Malicious mobile BankBot Trojan injected into everyday apps, taking advantage of unknowing users whose banking apps could be compromised
Co-authored with Niels Croese (SfyLabs) and Lukas Stefanko (ESET)
Recently, the mobile threat intelligence team at Avast collaborated with researchers at ESET and SfyLabs to examine a new version of BankBot, a piece of mobile banking malware that has snuck into Google Play on numerous occasions this year, targeting apps of large banks including WellsFargo, Chase, DiBa and Citibank and their users in the U.S., Australia, Germany, Netherlands, France, Poland, Spain, Portugal, Turkey, Greece, Russia, Dominican Republic, Singapore and Philippines.
The new version of BankBot has been hiding in apps that pose as supposedly trustworthy flashlight apps, tricking users into downloading them, in a first campaign. In a second campaign, the solitaire games and a cleaner app have been dropping additional kinds of malware besides BankBot, called Mazar and Red Alert (Mazar was recently described by ESET and we won’t dive into the details here). However, instead of bringing light, joy and convenience into their users’ lives, the dark intention of these apps has been to spy on users, collect their bank login details and steal their money.
Google previously removed older versions of BankBot-carrying apps from the Play Store within days. However, several versions remained active until November 17th. This was long enough for the apps to infect thousands of users.
Google has scanning and vetting measures in place for all apps submitted to the Play Store to ensure no malicious programs enter. But in their latest campaigns, authors of mobile banking trojans have started to use special techniques to circumvent Google’s automated detections, commencing malicious activities two hours after the user gave device administrator rights to the app. Also, they published the apps under different developer names which is a common technique used to circumvent Google’s checks.
The malicious activities include the installation of a fake user interface that’s laid over the clean banking app when it’s opened by the user. As soon as the user’s bank details are entered they are collected by the criminal. In some countries, banks use transaction authentication numbers (TANs), a form of two-factor authentication required to conduct online transfers often used by European banks. The authors of BankBot intercept their victims’ text message that includes the mobile TAN, allowing them to carry out bank transfers on the user's behalf.
This malware shows similarities with the kind Trend Micro blogged about in September.
BankBot - Technical description
We spotted the first sample of the new BankBot malware version in Google Play on October 13, 2017. It was hidden in the “Tornado FlashLight” (com.andrtorn.app) and later appeared in the “Lamp For DarkNess” and “Sea FlashLight” apps.

The sample runs undetected without altering the performance or functionality of the flash lights.
The flashlight apps including the BankBot malware
really did have flashlight functionalities
In late October and November, a smartphone cleaning app and multiple Solitaire gaming apps appeared with the malware embedded, for the aforementioned second campaign.

Infected Solitaire gaming app from the second wave
As soon as these apps are downloaded, the malware activates. It checks what applications are installed on the infected device against a hard coded, pre-computed SHA1 list of 160 mobile apps. The package names are hashed, and therefore we’ve only been able to identify 132 of them. This list includes apps from Wells Fargo and Chase in the U.S., Credit Agricole in France, Santander in Spain, Commerzbank in Germany and many others from around the world. You can find a full list of targeted apps at the end of this post.
If the malware is able to identify one or more apps from the SHA1 list installed on the phone, it initiates a ‘service’ - an expression used for an Android application component that can perform long-running operations in the background. The service includes a dropper functionality that allows it to download another application from a webserver in order to install it on the device.
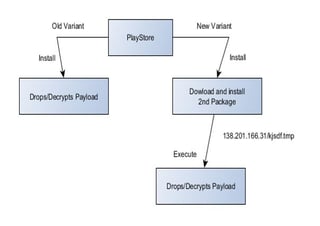
Comparison of the old and new BankBot version: The new variant first downloads/drops the payload from an external source
The malware communicates with its Command and Control (C&C) server through Google’s Firebase service in order to hide and use encrypted communication:
The malware also runs the same check when the device is booted. If it discovers one of the apps on the device, the service will launch.
