In September 2016, Twitter, CNN, Spotify, and many others were knocked offline by the biggest DDoS attack in history. Today we know it by the name Mirai, but no one would have imagined at the time that this attack was coming from a herd of Internet of Things (IoT) devices cobbled together to form a botnet.
Mirai was discovered by MalwareMustDie researchers in August 2016 . Although it was not the first IoT malware to be discovered, it is certainly the most prominent.
After taking down much of the internet on the east coast of the US, things got worse when the malware creator self-dubbed Anna-Senpai released the source code. Since then, motivated hackers around the world have used it as a framework to create their own variants of botnets. Eventually, the original malware creators were arrested and pleaded guilty in court, but the impact of the code release significantly sped up botnet creation. New variants started to appear, adding new functionality and exploiting a variety of vulnerabilities in unsecured IoT devices.
Any Skiddie can do it
Now we are two years after Mirai, and new variants are still causing havoc, destruction, and harm. Inexperienced hackers are making minor tweaks to the original Mirai code, deploying it, and amassing new botnet armies. In some cases, they even rent them as botnet mercenaries.
One such cybercriminal popped onto the scene in July of 2018 when several new variants of Mirai appeared, causing online discussion among security researchers. One of the participants was a Twitter account with no followers, who pointed out that researchers made a mistake in the Mirai variants classification. To prove himself he released a link with the source code of seven Mirai variants. This challenge motivated us to download the source code ourselves in order to classify and determine how different these seven variants really are from Mirai (spoiler: not that much).
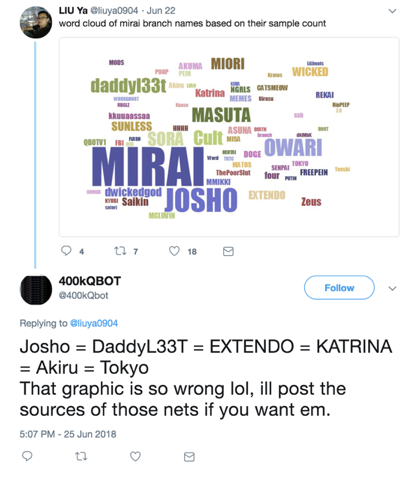 Figure 1. The Twitter handle responsible for the code release
Figure 1. The Twitter handle responsible for the code release
Mirai in a nutshell
To illuminate the differences in the Mirai variants, let's do a quick recap of how Mirai works. The original Mirai code works as follows:
- Scans the internet for vulnerable IoT devices.
- Attempts to gain access by brute force attack using several weak default credentials via the Telnet protocol.
- Successfully infects the device which became part of the botnet and starts to scan for the other vulnerable devices on the same network and performs the brute force attack in an attempt to infect them.
- Periodically, the bot reports to a command and control server (C&C). The C&C might issue commands or instructions to the bot to launch a DDoS attack.
Since the majority of Mirai variants are copycats of the original Mirai code, they have a similar code structure. They have three main parts: the bot, the C&C server, and the loader. The bot part is written in C, and the C&C module is written in Go.
For the purpose of this analysis, we are going to focus on the following leaked variants of Mirai: Akiru, Katrina_V1, Sora, Owari, Saikin, Josho_V3, and Tokyo and their three modules under the bot directory, such as:
- table.c: contains configuration information
- scanner.c: contains a list of credentials to scan with to discover potentially vulnerable devices, as well sending scanning report to the loader.
- killer.c: contains information about which processes should be killed
All decoded passwords, strings, and additional information can be found in the complementary information at the end of this article.
Variant Analysis - What’s in a Name?
The Mirai code is a framework, like a template, and anyone who finds a new way to exploit a new device can simply add it which would create a “new” variant. The key variables in the botnets are the naming as well as the credentials it attempts, the architecture it targets, as well as the ports it turns off (kills) to keep other malware from gaining foothold in the device. To understand the differences between the variants, you can compare them to each other as in the table below.
