Learn about the dark world of cybercrime as malware developers, scammers, and thieves continue expanding this billion-dollar illegal industry.
For as long as there’s been an internet, there’s been cybercrime. Real-world criminal activity is mirrored in our digital lives. In both worlds, you find stalking, theft, extortion, destruction of property, and scams and schemes galore. And while we condemn all cybercrime, we have to begrudgingly admit that it’s a functioning — albeit totally illegal — industry. Let’s pull back the curtain for a better understanding of this invisible menace.
Web of cybercrime
First, let’s look at the players who make up this unsavory world. Several interlocking branches form this industry that nets hundreds of billions of dollars annually from innocent victims. These branches are made up of the following specialists:
- Programmers are the brains who develop the exploits and malware. But the degree of culpability is grey here, as some developers most likely do not intend their programs to be used for malicious purposes, while others most certainly do.
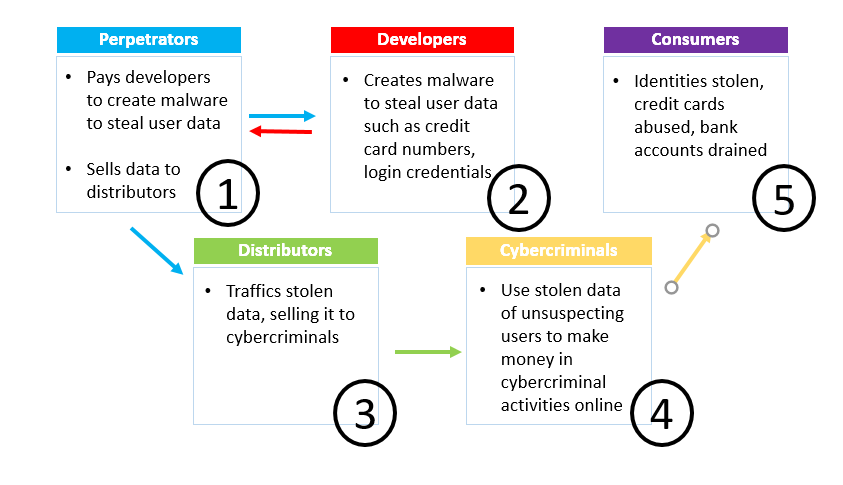
- Distributors trade and sell the stolen data, vouching for the credibility of serious specialists in the field.
- Tech experts maintain the IT infrastructure for the criminals, the same way a legitimate enterprise functions, including servers, databases, security, etc.
- Hackers search for vulnerabilities to exploit in systems, applications, and networks.
- Fraudsters scheme up social engineering tricks for phishing scams.
- Hosted systems providers give safe haven to illicit content servers and sites. Like programmers listed above, some hosts may be hapless innocents whose technology is being abused.
- Organization leaders tie the whole operation together, assembling the team and choosing the targets.
How does it work?
Perpetrators of the attacks are the ones who actually steal information from users. They usually do not develop the malware themselves, but hire developers to create the malware to steal user information online. Once they have the stolen user information, they then sell it on the darkweb to cybercriminals who specialize in using stolen information (such as credit card numbers, login credentials, etc.) to make money.
The evolution of cybercrime
Cybercrime has kept pace – perhaps not surprisingly – with the evolution of e-commerce. As the general public grew more and more accustomed to entering credit card numbers online, cybercriminals quickly realized the impact that some strategically placed malware could have on this new digital marketplace. Here’s a decade-by-decade account of some of cybercrime’s “biggest hits.”
- 1990s -
“Nigerian Prince” and similar email scams
To this day, these emails continue to make lots of money, ripping off everyday people who are caught unaware. The email leads people to believe that someone close to them is in trouble, and so they send thousands of dollars to the rescue. Unfortunately, the money actually goes directly to the cybercriminal and it really just is a money heist.
- 2000s -
Money Mule schemes evolve into ecommerce scams
Often appearing to be legit, money mule schemes became very popular in the 2000s and worked like this: criminals recruited unsuspecting people for what they thought were real jobs. However, once hired, the “mules” were set up to have money transferred to a financial account in their own name; the mules was then instructed to withdraw the money and send it to another contact in another country via Western Union or MoneyGram. This way, the criminal would never get caught.
