Recently, we've noticed that there are too many legitimate domains popping up in our url filters with malware. At first we thought we had a huge false-positive (FP) problem, but after analysis we found a pattern.
All of the referring links came from the Russian Odnoklassniki server, which is a quite-popular Russian social network. Users of that network are getting fake messages with links to photos.
The links are hosted on domains that look completely innocent, and were registered long ago. But, all of them were 3rd or 4th level domains and all of these led to a few malicious IPs: 69.197.136.99, 94.249.188.224 and 178.63.214.97, 94.249.189.21.
All of the sites we were checking had their XX.YY/www.XX.YY (2nd level) pointing to clean legitimate websites. Only ZZ.XX.YY (3rd level) were pointing to malicious sites. First, we thought about the password theft and modifications of the records on the domain hosting (such as GoDaddy or such, where similar attacks were recorded in the past). But because we were seeing too many of them, we suspected that we needed to look for another explanation.
Then we noticed all the original domains are hosted on afraid.org servers. This service provides free DNS hosting, which makes it very popular for both legal and malicious use. They provide insight in their registry here - most of the top domains are clearly known to any malware analysts for hosting tons of malware. But the domains we spotted were definitely not created for that purpose. We contacted the owner of the service and were surprised by the fact that ANYONE can create an account and create a subdomain for any of the domains hosted on afraid.org. Personally, I think that it's good to have freedom, but we also should have accountability in such cases.
All these 'picture' links host executables from the Bicololo family of Russian trojan viruses, which we first saw more than two months ago. They have several characteristics: The executable is actually a legitimate installer, in this case the Nullsoft Installer. It always drops 3 files to %PROGRAMFILES%\s1\s1 - a .bat, a .jpg and a .exe - and proceeds to execute them in that order. The most important file in attack is a .bat file, in this case named "090909.bat" ( http://www.virustotal.com/file/606d720d0447f00b1df527978174347762b5371160783816b1ed3524c6b66a8d/analysis/1347352288/ ). This file appends IP addresses and host-names of fake Russian social networking and mail sites my.mail.ru, vk.com, odnoklassniki.ru, ... to %WINDIR%\System32\etc\hosts. The batch is randomized to a degree and uses different variable names and sub-strings of the path and URLs in every variant of the trojan.

The .jpg file is only the image file, usually a picture of naked young girl taken from social sites.
The third file is executable file, in this case named "lublu_vinograd.exe" ( http://www.virustotal.com/file/07a63db075fb163f46a6dee091ae5498cf574de6130872d4d99aaca24bbe4b16/analysis/ ). This file is written in Borland Delphi and actually contains mostly dead code from a benign Delphi project - in this case, a "Chart FX 3" tool, and statically linked Indy library for HTTP connectivity. What really gets executed is a small stub unit appended to the neutered program, which sets etc\hosts as hidden, creates a new, empty file in System32\drivers\etc named "hоsts", where the "о" is a cyrillic letter, thus it is considered a different filename and serves as a cover for the hidden infected one, and performs an HTTP request to an obvious "stats" URL, signalling a successful infection to the authors of this malware. It neither replicates nor remains persistent on startup.
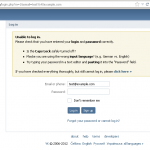
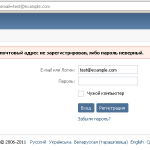
So, at the time of writing this blog post, the purposes of this malware are to redirect traffic of big Russian social sites to the IP of the attackers and credential theft. After the installation, when an infected user visits the social site, he/she is taken to an almost perfect copy of the 2011 Russian version of the site (attacking llamas forgot to change the copyright year on some of the pages and didn't even try to use geolocation to serve the correct language, as regular vk.com is in English when opened from Prague, plus they missed a recent graphical redesign of vk.com).
Real VK.com
Fake VK.com
With the latest defs version, avast! detects the binaries, blocks access to the binaries download, and blocks access to the redirected server.