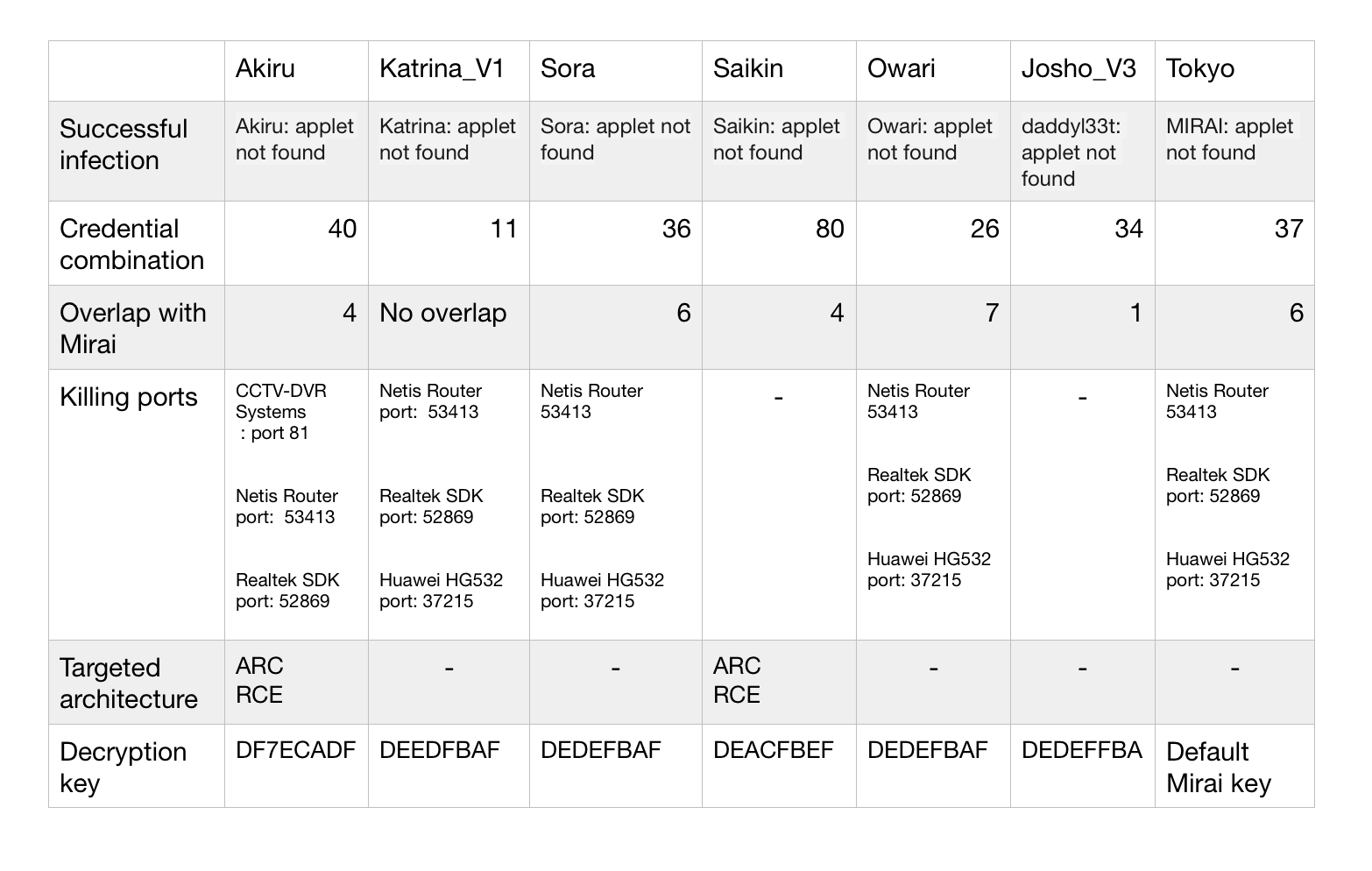 Figure 2: This table contains a summary of changes per variant
Figure 2: This table contains a summary of changes per variant
Now let’s take a closer look at some of the differences.
