Avast found multiple downloaders on Google Play that can download malware designed to steal Facebook credentials
Multiple downloaders, malicious apps that download further malicious apps to infected devices, have made it onto the Google Play Store. The downloaders are capable of downloading further apps that pose as system apps, some of which are capable of stealing Facebook login credentials. To do so, the malicious apps use social engineering tactics to trick victims into giving them up.
The original downloader apps we found pose as various entertainment and lifestyle apps, such as barcode scanners, voice recorders, and a chess game; targeting English and Vietnamese Android users. We also found additional downloaders uploaded to the Play Store by other developers that specifically target Vietnamese users. Avast has reported the apps to Google and the developer accounts have been blocked.

While the apps do contain some of the features they promote, most of them display an abundance of advertisements, contain code that downloads additional malicious apps, which can trick users into giving up their Facebook login credentials.
There is one app made by developer, Mplus Group, called HayLive that is not malicious. The app looks different from the rest, has a few more users than the other apps, a webpage that goes along with the app, and the app’s APK structure is unlike the others. We can only speculate, but it could be the app developer originally only developed HayLive and it became relatively popular. In order to monetize more, the app developer possibly decided to use HayLive’s success to promote malicious apps via the “more apps from this developer” notification.
Downloading the downloaders
The downloaders (the apps uploaded to Google Play) themselves do not contain any real malicious features, which is how they managed to get past Google’s security checks. The only negative thing the apps do is aggressively show ads. There is a catch though, the apps can download pieces of code to use in runtime or can even download other apps to the device.
The downloaders contact a server setup by the people behind the downloaders, to check a list of available servers and send a request to one of them. The server then gives the downloader a package for it to download on the infected device. The package is outright malicious and if removed, it can be downloaded again, or be replaced with another one.
Gaining admin rights
The malicious apps downloaded by the downloader request device admin permissions right away. If these are not granted, the apps continuously display fake crash dialogues, whenever the user attempts to open any application on their phone. The dialogue usually says the app the user is trying to open has failed and Google Play services have been disabled, convincing the user to activate device administrator rights for Google Play services in order to “avoid unwanted bugs”.
The apps the user tries to open are not actually crashing. In fact, they run normally, but the fake failure dialogue the malicious app puts on top of them covers the apps so that the user cannot recognize something is wrong. This annoyance most likely convinces people to give the malicious app, unknowingly, admin rights, so they can continue using their phone as usual.
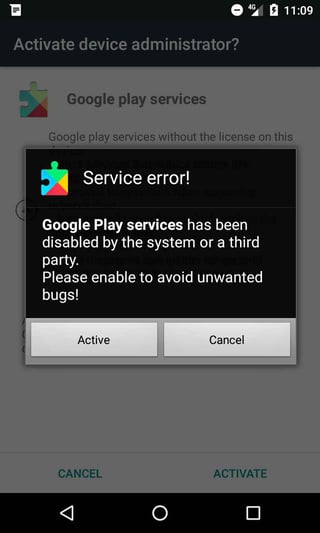
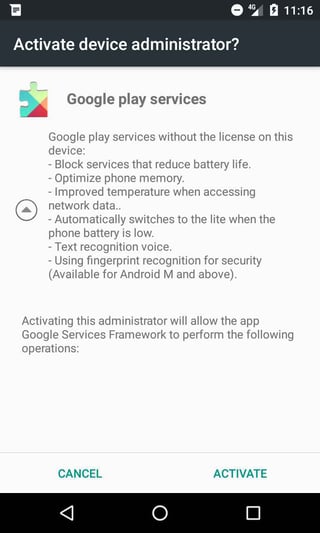
Once the app is granted admin permissions, the dialogues disappear and a request is sent to the server, letting the server know the rights have been granted (/manager/update_state.php).