Once launched, the service will try to trick the victim into giving the app admin rights by pretending to be a Play Store (or system) update using a similar icon and package name:
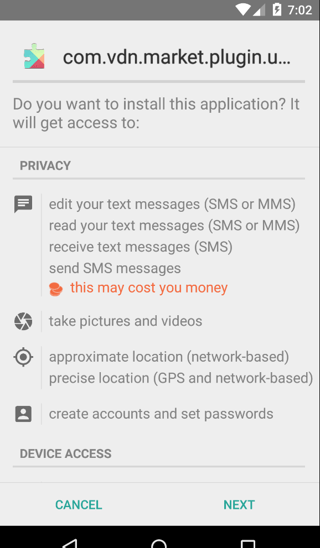
Dropped app imitating the Google design
Two hours after obtaining admin rights the malware will start downloading its payload, the BankBot APK (com.vdn.market.plugin.upd). We believe the cyber criminals use this two hour window to evade Google’s checks. This is the same for all dropper samples and each time the BankBot APK is downloaded from hxxp://138.201.166.31/kjsdf.tmp:
Once the payload is downloaded from the C&C server, the malware tries to install the APK using the standard Android installation mechanism for applications hosted outside the Google Play store. This requires the smartphone to be set up to accept installations from unknown sources. If this is not enabled, Android will display an error and the installation will terminate.
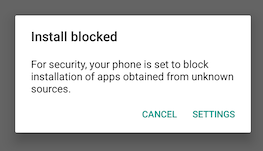
Otherwise, the user is asked to accept in order to continue the installation.
Unlike this newer version of BankBot, droppers from previous campaigns were far more sophisticated. They applied techniques such as performing clicks in the background via an Accessibility Service to enable the installation from unknown sources. Google blocked this service for all applications this fall, except those designed to provide services for the blind. Therefore, the new BankBot version cannot utilize this mechanism any more.
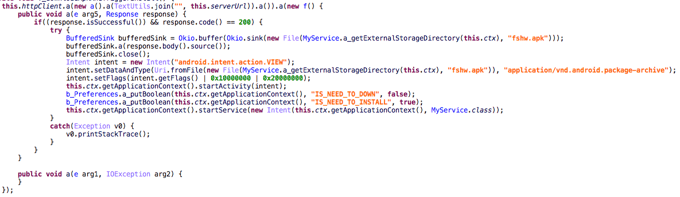
The name and icon of the package to install the malware tries to make the user think it is a Google Play update. Once the installation has finished, the new APK will also request device admin rights.
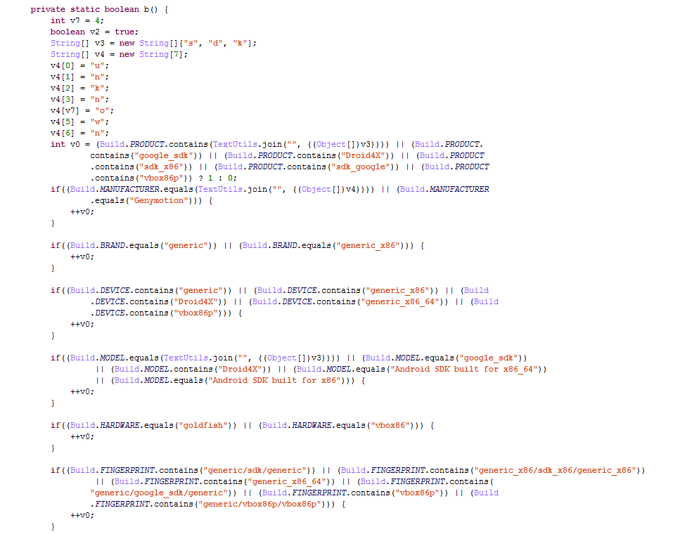
The dropped APK checks for different indicators on whether it's running inside an emulator or directly on the device. These anti-sandbox checks can help the malware bypass or delay detections from different antivirus engines:
When the user opens one of the aforementioned banking apps, the dropped app is activated and creates an overlay on top of the genuine banking app. The Avast Threat Labs tested this mechanism with the app of the local Czech Airbank. In the video below, you can see how an overlay is created within milliseconds. When the user enters their bank details, they are sent to the cyber criminal.
Text message stealing function
Many banks use two-factor-authentication methods to ensure a transaction is secure and initiated only by the bank’s customer. BankBot includes a functionality that allows it to steal text messages, so if the mobile transaction number (mTAN) is sent to the customer’s phone, the cyber criminals behind BankBot can access it and use it to transfer money to their own accounts.
The malware is not active in the Ukraine, Belarus and Russia. This is most likely to protect the cyber criminals from receiving unwanted attention from law enforcement authorities in these countries.
