If it’s free to play, consider the potential cost. Are cybercriminals the real winners?
Who is being targeted?
Late this past summer, we began seeing a new web phishing scam targeting League of Legends gamers. It seems the attackers are predominantly targeting western Europe, with most of the attacks occurring in France, followed by Germany and Spain. And, with more than one hundred million gamers playing League of Legends every day, they are an attractive target for phishing scammers.
The game was released in 2009 by Riot games. Its relatively new free-to-play model at the time made it especially successful in Asia. It is estimated that up to 5% of the total population of Taiwan played the game during peak times. The infographic below shows the popularity of League of Legends, with its number of active users falling between XBox Live subscribers and World of Warcraft players.

Don’t play League of Legends? Your credentials are still at risk.
You might be thinking that a hacker stealing credentials to a League of Legends account is not the same as stealing the login and password to your personal email, correct? Think again. People tend to use one identical password for many different accounts. As recently reported by Dark Reading, three out of five people use a singular password for various services. Thus, even if a game is free to play, the stolen credentials may be valuable if the cybercriminal can use them to gain access to your personal email or PayPal account. It is important to remember that reusing your password for different services is not wise. Instead you should always use strong passwords and make sure to generate unique passwords.
Inside the scam
Let's take a closer look at the League of Legends phishing scam. At first sight, the login page looks compelling and real to an untrained eye. The image quality is not downgraded and the design impersonates the original website quite well. Links to reset your password or to retrieve your account point you to the real website of Riot Games.
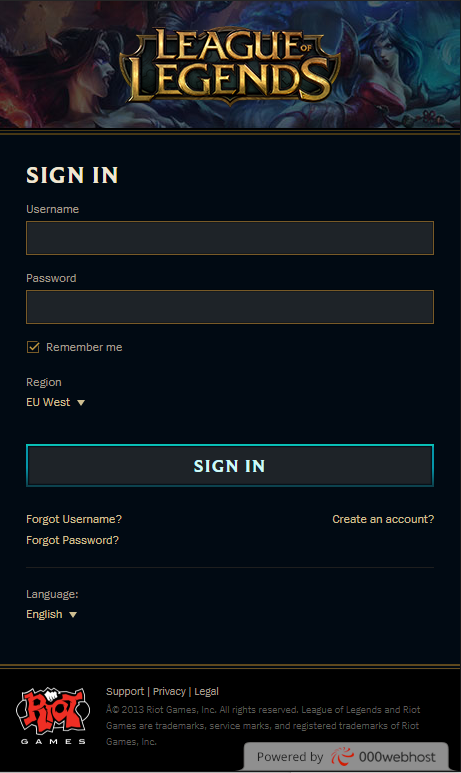
However, after further evaluating the sign-in screen, a huge red flag is easily discovered: the website is being hosted by a free provider - 000webhost. You can see this in the lower right footer of the site. Renowned companies the size of Riot Games rarely use free hosting. And, certain UI elements on the site are not working. It is impossible to check the ‘Remember me’ box, or to select the desired region. This option is stuck on ‘EU west.’ Your suspicion should always be raised if you encounter UI elements that are not functioning properly.
Looking deeper into the HTML code, we can clearly see the link points you only to the top of the page - ‘href=”#”’.
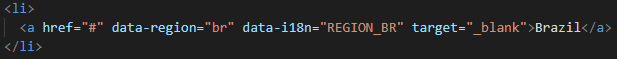
Upon clicking the “sign-in” button, the user’s credentials are submitted to the ‘done.php’ file and likely sent to the attacker’s email or stored elsewhere for later use.
Detecting a suspicious URL
Before we move on, let’s go through some URL essentials. It turns out that knowing the structure of a URL can help you tell potentially suspicious websites from trustworthy ones. In this case, we will focus on the basic parts of a URL: top level domain, domain name, and subdomain. The picture below shows a URL to Avast’s company website.