Naming
All Mirai variants have an implementation of the successful execution check-string. Most of the variant’s check-string corresponds to the variant name. There are several exceptions, for example, the Tokyo variant has a default Mirai check-string, the Sora variant has no name, and Josho_V3 has a completely different name.
Credential Combinations
The original Mirai code used a list of sixty-two hardcoded passwords to perform a brute force attack (dictionary attack) against vulnerable IoT devices. The list is obfuscated and could be decoded with the DEADBEEF key.
By looking at its variants, we can see that the password list changes per bot. We retrieved and decoded all passwords used by each variant in order to find out if the password list was reused from the Mirai code, and if there is any overlap. The biggest password list was implemented in the Saikin variant with eighty passwords, where only four overlap with the original Mirai code. By choosing to implement the different password list, the attacker is targeting different IoT devices.
New Ports
Just like Mirai, all of its variants have a module killer.c which has several purposes. First, it gets rid of other malware possibly running on the current device. Second, it prevents others from gaining remote access to the device over Telnet, SSH, or HTTP. Analysis revealed that in addition to having the standard Mirai kill ports, five out of seven variants (except Saikin and Josho_V3) added a new protocol/device specific ports to their kill lists. These ports are: port 53413 related to Netis Routers, port 37215 related to Huawei HG532 routers, port 52869 UPnP SOAP service from a Realtek SDK, and port 81 for CCTV-DVR cameras. The addition of these ports would allow the botnet author to connect to more devices and at the same time prevent others from connecting to these devices remotely.
New Architectures
All the Mirai variants we looked at are targeting the same architectures as Mirai, and only three of them: Sora, Saikin, and Akiru added two new architectures: ARC (Argonaut RISC Core) and RCE (Motorola RCE).
After examining Mirai and its variants a bit, we became interested in trying to understand who was behind the variants and the twitter handle that shared them.
Going down the rabbit hole to find the skiddie’s name
After reviewing the code, an analysis of which is contained later in this post, it was fairly easy to see that while this code was capable of doing a lot of damage, it wasn’t remarkable in its variations from the original Mirai source code. It took advantage of some of the modular architecture of Mirai to potentially crack new devices and set up defensive posture in the devices that it is trying to infect, but it didn’t present anything that was really new or noteworthy.
What interested us primarily was learning more about how this botnet author worked, so we decided to build a case for determining the identity of the author.
At first, we suspected that the person behind the 400kQBOT Twitter handle is the known threat actor and creator of Owari/Sora who once identified himself in an interview as Anarchy. He was also known as Wicked.
However, by simple googling him, we stumbled upon some other information which seemed to point in a different direction. We found another directory containing leaked source code of Mirai variants that was virtually identical to the samples 400kQBot leaked. Among the compiled sources of Mirai variants, compilers, and tutorials about how-to compile Mirai source code, we found a text file with the following message. The author signed himself as Scarface#1162.
