Get key info now that the dust has settled in Las Vegas after cybersecurity’s big summer conferences
If you didn’t go to the Black Hat or DEF CON cybersecurity conferences last week in Las Vegas, we’ve got a quick summary of some of the best stories, presentations, social media, and just plain weirdness.
The big story
Millions of Windows users may be vulnerable to a design flaw in drivers made by 20 manufacturers, Eclypsium researchers said in a presentation. (Drivers connect the operating system in a computer with the hardware components.) The issue even involves the Windows kernel – the key computer program that connects all the others – at the very heart of the operating system. The researchers said drivers were all from trusted vendors, all signed by trusted certificate authorities and all certified by Microsoft. Microsoft responded that “In order to exploit vulnerable drivers, an attacker would need to have already compromised the computer.” Read more from Bleeping Computer and PC Mag.
The big theme
There were multiple presentations and news articles about vulnerability in Apple products, which have always been considered more secure than competitors. In one of the most impressive demos, Google Security Engineer Natalie Silvanovich showed how she partially seized control of an iPhone just by sending it text messages. Read more from PC Mag. Apple told Vice that recent software updates fixed the issues presented by Silvanovich. Hackers also showed off an Apple Lightning charging cable custom-modified with electronics that allow it to be used to access any Mac it has been connected to over a Wi-Fi network. Read more from ZDNet. Apple unveiled a new program at Black Hat in which the company is offering special iPhones for security researchers who want to poke around iOS and Apple's hardware to find security flaws. Vojtěch Boček, an Avast Senior Software Engineer, praised the program, which he said is necessary. “While iPhones enjoy a reputation of being very secure, bugs are still regularly found in various parts of their software, just like any other smartphone. Apple does put a lot of resources into securing iPhones as best as possible though, for example they increased the rewards for reported security bugs also announced at the BlackHat conference.”
The best tweet
Amid the self-promotion there is great truth, and wit:
The handiest post
Many security researchers shared new and updated open source tools at the conferences – including a fuzzing framework that helps show driver issues (see the top story above) and something with the atmospheric name Trash Taxi. Bitdefender did a nice wrap-up of the tools here.
The whoops! moment
The plumber has leaky pipes and the cybersecurity conference has a leaky app. At least that’s what one attendee said on Twitter, providing a video that revealed what he said were vulnerabilities. Read more from Mashable here.
The big message
Watch the main keynote address on YouTube here. Dino Dai Zovi, head of security for the cash app at Square delivered the message, “Every Security Team is a Software Team Now.”
These kids today
Teen-age hacker Bill Demirkapi told how he was able to access records for millions of students, everything from their phone numbers to their class schedules, by exploiting common bugs. More from Gizmodo.
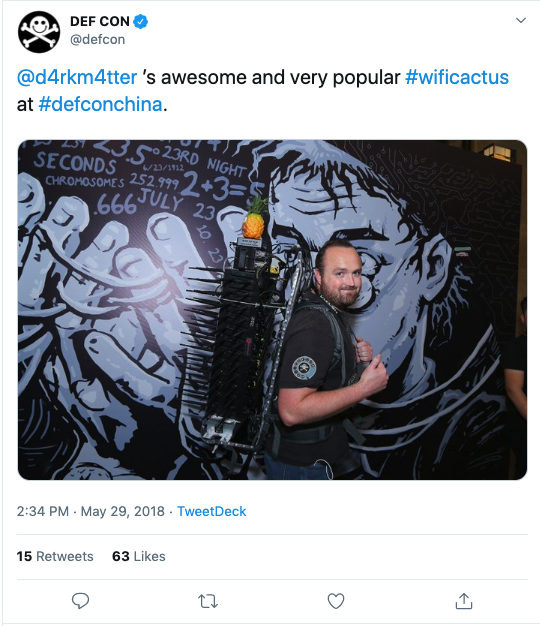
Hacking the hackers
For three years security researcher Mike Spicer wandered around the security conferences wearing a 35-pound surveillance tool he nicknamed the "Wi-Fi Cactus." CNET tells what he learned from analyzing web traffic.
Election hacking fail
The election couldn’t be hacked – and that was a fail. The U.S. government’s $10 million voting machine was supposed to be available for hackers to find security flaws. An unexpected bug stopped the experiment from starting until Defcon's last day. More from CNET here.