The top level domain (TLD) is the section that follows the last dot between the slashes. That would be ‘.com’ highlighted in blue above. You probably know many others like ‘.co.uk’, ‘.gov’, ‘.net’ and so on. The domain name is the segment located to the left of the TLD, which is again terminated by dot and highlighted in red above. In general, the domain name is the name of your website, and is typically a company’s name or an associated brand that is easy to remember, like ‘Avast.’ The crucial point here is that custom domain names always cost money. Finally, the subdomain name is highlighted in light orange. This is located to the left of the domain name, and it is terminated by the protocol name - ‘https://’ in the above example.
Subdomain creation is an inexpensive way to develop many independent websites within your domain. You can also achieve more sites by creating different folders. But, subdomains provide an easier way to allocate resources. That is why the subdomain is the only modifiable part of the URL when you use free website hosting. You may be wondering how to tell if a website is using free (instead of paid) hosting. This is never easy. But, here are some of the more common free hosting domain names: 'bravenet', 'weebly', '000webhost', 'x10hosting', 'awardspace', '5gbfree', 'freehostia', 'freewebhostingarea', 'godaddysites'.
Why a website would use free hosting
The main reason many phishing scams use free hosting is money. Phishing scams do not take much disk space and they will not generate a lot of traffic. They don’t need any of the advanced features provided by the paid services. So, free hosting is the most sensible choice. According to the data we gathered from different phishing URLs of the same threat, the League scam is mostly hosted on 000webhost.
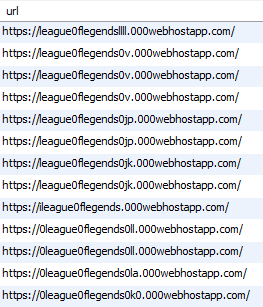
As you can see, cyber criminals tend to make phishing sites look more trustworthy by creating a subdomain name that would resemble the original one. In this example, they bet on the chance that the victim will overlook the hosting site, or that the victim will not know the hosting site, or that it is free. As described earlier, the attackers are trying mimic the real website ‘leagueoflegends.com’ by modifying the subdomain name. You do not have to be a rocket scientist to tell that ‘league0flegendsIII’ looks fishy. In the above image, we see that the pattern is repeating itself over and over again.
This is why some modern browsers are trying to highlight the hosting domain – 000webhostapp.com – in the title bar of the browser. Opera internet browser displays the subdomain name in grey by default as shown below. The Mozilla browser uses a very similar approach.
The Safari browser on MacOS, on the other hand, went in the opposite direction with past updates and shows only the domain name by default. And Google, with its Chrome browser, recently stated that the structure of a URL is becoming too complex for an average user and is considering getting rid of it.
Another advantage that plays in the attackers favor is the SSL certificate that is shown as a green lock in the search bar. It is provided for every subdomain of the 000webhostapp as the default option. Unfortunately, a SSL certificate doesn't necessarily mean you should trust the website. It is merely a sign that the communication between you and the website is encrypted. So, while the information won’t be visible to third parties, the website could still misuse the data you’re transmitting to the website.

4 ways to keep your credentials safe
-
Review the URL: If you are unsure if a website is trustworthy or not, always take a closer look at the URL. Looking at the domain name tells you a lot. If it includes zeros instead of “Os” like in our example “leage0flegends,” something might be wrong.
-
Search the host: It is very rare for a company to have a login at a free hosting site, and while many users may not know any free hosting sites, it is possible to look up the host with a quick Google search.
-
Be wary of fake links: It is very common for a phishing website to have all of the links hat aren’t relevant for the attacker, disabled or not working. Try to click on the “license agreement,” “forgot your password,” or any other links to see if they work. If they don’t, beware.
-
Use a strong antivirus: Using a solution like Avast Free Antivirus ensures the URLs you visit are scanned for suspicious characteristics. Our solution also uses AI and visual recognition to automatically check a site's URL for suspicious tokens, domain meta information, and out of place visual aspects, to keep users protected from scam websites.