A laughable fake Avast alert email tries to harvest email addresses via a spam message and leads to several malicious domains.
Guess who hackers disguised themselves as in a recent phishing campaign? That’s right – Avast! A laughable fake Avast alert email trying to harvest webmail addresses is being sent out via a spam message which leads to several domains where attackers have prepared a simple form to collect victims’ email addresses and passwords. This is what it looks like:
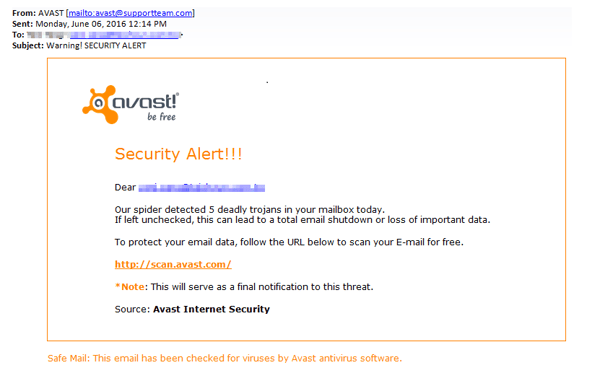
Received spam in a phishing scheme impersonating Avast
The email shows the link as hxxp://scan.avast.com/, but in reality, this fake link directs to several hacked domains (www.hacked-domain.com/index.php?email=victims_email) where a simple PHP file, which immediately tries to support an alert message that your mailbox contains viruses, is located. There is even a list of some file names and their locations.
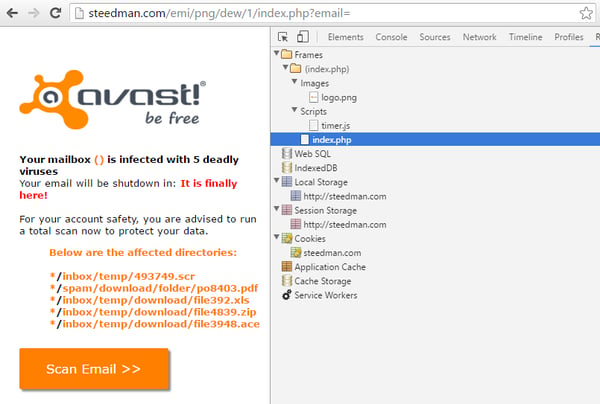
The PHP file is really simple with just one picture and one JavaScript file
Some parts of code in the PHP file are encoded by escape() function. After decoding those parts, it reveals CSS and HTML code. A JavaScript file serves just as delay for the alert "It is finally here!".
There is also a main part in the code of this form, which is <form method="post" action="post.php">, and post.php, where all the magic happens. After you hit ”Scan Email”, the following form will appear.
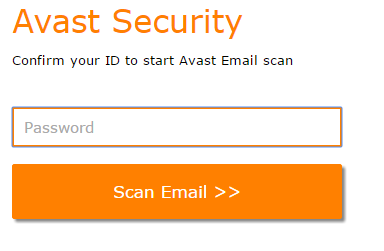
First attempt to gain password
After a password is entered into the form, the victim is automatically redirected to another HTML file. This triggers an error message stating that the user has incorrectly entered their credentials.
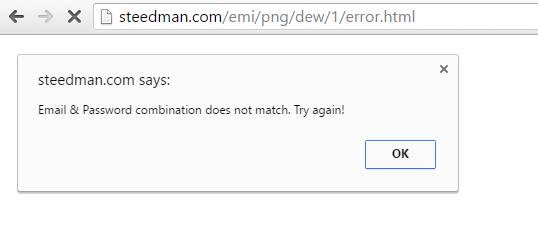
Error message
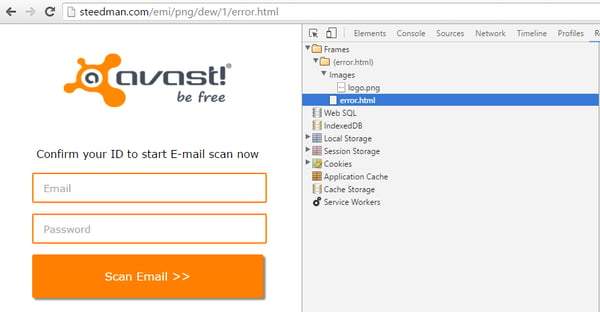
Resources of error.html
The purpose of all the fake alerts is to gain the victim's trust, but it all leads to this last simple form where you enter in your email address and password. This is a typical tactic of cybercrooks.
When your credentials are entered, post.php is called again and the previous alert message is shown once more. At this point, the victim can repeat the process again.
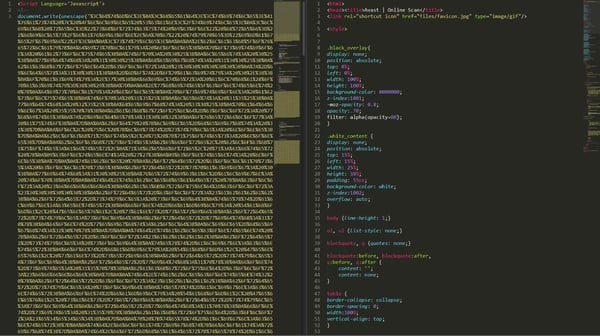
Simple encoding by escape() function
How can I protect myself against phishing scams?
- Protect yourself with antivirus that has phishing and spam detection. Avast Internet Security, one of our premium products, has that protection.
- Beware of unofficial email addresses: When an email is sent from an unofficial address, you can be sure that it’s a phishing attempt or another type of spam.
- Pay attention to the login page’s location: The first thing is to realize where a site’s log in process is located. In this example, the first red flag is the website domain – it obviously doesn’t belong to Avast. Unfortunately, there is no secure protocol that exists as today's standard in log in processes – this makes it especially important to keep your eyes peeled when providing log in info to any website.
- Be suspicious of any “urgent action” required: Attackers like to include urgent "calls to action" in an attempt to get victims to react immediately.
- Don’t give into scaremongering: Emails that make claims such as "your account will be closed" or "your account has been compromised" should get your attention – in these cases, either use extreme caution in responding or simply don’t respond at all. Attackers take advantage of victims’ concern to trick them into providing confidential information. Call customer service instead.
- Legitimate links don’t always ensure safety: Attackers also try to use legitimate links within phishing scams. These authentic links can be mixed in with links to a fake phishing website in order to make the spoof site appear more realistic.
- The devil’s in the detail: Small things, such as typos, poor grammar or low-quality graphics, can indicate that a message or website is fake and/or malicious. Always proceed with caution while browsing online.