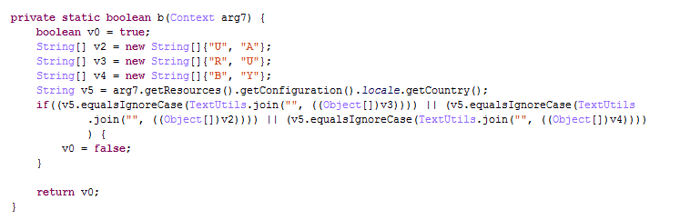
Interestingly enough, even though the dropper apps that appeared in early October have been removed from Google Play, they were not detected by Play Protect which allowed them to enter the Play store in the first place. The same applies for the malware that is dropped by the dropper.
Infected Solitaire gaming app from the second waveFrom the second wave
How you can protect yourself from mobile banking Trojans:
We recommend users take the following steps to protect themselves from mobile banking Trojans:
- Confirm that the app you are using is a verified banking app. If the interface looks unfamiliar or odd, double-check with the bank’s customer service team
- Use two-factor authentication if your bank offers it as an option.
- Only rely on trusted app stores, such as Google Play or Apple’s App Store. Even though the malware slipped into Google Play, its payload was downloaded from an external source. If you deactivate the option to download apps from other sources, you will be safe from this type of banking trojan activating on your phone
- Before downloading a new app, check its user ratings. If other users are complaining about a bad user experience, it might be an app to avoid
- Pay attention to the permissions an app requests. If a flashlight app requests access to your contacts, photos and media files, treat this as a red flag.
- Often, malware will ask to become device administrator to get control over your device. Don’t give this permission to an app unless you know this really is necessary for an app to work.Use a security app like Avast Mobile Security or AVG Antivirus for Android that detects and protects you from BankBot
IOC
(click here for all IOC tables shown below)
Samples in Play Store
First Campaign
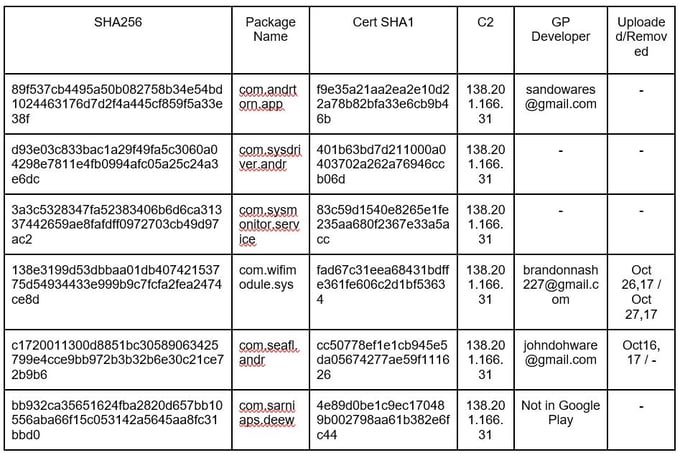
Payload Downloaded
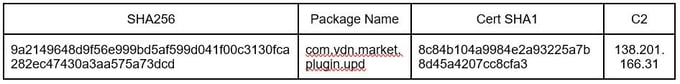
Second Campaign
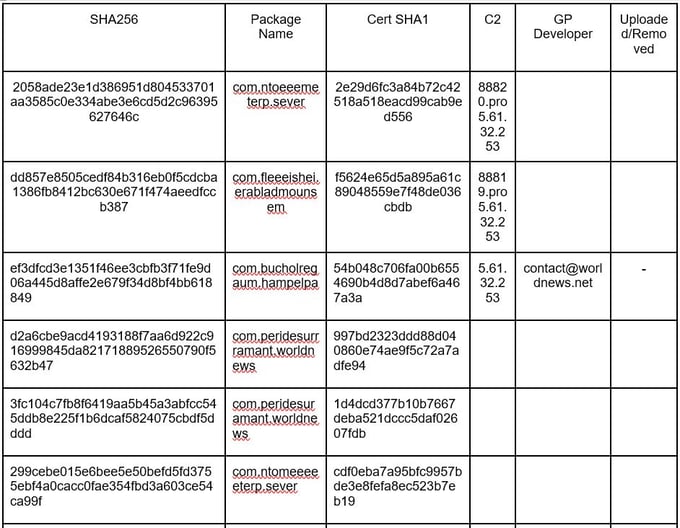

Payload Downloaded

Hosts
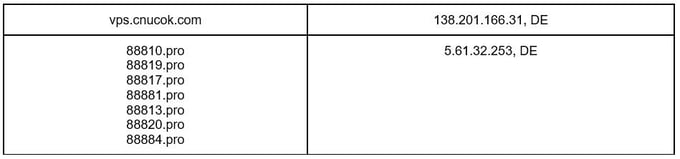
Control Panel

Targeted Apps
ar.nbad.emobile.android.mobilebank
at.bawag.mbanking
at.spardat.bcrmobile
at.spardat.netbanking
au.com.bankwest.mobile
au.com.cua.mb
au.com.ingdirect.android
au.com.nab.mobile
au.com.newcastlepermanent
au.com.suncorp.SuncorpBank
ch.raiffeisen.android
com.EurobankEFG
com.adcb.bank
com.adib.mbs
com.advantage.RaiffeisenBank
com.akbank.android.apps.akbank_direkt
com.anz.SingaporeDigitalBanking
com.bankaustria.android.olb
com.bankofqueensland.boq
com.barclays.ke.mobile.android.ui
com.bbva.bbvacontigo
com.bbva.netcash
com.bendigobank.mobile