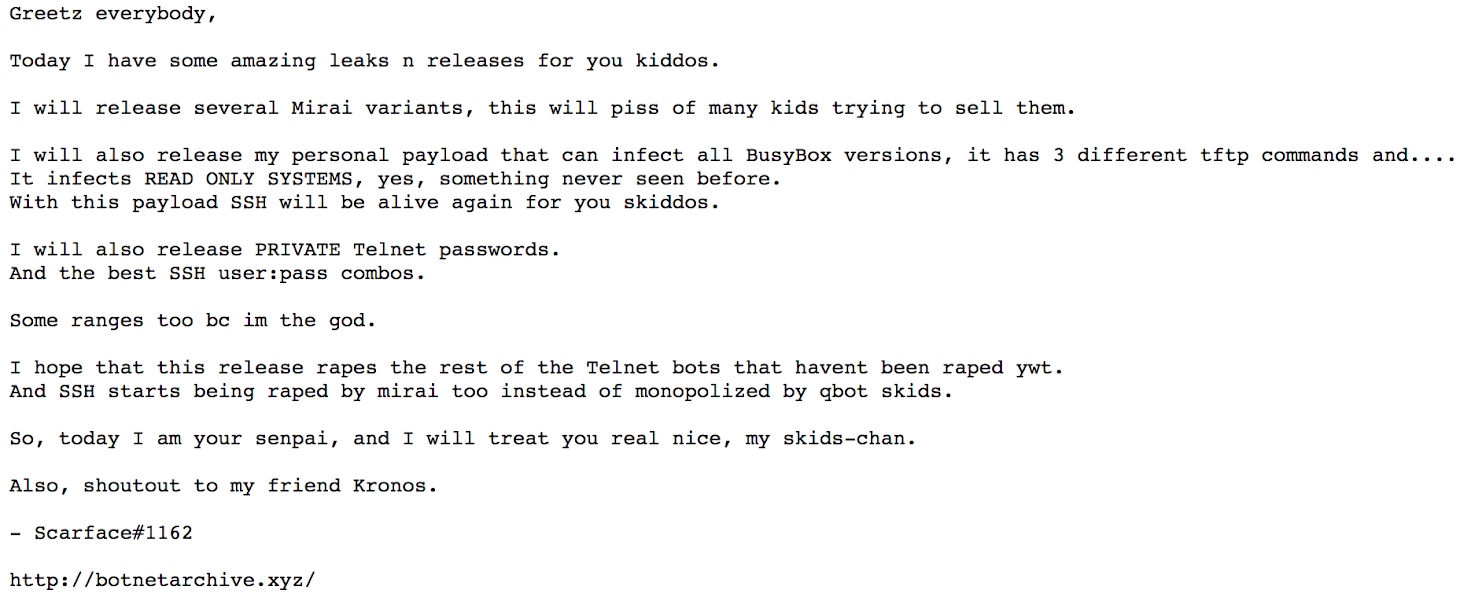 Figure 3: The message from Scarface#1162 the next Senpai to all kiddies out there
Figure 3: The message from Scarface#1162 the next Senpai to all kiddies out there
A simple name search revealed that Scarface#1162 is not only doing “charity” work writing and releasing botnet source code for skiddies, he is also renting access to his botnet as a service.
 Figure 4: Botnet setup service offer by Scarface
Figure 4: Botnet setup service offer by Scarface
He also has a YouTube channel where he demonstrates his hacking skills taking over the botnets of other skiddies. In one video, he shows in real time how he took over the Akiru botnet and then informed its creator, our old friend Wicked, in a chat app channel for “money team staff members”. In addition to Wicked, another familiar name caught our attention: Anarchy. So, maybe Wicked and Anarchy are not the same person after all, but two different people from the same team.
Our suspicions that 400kQbot and Scarface were the same person was confirmed when in mid-September, he identified himself in a tweet from the 400kQBot handle.
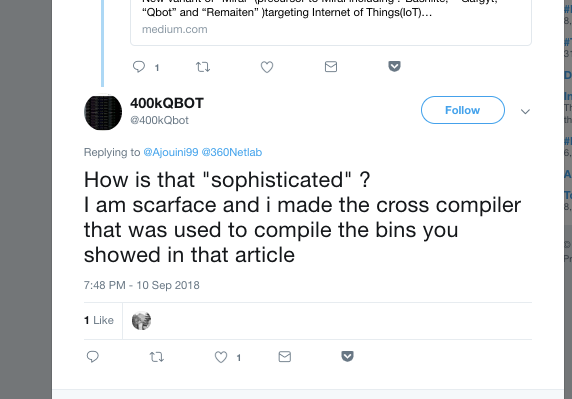
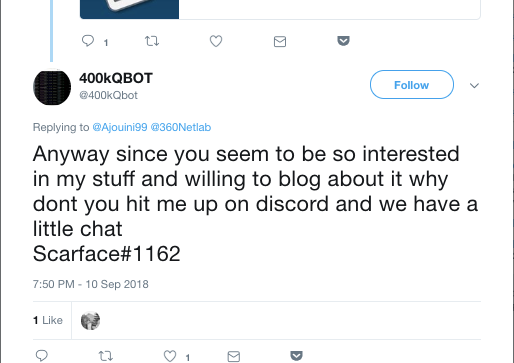
So, now we were on to something. Scarface is emerging as a new and fairly destructive botnet author, and one with a penchant for engaging researchers and press. But we are still no closer to understanding who he (or she?) is.