I spy your location
The downloader app collects information about the device, such as unique device ID, location, language and display parameters. The device’s location is obtained from the IP address that is used when contacting online services that offer geolocation information for IPs. The services the app uses are:
freegeoip.net
ip-api.com
This method does not require the app to have permissions for accessing the device's coarse or fine location, but it can only be used when the device is connected to the internet. If the user is using a VPN, this method will report the location of the endpoint the device is connected to through the VPN service.
Information about the device is sent to a server (/manager/insert_device.php, manager/get_facebook_ads_manager_v4.8.php). Data regarding the device’s location is frequently reported as an update to the server, tracking the victim whenever they are connected to the internet.
Stealing Facebook credentials
The malicious apps go even further and steal Facebook login credentials. The apps, however, do not steal the credentials from the Facebook app itself, nor do they abuse any system or app vulnerabilities. Instead, they trick the user into giving up their credentials by pretending to be Google Play services or another app that many users will most likely recognize and trust.
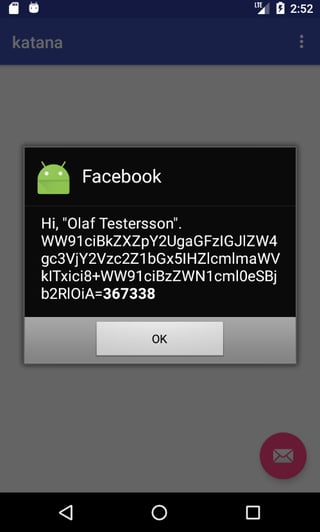
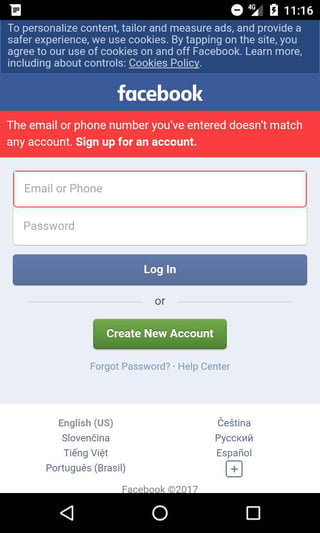
The dialogues used claim there are issues with the user’s Facebook account, for example, someone tried to hack their Facebook account and it has been suspended or the server is unavailable. These dialogues are shown to worry the user.
The malicious apps swiftly load a webpage with the mobile version of Facebook to “check” the issues. The activity even emulates Facebook’s official loading screen and it's not a fake page; it's the actual Facebook welcome screen for mobile devices (m.facebook.com), including the Facebook login form. However, the page is viewed within the malicious app as a WebView object and the app can therefore inject JavaScript code into the page. When the user enters their Facebook login credentials, the app steals them. There is actually no problem with the account or server, the messages are just a scare-tactic used to convince the user to sign in to their account.
This way of stealing Facebook credentials is not very unusual, but it’s becoming more popular. This is most likely due to developers using embedded web browsers (WebView, WebChromeClient) in their apps, instead of opening the webpage in a browser. Widespread use of this method means developers are more likely to find ways to exploit features in embedded browsers, such as injecting JavaScript into pages loaded in the embedded browser. The option was always there, but now it is being abused, because the feature is popular that using it won't raise any flags. If only one developer were using WebChromeClient and injecting malware using JavaScript, the abuse would be flagged early on and the technique would be easily recognized, but when many developers use the feature, it's harder to single out abuse.
