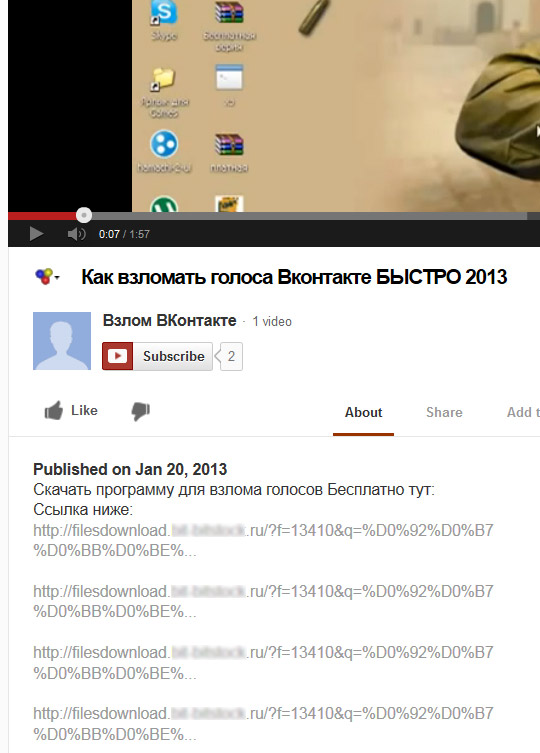
One question remains to be asked. What brings users to those infected URLs? What we've seen is that the virus authors present those URLs as a download links for games, cracks and keygens at many different social sites and forums. We have detected the virus sent as an email attachment or uploaded to a file sharing service as well. Following screenshot shows the virus download links added to a YouTube video presenting installation guide of a voting crack to a Russian social network.
Protection with avast!
This Russian malware family mutates and spreads rapidly. There is no indication this trend should stop. To protect your system against the Bicololo thread we recommend you to use the latest version of avast! with autosandbox enabled, as it successfully detects even the newest Bicololo verisons.