Many ignore everyday warnings, but this one from the FBI is one you should take seriously
UPDATE June 18th: US consumers who practice poor router security are at high risk from cyberattacks designed to take over their connected devices, steal passwords and gather other sensitive personal information. Half of people surveyed (51%) in the US by Avast, the global leader in digital security, have never even logged into their router’s web administration interface to change the factory login credentials. And, 72% have never updated their firmware. Given the vulnerabilities users face with VPNFilter, it is highly recommended to update your router firmware and change your router admin password. See the article below for the full story.
UPDATE June 6th: Many more devices are affected by VPNFilter than originally thought. Ars Technica estimates that over 200,000 additional models may be affected. Click here for the full list of routers.
The FBI recently issued an immediate call-to-action for every small office and homeowner out there: power cycle (reboot) your router ASAP. The malware is coming. Chances are your router might be hiding in plain sight — you probably take it for granted since it just does its thing — but it needs your attention, and the sooner the better. If you are like many, you don’t always update your router firmware (only 14% of those recently surveyed have done so). Or, change the default administrator password (only 18% of those recently surveyed have done so) according to Broadband Genie. But, this time, you really need to.
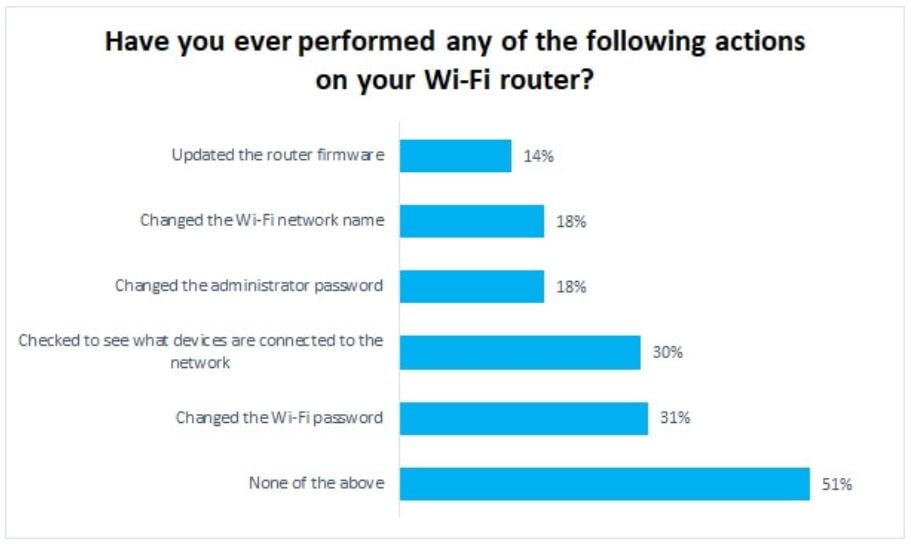
Source: Broadband Genie survey, April 2018
So what happened?
Across the globe, cybercriminals have used VPNFilter malware to compromise about 500,000 home and office routers, as well as other networked devices.
What exactly does VPNFilter do?
This malware is capable of several nefarious actions, including rendering the router inoperable, possible information collection, device exploitation, and blocking network traffic. Worse, this malware is not limited to a particular router manufacturer (so far Netgear, TP-Link, Linksys, MikroTik, and QNAP have all been confirmed as affected), and may also include routers you got directly from your internet service provider (ISP). This malware has also already been known to infiltrate a network-attached storage device of at least one manufacturer.
In short, both size and scope of this malware attack are significant.
How can I protect my router from VPNFilter malware?
If you have a router at home, home office, or small business, you should take action as soon as possible by following these steps to protect your network:
- Reboot your router.
Turn it off, wait 10 seconds, and then turn it back on.
- Change the admin password on your router. (And, make sure it is a unique, strong password - tips on how to create a good password here).
- Disable remote administrative access whenever possible.
- If you want to go all out, consider resetting your router back to its factory settings. This will take some time as you will need to implement all security patches for your router and then setup your Wi-Fi again so that all of your devices can easily reconnect. We recommend that you check your router documentation or contact the manufacturer and follow the steps carefully to do the reset and reconfiguration.