com.bmo.mobile
com.caisseepargne.android.mobilebanking
com.cajamar.Cajamar
com.cbd.mobile
com.chase.sig.android
com.cibc.android.mobi
com.citibank.mobile.au
com.clairmail.fth
com.cm_prod.bad
com.comarch.mobile
com.comarch.mobile.banking.bnpparibas
com.commbank.netbank
com.csam.icici.bank.imobile
com.csg.cs.dnmb
com.db.mm.deutschebank
com.db.mm.norisbank
com.dib.app
com.finansbank.mobile.cepsube
com.finanteq.finance.ca
com.garanti.cepsubesi
com.getingroup.mobilebanking
com.htsu.hsbcpersonalbanking
com.imb.banking2
com.infonow.bofa
com.ing.diba.mbbr2
com.ing.mobile
com.isis_papyrus.raiffeisen_pay_eyewdg
com.konylabs.capitalone
com.mobileloft.alpha.droid
com.moneybookers.skrillpayments
com.moneybookers.skrillpayments.neteller
com.palatine.android.mobilebanking.prod
com.pozitron.iscep
com.rak
com.rsi
com.sbi.SBIFreedomPlus
com.scb.breezebanking.hk
com.snapwork.hdfc
com.starfinanz.smob.android.sfinanzstatus
com.suntrust.mobilebanking
com.targo_prod.bad
com.tmobtech.halkbank
com.ubs.swidKXJ.android
com.unicredit
com.unionbank.ecommerce.mobile.android
com.usaa.mobile.android.usaa
com.usbank.mobilebanking
com.vakifbank.mobile
com.vipera.ts.starter.FGB
com.vipera.ts.starter.MashreqAE
com.wf.wellsfargomobile
com.ykb.android
com.ziraat.ziraatmobil
cz.airbank.android
cz.csob.smartbanking
cz.sberbankcz
de.comdirect.android
de.commerzbanking.mobil
de.direkt1822.banking
de.dkb.portalapp
de.fiducia.smartphone.android.banking.vr
de.postbank.finanzassistent
de.sdvrz.ihb.mobile.app
enbd.mobilebanking
es.bancosantander.apps
es.cm.android
es.ibercaja.ibercajaapp
es.lacaixa.mobile.android.newwapicon
es.univia.unicajamovil
eu.eleader.mobilebanking.pekao
eu.eleader.mobilebanking.pekao.firm
eu.inmite.prj.kb.mobilbank
eu.unicreditgroup.hvbapptan
fr.banquepopulaire.cyberplus
fr.creditagricole.androidapp
fr.laposte.lapostemobile
fr.lcl.android.customerarea
gr.winbank.mobile
hr.asseco.android.jimba.mUCI.ro
in.co.bankofbaroda.mpassbook
may.maybank.android
mbanking.NBG
mobi.societegenerale.mobile.lappli
mobile.santander.de
net.bnpparibas.mescomptes
net.inverline.bancosabadell.officelocator.android
nz.co.anz.android.mobilebanking
nz.co.asb.asbmobile
nz.co.bnz.droidbanking
nz.co.kiwibank.mobile
nz.co.westpac
org.banksa.bank
org.bom.bank
org.stgeorge.bank
org.westpac.bank
pl.bzwbk.bzwbk24
pl.bzwbk.ibiznes24
pl.ipko.mobile
pl.mbank
pt.bancobpi.mobile.fiabilizacao
pt.cgd.caixadirecta
pt.novobanco.nbapp
ro.btrl.mobile
src.com.idbi
wit.android.bcpBankingApp.activoBank
wit.android.bcpBankingApp.millennium
wit.android.bcpBankingApp.millenniumPL
www.ingdirect.nativeframe