We zeroed in on a clue we found in researching the code. When Mirai attacks a device, it uses a check string as a sign of successfully finishing a sequence of commands. We have no information how the Scarface got access to these variants, nor we can not confirm if he is the author. For example, one of the variants, Josho_V3, has a different successful execution check-string: daddyl33t: applet not found.
For those who have never heard the story, daddyl33t was a 13-year-old teen looking for a freelance job in development who tried to hone his scripting skills by compiling the QBot botnet. Perhaps the 13-years-old-fame-seeking skid is also a part of a money making team with Wicked and Anarchy. Perhaps they are all the same person.
We find ourselves with several options and connections to consider, but none that point us in a certain direction. Is Scarface trolling us all as he adopts different pseudonyms to go with different malware strains? Is he one and the same as daddyl33T or just mentioning him as a tribute? The exercise left us with some leads, but not enough real information to draw any conclusions.
In the end, it is mere speculation to explore who the real person is behind an anonymous twitter or discord handle, and perhaps that is not the point, but that is also not that material. What is interesting is that it was so simple to create several botnet variants using publicly available code and then market them for profit and attention.
Conclusion
It is laughably easy to create variants of Mirai off the leaked source code, and it is not that surprising to see budding cybercriminals monetizing their botnet armies. A botnet is a versatile tool that can be used to launch a DDoS, cryptomine, or act as a malware proxy.
“I don’t know what to tell people and IoT security is a joke.”
- WICKED, botnet variant author
We are all making heavy use of technology in a time where it’s relatively easy to create malware, and having created it, to rent or sell its capabilities. Anyone can take the Mirai framework add a few passwords here and there, get creative with a botnet name, and it’s show time, ready to infect for fame and profit.
Yet, we are falling over ourselves to fill our homes with devices that literally ARE the playing field for this back and forth game of control over our spare processing power. No dark arts needed here; your IoT devices are up for hire.
Botnet variants like these seven based on Mirai are being honed every day. They are getting better at taking control of devices, kicking others out, and then locking down their position in your device. And, very few IoT devices can be either updated or secured from being drawn into a botnet army.
For decades we have worried about viruses getting access to our PCs and mobile phones. Rightly so, but we seem blind to the irony that we have locked down our laptops only to leave the door to our personal networks wide open in the form of poorly secured IoT devices.
But what is a bit of processing power between friends? Are botnets the victimless crime of the IoT age? Not so. While it is virtually impossible for the average consumer to determine whether their IoT device has been infected by Mirai or one of its variants, there may be a noticeable impact to processing speed, power consumption, and overall performance. As we bring more and more smart devices into our lives, the ability for these botnets to infect, recruit, and attack improves, so does the havoc they can wreak.
If you have a router at home, home office, or small business, you can take these steps to protect your network:
- Change the default admin password for your router and any IoT devices as soon as you get them.
- Keep your devices up to date with the latest firmware updates.
- Disable remote management in your router settings page.
- If you are not certain if your devices have been infected, consider resetting your device to manufacturer’s settings and repeat from step 1.
Avast is a global leader in cybersecurity, protecting hundreds of millions of users around the world. Protect all of your devices with award-winning free antivirus. Safeguard your privacy and encrypt your online connection with SecureLine VPN.
Learn more about products that protect your digital life at avast.com. And get all the latest news on today's cyberthreats and how to beat them at blog.avast.com.