Know how to detect and outsmart any phishing scam.
Gentlemen and Gentlewomen, start your search engines.
Detecting, identifying, and even exposing phishing scams is not difficult these days. All you need is the ability to recognize the tell-tale phishing ploys, and a decent search engine. We had both, so we decided not only to catch a phishing scam, but to trace it back to its source.
In 2017, phishing scams are an everyday occurrence. It’s happened to me, it’s happened to you, and it keeps happening. We receive an email from an entity that looks remarkably like a company with whom we have an account. This entity claims that it IS said company, and that our account is in trouble or somehow compromised. Not to worry, this entity informs us: fixing the matter is easy enough. All we have to do is click the provided link and enter our login credentials.
And once we do that, the cybercriminals have our info. With one click, a Pandora’s box of annoyance and hassle has been opened.
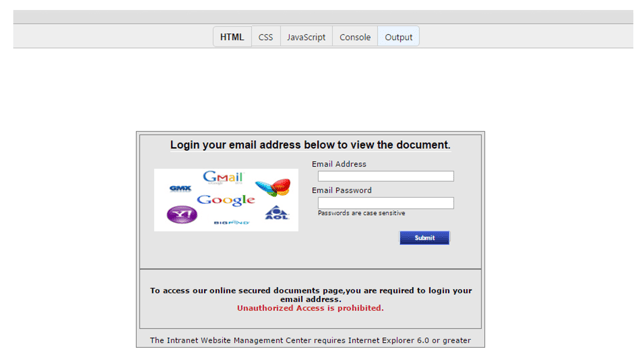 A phishing page that can trick new users.
A phishing page that can trick new users.
How do we recognize a phishing scam?
Good first clue: the phishing email very likely contains low-quality and sometimes distorted images of the company logo. And then you’ll probably notice the HTML tags and typos. Never mind that any experienced user can note the obvious fraudulent elements a mile away. The sad truth is that this tactic continues to work on naive, inexperienced users.
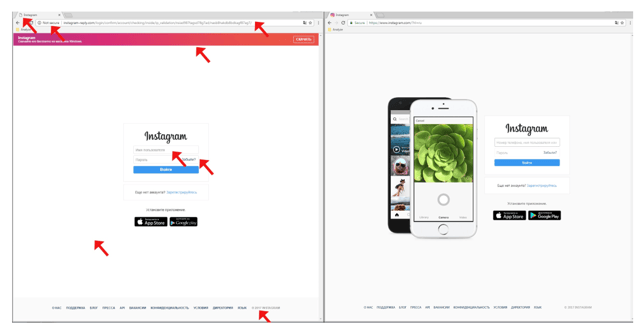 Differences between a phishing page (left) and the original (right).
Differences between a phishing page (left) and the original (right).
In addition to the glaring design mistakes overall, you should also check the URL bar. Secure browsers like Avast will warn you if a web page is not rooted in a secure connection. Then, looking at the URL itself, you will see more clues that it is not the legitimate company it claims to be.
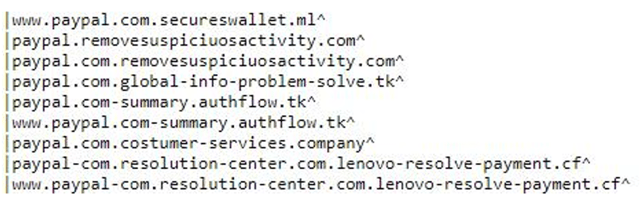 Examples of strange domain names that try to look like PayPal
Examples of strange domain names that try to look like PayPal
Another red flag is Base64. This is an encoding scheme that allows phishing pages to hide a web domain. The link tries to persuade the user into clicking on a link, which may be hidden in an email, document, or web page. An examination of the loaded website will show the phishing link and HTML code, which is hidden in the meta tag data. This is yet another obfuscation technique used to avoid simple detection. If you see Base64 in the URL bar, you know you are dealing with a suspicious link.
 Base64 in address bar
Base64 in address bar
Case study: to catch a phishing scammer.
Our experiment began when we spotted this phony login page:
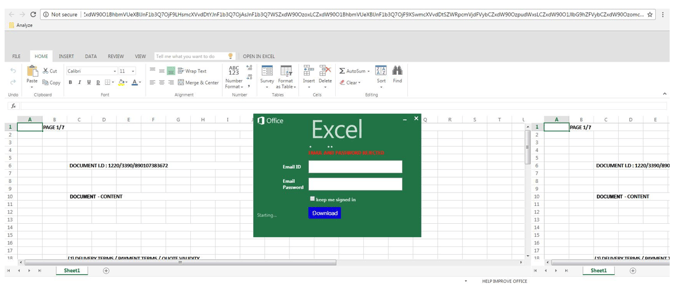 Phishing log-in
Phishing log-in
As you can see, the address bar is full of Base64 code. To the untrained eye, it looks like a genuine URL string. Looking deeper into the coding, we see a form that triggers this:
 Original sample
Original sample
It is a PHP file located at “papyrue.com.ng/cgi/default/mr.php” which typically delivers victims’ credentials directly to the cybercriminals. Avast analysts and security experts see this occur on a daily basis. Continuing our hunt, we used our search engine to find the owner of “papyrue.com.ng.”
