Marriott-owned Starwood Hotels data breach
Another day, another data breach. Marriott-owned Starwood, the largest hotel chain in the world, confirmed that its Starwood Hotels database, which includes information on about 500 million hotel guests, has been stolen in a breach. While specific details remain unknown, the company, in a statement filed with US regulators, said that the “unauthorized access” was detected on or before September 10, but may have dated as far back as 2014. “Marriott reported this incident to law enforcement and continues to support their investigation,” the statement reads.
Over 325 million records in the database contained names, birthdates, physical addresses, email addresses, passport numbers, travel info, and Starwood rewards info. The hotel chain has started informing customers of the breach in the U.S., Canada, and the U.K. Since the breach falls under the European-wide GDPR rules, Starwood, if found to be in breach of the rules, could face substantial financial penalties.
"Hotel chains have been a target of cybercriminals for years due to the valuable information they collect from their customers," explains Luis Corrons, Avast security evangelist. "If you’ve stayed at a Starwood Hotel property in the past, you should take action — inform your bank or credit card provider, and be vigilant about monitoring all accounts for any unknown transactions. Also, change the password for your Starwood account, and any other account where you may have used that same password."
If you were involved in any data breach, follow these steps to protect yourself. After any data breach, always be on the lookout for emails that look "phish-y" as bad actors may start email campaigns which look like they are from Starwood (in this case) and try to steal your credentials by getting you to "log in and confirm your credentials."
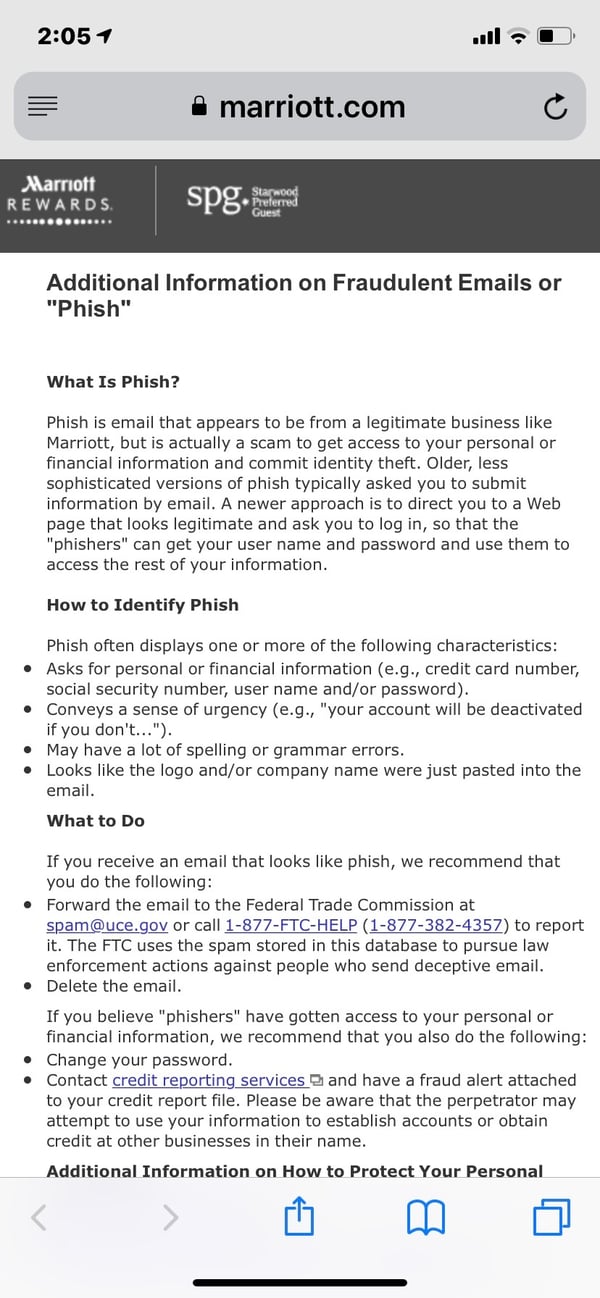 Marriott-Starwood notification on fraudulent emails or "phishing"
Marriott-Starwood notification on fraudulent emails or "phishing"
57 million personal records leaked
During a routine security audit of unprotected servers, cybersecurity researchers stumbled upon an open ElasticSearch server storing the names, email addresses, physical addresses, IP addresses, and phone numbers of almost 57 million US citizens. The server also contained an index of almost 26 million business entries, listing company details, revenue numbers, employee info, NAICS codes, SIC codes, and more. The researchers did their own detective work, deducing that the owner of the neglected server is Canadian firm Data & Leads. When reached for comment, the firm did not respond, taking their website offline shortly thereafter. The leaked info has been turned over to user-friendly database Have I Been Pwned, where anyone can check if their data has been compromised.
The data-farmer in the Dell
All Dell.com customers were prompted to reset their passwords in reaction to a breach that occurred November 9th this year. The company does not share many additional details in their official statement except to say that names, email addresses, and hashed passwords were potentially compromised, and that “there is no indication that any credit card or other sensitive customer information was targeted.” Some cybersecurity experts take issue with the statement, however, arguing that email addresses and passwords are indeed sensitive info. Questions, such as why it took 19 days for the company to disclose the breach to its customers, are still being investigated as the story unfolds.
“If there is any user from the European Union among the affected,” notes Corrons, “waiting 19 days would mean a violation of the GDPR and Dell would have to face a fine. GDPR gives companies a maximum of 72 hours to communicate the data breach.”
When a RAT becomes a worm
Cybersecurity researchers have discovered a fileless variant of the commonly used remote access tool njRAT. The new version of the malware has the ability to spread like a worm, finding its way onto removable drives, where it can stow away to infect more machines. Also going by the names BLANDABINDI and njw0rm, the RAT grants remote access of the infected machine to whoever is sitting at the C&C (command and control server). It’s a remote backdoor, capable of being used to spy on, steal from, and generally control the host system. The advanced malware serves as a reminder that cyberattack strategies are always evolving, as should all users’ cybersecurity.
Avast is a global leader in cybersecurity, protecting hundreds of millions of users around the world. Protect all of your devices with award-winning free antivirus. Create and manage strong passwords using Avast Passwords.
Learn more about products that protect your digital life at avast.com. And get all the latest news on today's cyberthreats and how to beat them at blog.avast.com.