While spyware using the Telegram Bot API is limited, it's the first Android Trojan controlled via Telegram’s message-exchange protocol. Avast investigates.
A spyware app communicating via the Telegram Bot API has recently targeted Iranian Android users, uploading extensive personal data about users on a remote server in Iran.
While slightly different versions of the spyware app exist – one promises to tell you how many visitors viewed your Telegram profile, others mask as a Cleaner Pro or Profile Checker app – they all offer the same functions and spy on your Android device. And because cybercriminals don’t have to create their own communication or set up encryption to run the scam (just set up a Telegram bot!), it’s more likely to be used by more bad actors as a ready-to-run “solution,” even if only in the short term.
How does the Telegram Bot API spyware work?
The spyware pretends to be legit and lures potential victims by promising what the Telegram app itself doesn’t provide: the number of people who’ve looked at your listing. Similar scam apps exist for Facebook, promising to show you who has “unfriended” you. Once a user has downloaded it, the app requests your Telegram credentials so it can supposedly retrieve the number of people who’ve viewed your profile. Your score actually depends on a pseudorandom number generator, meaning you can be told you have as many as 9,999,999 viewers.
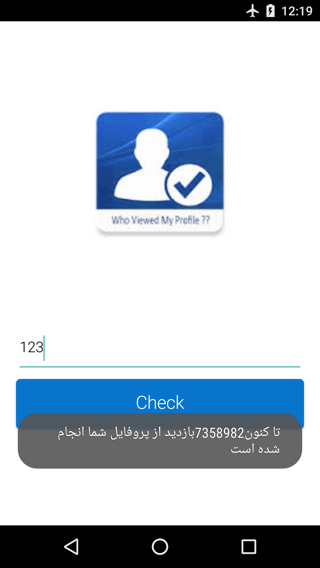 Description: Wow, your profile has been viewed by 7,358,982 people!
Description: Wow, your profile has been viewed by 7,358,982 people!
The app then waits a while, quits, and hides its icon. Now that most victims believe it’s been removed from their device, it can start getting busy in the background.
 The app only hides its icon from your list of apps, but you can still find it under installed apps in your device settings.
The app only hides its icon from your list of apps, but you can still find it under installed apps in your device settings.
Telegram spyware starts by taking your picture, but doesn’t stop there
One of the first things this app does is take and save a photo of you, using your device’s front camera. Then your contact information, incoming and outgoing SMS messages, and Google account info are illegally captured and stored in new, separate files for later uploading to the attacker's server.
Once your device has communicated with the attacker via the Telegram Bot API that it can now send and receive commands, it will upload your text messages (including sender and recipient phone numbers and message contents), list of contacts, Google email address, location, and photo. The attacker can also request files that are yours, not just the ones newly created by the app.
At this point, the spyware developers can send a variety of additional commands, essentially remote-controlling your device, including orders to:
- make a phone call or send an SMS
- forward information about installed apps and available files to the attacker’s server
- upload to the attacker’s server or delete any file stored on device
The attacker isn’t the only one with access to your stolen information
The spyware uploads all files via PHP script and saves them to the /rat/uploads directory on the server. These files are available to anyone who enters the right URL into a browser, likely due to inadequate security measures taken by the attacker.
The script used for file upload is very basic and doesn’t sanitize the input at all. A week after the first posts about this Android spyware, someone had already injected malicious PHP script into the /rat/uploads directory, giving anyone who runs it access to the server's shell in their browser. The server currently looks like a penetration testing school project, meaning several people try and upload more malicious files. Some of them delete the stolen data that shows up in the directory, while others just test what they can do with the server behind the owner’s back.
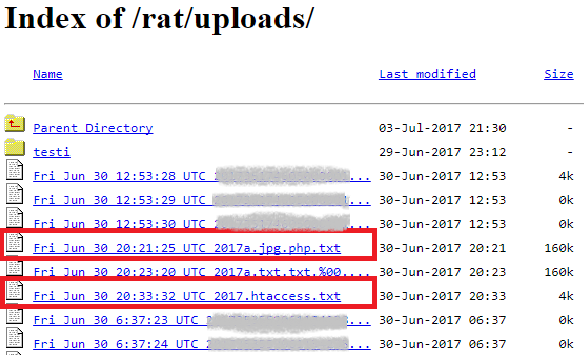 Always make sure your own security is tight before attacking others
Always make sure your own security is tight before attacking others
What you can do to avoid spyware
Following these steps can protect you not only from this particular spyware, but also from most malicious apps.
- Install apps only from reputable sources. (e.g. Google Play). If you really need to allow installation from an unknown source, disable the option once you’ve installed the app.
- Look at the author’s other apps and read reviews, especially recent ones. Is this the author’s only app? Do users say the app doesn’t do anything or that it acts suspiciously? These are both red flags. Also be wary of apps with only a few glowing, 5-star reviews, all published around the same time and using generic phrases such as “Best app ever!,” “Thank you!,” or “Love your app!” These are quite possibly fake. Finally, if there are no ratings or reviews, or if the author has filtered them, reconsider downloading.
- Read the list of permissions the app requests. Does an app claiming it can retrieve your number of Telegram profile viewers really need access to your device’s flashlight, camera, or SMS? If you installed an app and it disappeared from your app list, go to your device Settings and check installed apps there. If it's still installed and only pretends to be gone, you can uninstall it in the settings. Some malicious apps make sure that you won't remove them by installing another executable that will download them again. This spyware makes no such attempts, although its code shows some possible future attempts to clone the app itself.
And it never hurts to have another line of defense, such as Avast Free Mobile Security, which not only blocks malware and viruses, but also lets you connect privately, block calls, and lock apps.
To sum it up, this spyware is stealthy and poses a huge risk to victims’ privacy, leaving unwitting Telegram users on Android open to being tracked, spied on, and robbed of data. Even worse, the attacker’s negligence leaves the collected, sensitive information accessible to anyone.
During our analysis, we also noticed that some samples contained extra capabilities not used in the app, such as the ability to check whether the device is rooted or if the app was run in emulator. This means the spyware is either still a work in progress or that its creator built the app on top of a bigger framework, then decided not to use all of its features. In any case, don’t trust your device or your data to it.
IOCs
Servers hosting the uploaded files:
https://navidtwobottt.000webhostapp.com
http://telememberapp.ir
Telegram bots used:
bot397327632
bot391779082
bot382578708
bot374463427
bot339912423
bot314010881
bot283591101
Samples:
0CFF8D65002CD6DFF2A6F79EEE6A25996AC7622452BC7A08BF55E4C540320812
1D0770AC48F8661A5D1595538C60710F886C254205B8CF517E118C94B256137D
12A89CEF7D400222C61651ED5DF57A9E8F54FE42BC72ECEB756BB1315731F72D
47419E7E531C12C50134D21F486F6C4BF3A11983628D349599C6500ABCDB30F5
BFEB978B3998A18F852BE7012D82CB5C6F14DE67CD4C4521F3D5ACF0B01F987F
05A779F322C281878C6946D7C4B0B0B17A56ADAD29387BDE08F6BF12055BE5C4
ED84D9B0A4C205EA108CD81A856E8027D03719802454A13CB2FCE1B50F257B54
Image: Álvaro Ibáñez