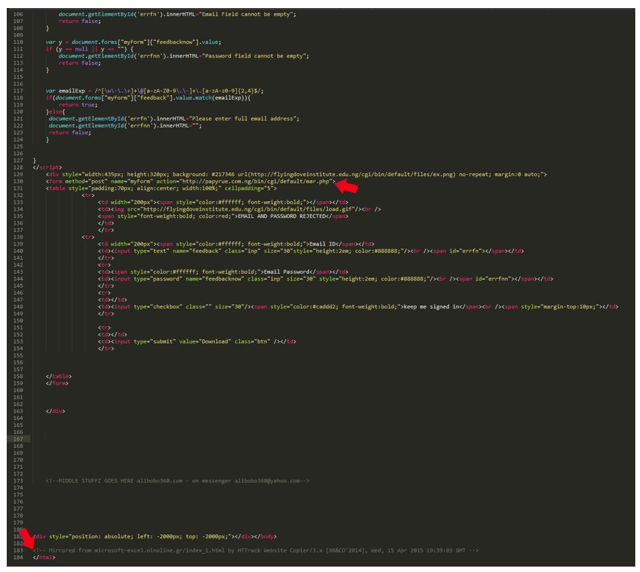 Decoded HTML source of the attacker's site.
Decoded HTML source of the attacker's site.
Using the Whois database, we found that this domain was registered on March 14, 2016 to an individual in Nigeria with his email address.
We decided to dig even deeper.
 Design of papyrue.com.ng
Design of papyrue.com.ng
We were not surprised to find that the papyrue website was flimsy, with an unfinished design. Investigating the phishing server yielded more insights as several other phishing HTML files were discovered.
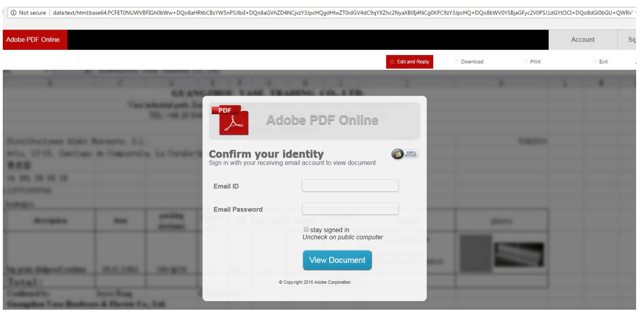 Another phishing page from papyrue, coded in the same style as the others.
Another phishing page from papyrue, coded in the same style as the others.
Phony phishing versions of Excel Online, Yahoo, and Adobe were found in the directory, all holding dangerous PHP files just waiting to be unleashed in someone else’s system.
In some samples we discovered authorship comments from an attacker named “Alibobo.” That name was seen behind many phishing attempts.
 Phishing page developer comment.
Phishing page developer comment.
Who are you, Alibobo?
One sample even contained a link to his website and email. Utilizing our handy-dandy Whois search engine, we discovered that Alibobo is also a man from Nigeria. The Whois report led us to his social networks. His email address was used to register over 19 other domains, albeit inactive ones. But again, this was a search based only on this single email address of Alibobo’s, and you know that in all probability, he held several. Whois also gave us his phone number and other info.
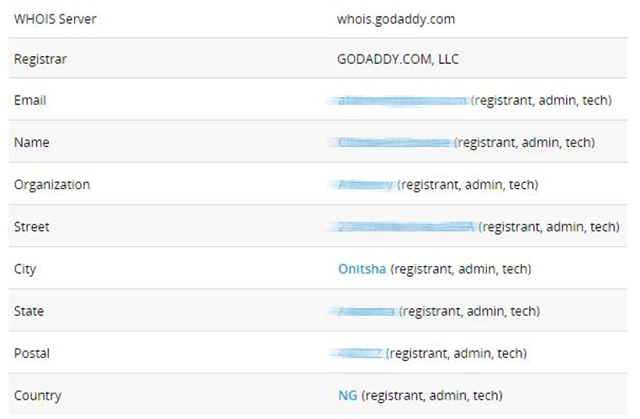 Whois report of Alibobo’s website.
Whois report of Alibobo’s website.
After spending some time with Google, we found even more info about this person: photos on social media, home and work addresses, and even a profile on “freelancer.in” where someone can hire him!
 Alibobo’s freelancer.in profile.
Alibobo’s freelancer.in profile.
At the root of all malware is a money-making racket, which attracts hordes of nefarious coders like our case study Alibobo, and there are thousands, if not millions, like him. Based on his social network activity, it looks that this particular phishing author became more careful over time, but for every cybercriminal that drops out, another drops in.
With a little knowledge, you will never be a victim to phishing. Here are a few good rules of thumb to keep unhooked from any potential phishing scam:
- Question everything, and look closely.
- Never-ever click a link in the body of your email. Instead, open a new browser window and log in to your accounts through the proper “front door.”
- Stay alert, and prove to these predators that despite their best efforts at phishing, you’re never going to bite.