Later, this evolved into e-commerce scams. The technology was new to everyone — the sellers, the buyers, the banks, the credit cards — so cybercriminals who knew what they were doing got a leg up in exploiting the system, starting with scams where they’d buy stolen credit cards and credential login data from data breaches to order goods and have them shipped to the locations of their choice.
- 2010s -
Online poker and in-app video game crimes
For those that do business in the underworld, a great perk to cybercrime is the relative ease of money laundering. Online poker sites were a notorious hotbed of laundering and fraud until the big FBI crackdown in 2011. Online poker players were targets, too, with cybercriminals going after the large bank accounts associated with their online gambling.
- The latest scams - Online free-to-play video games -
Successful online games lure users in with a free-to-play platform, then hit them with in-game purchases once they’re hooked. These in-game purchases can strengthen the player’s character, put game currency in their wallet, further the story, or any other game-enhancing feature. Do players actually purchase these in-game offers? Yes, they do, to the tune of hundreds of millions of dollars annually.
Cybercriminals are hip to this trend, and they’ve gleefully jumped into the pool. To launder money, they simply need to use their stolen credit card and other personal info to purchase a trove of these in-app items, and then sell them on the grey market to eager players. This scheme both launders money AND turns a profit.
And, with the rise of digital coinage, cybercriminals also are turning to cryptocurrencies to launder money. Whether they are hiding drug-dealing cash or ransomware proceeds, they can use cryptocurrency to obscure their activities by moving it around in an attempt to make it untraceable. Once they deem it “clean” enough, the criminals transfer the cryptocurrency into cash or into their bank accounts.
Where does all the stolen data come from?
So where do cybercriminals find this database of personal info and how do they harvest it? If they want to get their hands dirty and do the work themselves, they can target victims using phishing, email scams, etc. But easier than any of that, they can simply buy these databases online. There are plenty of dark web denizens who aggregate and sell lists of personal user info from data breaches, but some of this dirty wheeling-and-dealing is happening right in your own backyard — Daily Mail reports that social media sites like Facebook are also “widely used to buy and sell stolen bank details.”
Today’s cybercrime on the surface
On a daily basis, 99% of us navigate what is known as the surface web. While the dark web is legendary for being a viper’s nest of criminal activity, both rogue and organized, there is a less well known (yet prolific all the same) cybercrime element targeting the majority of us on the surface where we live our digital lives.
As a general rule, cybercriminals who operate on the surface web have more to gain from smaller financial scores. That is to say, they have more modest means and resources than their dark web counterparts, and perhaps smaller goals. But surface web cybercriminals do have their own community forums where they vouch for each other, sponsor new recruits, and conduct business. For example, cybercriminals may post data samples to illustrate the types of personal info they can harvest. They can also offer demos, discounts, and trials of their services, replicating standard business practice in the legitimate world.
Using law enforcement to tackle crime on the surface web is a challenge due to country borders. Cybercriminals know not to target people in their own country as it would make them easier to track. It’s a much foggier legal dilemma when international lines are crossed in the digital world.
Staying safe from cybercrime
While the existence of cybercrime may be an unavoidable fact of life, the harm it causes is not. You can avoid becoming a victim if you deploy the two strongest defenses each of us have at our disposal — cybersecurity tech and vigilance.
As for cybersecurity tech, crank up all the security measures at your disposal. Change your passwords to be as complex as possible. Better yet, use a password manager, which will not only generate unique, strong passwords for your accounts, but also remember them all for you. Avast Passwords is just one of the many great security measures that come with Avast Free Antivirus.
Also, turn on 2-factor or multi-factor authentication. It’s an extra login step that confirms you are you before granting access to a certain account, such as asking you a personal question or having you retrieve a code from your phone. Most online login setups offer it as an option — you can also search here to see which sites offer 2FA.
Your own vigilance requires you to be savvy with the latest social engineering techniques so you don’t allow yourself to be snookered into one of their traps. Stay alert, and question everything. Follow our social media channels on Facebook and Twitter to be keep updated, educated and aware of the latest cyber scams. The bottom line is that this phantom menace of cybercrime, while invisible, is very real, and we owe it to ourselves to stay informed and protected.