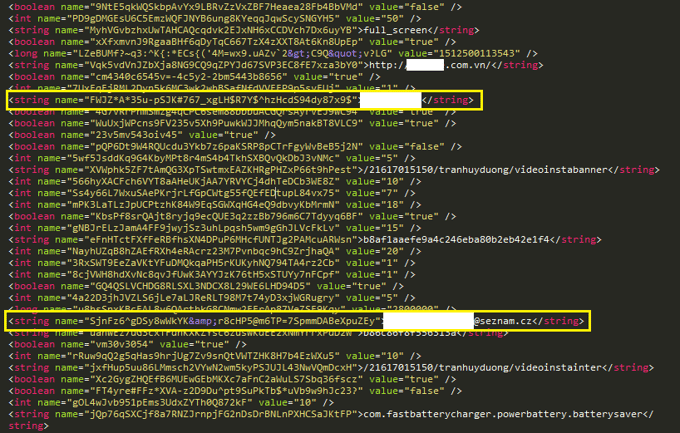
Above the malicious apps’ SharedPreferences XML file created when the credentials are entered into the Facebook login page. The password and email are saved along with info received from the server, which include a list of packages to download.
The stolen credentials are saved into the SharedPreferences of the malicious app and are sent to a remote server. The connection to the remote server is done using HTTP, which is unencrypted, meaning if someone is monitoring user’s communication, they can also steal their credentials in plaintext.
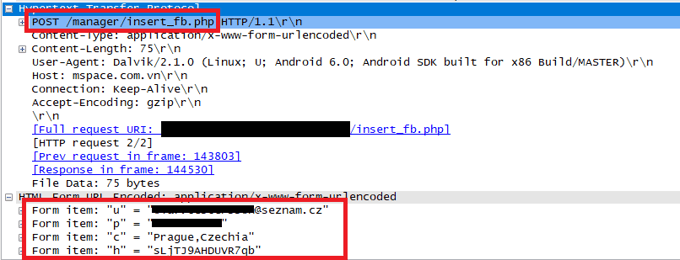
The credentials are sent over an unencrypted channel to the server.
Although Facebook can detect and block account logins if it suspects the account’s credentials were stolen (usually in cases when the user’s credentials are suddenly used on the other side of the world), this login activity will most likely not raise any red flags because it is coming from the usual location and device used by the user.
Selling shares
The Javascript within the malicious app usually clicks on share buttons within the Facebook webpage on the user’s behalf and goes through the user’s list of friends.
The page identifier part of the Facebook URL for a targeted application is sent to the device from the server (/manager/get_push.php). This way, the developer can offer these shares, likes or even generic comments to businesses or users looking for quick promotion from real users. They are authentic users which means they won’t be flagged as fake accounts by Facebook’s check and their value is also therefore higher. Going through users’ list of friends and accepting all friend requests or adding all suggested friends can make the collected accounts more valuable, as they will have greater outreach and the shares can be sold for even more.
Ads and uncaught exceptions
The apps contain several advertising platforms that can display ads and video ads, and also contain a feature that enables the app to click on the ads shown within it. The apps manipulate the device’s keyguard, turning on the screen and dimming its brightness so that the user doesn’t realize the malicious app is secretly clicking on ads on the user’s behalf.
If an uncaught exception, or problem, occurs in the app, a full stack trace (a full report) is retrieved and reported to the server so the developer can fix the problems.
Vietnamese and English users targeted
The original entertainment and lifestyle apps we discovered target both Vietnamese and English speaking Android users.
All alerts and messages in these downloaders and the additional apps they download are available in both English and Vietnamese. The apps try to determine the user’s location by checking the location, the language the phone is set to and who the mobile operator is. Depending on the outcome of these checks, the apps display in either Vietnamese or English.
So far, users around the world have encountered the app, presumably because they are available in English.
We suspect the people behind the malicious apps are Vietnamese. In addition to most of the *apps* being in Vietnamese, another hint that points to this is many of the downloaded apps use package names of popular Vietnamese apps.
There are clues that suggest the various other downloaders uploaded under different developer accounts, which we discovered later on, were uploaded by the same person or group that uploaded the original downloaders we discovered. The apps contact the same server and contain code nearly identical to the original downloaders. Further hints include some of the downloaders contacting a different server with the exact same interface and scripts used by the original downloaders.
