We analyzed 100 political candidate websites during the 2018 midterm election and found widespread use of tracking
It used to be so easy to figure out what a web server was doing by examining its underlying HTML coding. Those days are sadly a thing of the distant past. Today’s web servers do so much more: they consolidate a lot of information from various sources, including ad banner networks, images, visitor analytics, tracking cookies, content distribution networks and more. Sadly, this complexity hides a lot of abuses to your privacy.
We studied a group of 100 different political candidate websites during the 2018 midterm elections and found two basic issues of privacy abuse:
- The widespread use of canvas fingerprinting to track visitors
- The lack of accountability to protect visitors’ private data
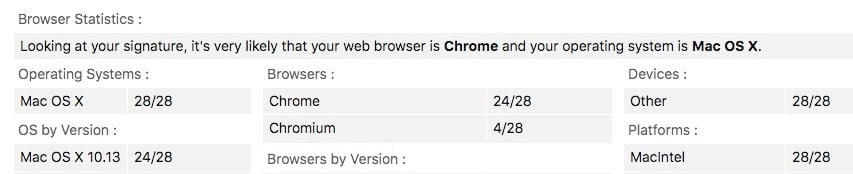
Canvas fingerprinting refers to coordinating a series of tracking techniques to identify a visitor using what browser, IP address, computer processor and operating system details and other details. To give you an idea of the data that the browser collects without your knowledge, take a look at the screenshot below from BrowserLeaks.com. It shows my computer running Chrome on a Mac OS v.10.13 using Intel hardware.
HTML Canvas , along with a variety of other fingerprinting techniques, has been around for several years as it is based on the same programming interface used to draw graphics and other animations using Javascript website developers are getting savvy about how to use it to detect who you are and target you accordingly. In the early days of the web, tracking cookies were used to figure out if you had previously visited a particular website. They were small text files that were written to your hard drive. But canvas fingerprinting is more insidious: there is no tracking information that is left behind on your computer: everything is stored in the cloud. What is worse is that your fingerprint can be shared across a variety of other websites without your knowledge. We found its use on almost every candidate website we examined. And it is very hard to eliminate this information, once you start using your browser and spreading yourself around the Internet. Even if you bring up a private or incognito browsing session, you still are dribbling out this kind of data.
What makes this worse is that more than half of the candidates’ websites we examined did not have any stated privacy policies linked to their home pages. That means they could be sharing your private data without your permission.
These results agree with a similar study done by Ghostery looking at a larger sample of candidate websites for the 2018 midterms. They found trackers on 87% of all websites, with 9% of sites having more than 11 different trackers present. Google and Facebook trackers appeared on more than half of the websites and Twitter-based trackers appeared on a third of the candidate webpages. Republican candidates had 16% more trackers on average than Democrats. (Our research found in general the two parties had similar numbers of trackers.)
Our research also found that some candidates’ websites were using well-known trackers that have had privacy abuses in the past, such as AddThis.
Why are these tracking technologies used? The simple answer is that they want to micro target their campaign advertising and shape the particular ad or pitch they want to show you. They use the canvas fingerprint to collect which news sites you visit, what kind of information you consume, and where you spend your browsing time.
What you can do to stop the tracking
There are two alternative privacy-oriented browsers that you can use to block fingerprinting. One of them is the Avast Secure Browser. This is available on Windows, Mac OS and Android and supports a number of privacy-enhancing features including preventing third party tracking, stopping websites from identifying your unique user profile, a better DNS implementation and built-in VPN. There is also the Tor browser, which has some of these protective features also built-in (and also available for Linux), and various things you can do to harden Firefox browsers.
There are three other tools that can run on a variety of standard browsers: Avast’s AntiTrack, PrivacyBadger and Ghostery. AntiTrack hides your digital fingerprint from techniques like canvas fingerprinting without breaking functionality. You can clear any tracking data and cookies on a regular schedule, be notified of any fingerprinting, and whitelist particular websites that you know are safe.
There are also two browser extensions. Privacy Badger is from the Electronic Frontier Foundation, and is focused on the consumer who is concerned about his or her online privacy. When you call it up onscreen, it will show you a list of the third-party sites and has a simple three-position slider bar next to each one: you can block the originating domain entirely, just block its cookies, or allow it access. Ghostery works a bit differently, and ironically (or unfortunately) wants you to register before it provides more detailed information about third party sites. It provides a short description of the ad network or tracking site that it has discovered from reading the page you are currently browsing. The two tools cite different sites in their reports.
How will this all shake out for the upcoming November elections? There are several things to consider:
- First, assume that every candidate’s website that you interact with will use a variety of tracking and fingerprinting technologies. If this concerns you, you might want to install our Secure Browser or use one of the other browser extensions. Realize that setting any of these tools up will carry some usability tradeoffs and some effort to tune them to your particular needs.
- If you are concerned about the quality of news that you consume, re-read our blog here about how to spot fake news and be more skeptical about what you come across online.
- Next, test what your HTML Canvas reveals about your configuration so you can get a better understanding of what data is collected about you.
- Finally, limit your web browsing on your mobile devices if at all possible. Your mobile is a treasure trove of all sorts of information about you, and even if you are using the Avast Android browser you still can leak this to third parties.