How to protect yourself from downloaders and other bad apps:
- Download an antivirus app, like Avast Mobile Security, which will act as a safety net and protect you in case you run into a malicious app.
- Whenever possible, visit the homepage of an established company, as they often promote their mobile apps on their websites and download the app straight from the source.
- Always read both the positive and negative reviews, before downloading any app. Even if an app has positive reviews, one can usually tell if these are fake or genuine; fishy positive reviews can be a sign that an app shouldn’t be trusted.
- Carefully check the permissions an app is requesting. If an app requests permissions that don't make sense and don't seem necessary for the app to function properly, you should think twice before downloading it.
---------------------------
IOCs:
http://mspace[.]com[.]vn
http://optimuscorp[.]pw
APPS:
Downloaders on Google Play that downloaded malicious APK:
com.azmobie.blockhexa EFCA498B6A6715337CDEDF627690217CEF2D80D1C8F715B5C37652F556134F7E
com.bestsoftfree.audiorecorder F3223010D0BEACE2445561BCB62FFAA491423CAD0B94CA0C811A8E165B9B94A8
com.softedu.sieumaytinh 3D04094251D48AC7F42D52FA460AB46384AF656581EC39D149F76DB8DCA058AE 50CAD37A8FC9E317FD521F32A2ADAA0B2B5013832864DEEDD10B078A7F661CF4
com.goodtool.studio.app.tool.Share.TransferFile 0E7DF5409D657205BB82A2698D0E18B3A6F42B6A82C82C5FFEEEC45D0970C6B4
com.cosy.app.tool.compass 17D788D6A77E4BB2A59562EBAC24568337B095CA9E63E6A1559AC3ADFEC26FE3
Apps on Google Play that contacted the same server, downloaded, but failed/decided not to process/install/save:
com.cosy.app.tool.home.Touch.Assistive E69C1BD90B6CAE22DC7968657F3A550D584D9747F6D9FDC62DFE6C66AD7DCC0E
com.cosy.app.tool.Brightest.led.Flashlight EA9C392D1779E3630053BF5B469E2AE10FDABC90D27030F1812791D32E0E3B54
Downloaders (have the capability) that did not download:
com.azmobile.chessmaster 8C34B7D233868811AF12364FF783FB9CDDBD8D900B6FEE7285723F4190E9721C
com.calendar.appfree.lichvannien 79529115E98401C15AC23803E095234619FB326E40EF2E6FD166A8D67F74A573
com.lichcom.tuvi.lich.mautuat 2A714C1BB6EF061D6BCF0AFBFA4B7609CCD40D0EB4C13F15143652C034B02402 77A67D58CBCA8E3F50329EAD2F6DBA6B75833AE6E240FB1BEF0E5027EAA14146
Downloaded files:
6F3E51FB8545D29BB5A5B93672A887462417096C741358C2BAF92872778D6232
45543FA9D222AE4B1932E9D44EDB895FF5BB2E1CB3F4A64E781F1B6EC921A374
10F54212197D5D4AB7E16E1E193D9B9F8EAB742D977AB0E37DF75516EBA5F23A
5F6497BAB8B6C74E1658D74F05C012619423AA8CE07E419329887D7CA43C7718
F041BAE2BFBE0CB07FC3687D5EF0EA03350C682B332A60DAD3BD11D6244CD41E
B984502129DBDEA1889A3BC36EF1F82377F5529809A555FEA0FAEA370D1ADE57
D153F355BB0C87F4BAA592858E8C891919B214605F62567E05447E98A5AB6729
F295571354ABD1E707E2E39BFB9367280DDAA9221E385C5EA6DAB05327A500CB
2247DE4714949A2ADE55020622B50CE7BDBCF46770EBC0E2D79C861DDE48F9B3
D716394A6C036000448B632C470E311DDA4028BE0836E53FB72E83D7D3F0CFA2
B296A79BFFDC166A27855ED0C1639C64659688108D56C45819D36F81571F0833