Plus, data-stealing apps target Twitter and Facebook users, a ransomware attack affects over 100 nursing homes, and the FBI warns the auto industry about cyberattacks
Microsoft’s security team released details about a new malware that uses sophisticated and stealthy tactics to evade detection, ZDNet reported. Dexphot, as the malware is called, runs a complicated series of actions to infect and hijack the system for crypto-mining. One of the operations employed is known as process hollowing, a fileless technique for making use of legitimate system processes by hollowing them out and filling them with malicious code. Another operation of the Dexphot malware is polymorphism, a technique that uses different names for the malicious files in an attack, varying them from one attack to the next so they cannot be added to security nets. Both of these tactics make detection especially difficult. The malware also burrows into the system’s scheduled tasks, setting up a re-infection failsafe in case any of the malware’s processes get disturbed. Once the malware senses it is being threatened, it terminates all malicious functions and then reinfects the system. With researchers tracking Dexphot since October 2018, Microsoft noted that the malware reached peak volume in June 2019 when it infected almost 80,000 systems in one day. Since then, Dexphot attacks have been dropping in number.
This week’s stat
91% of people have left a website that was slow to load, a Harris Poll shows.
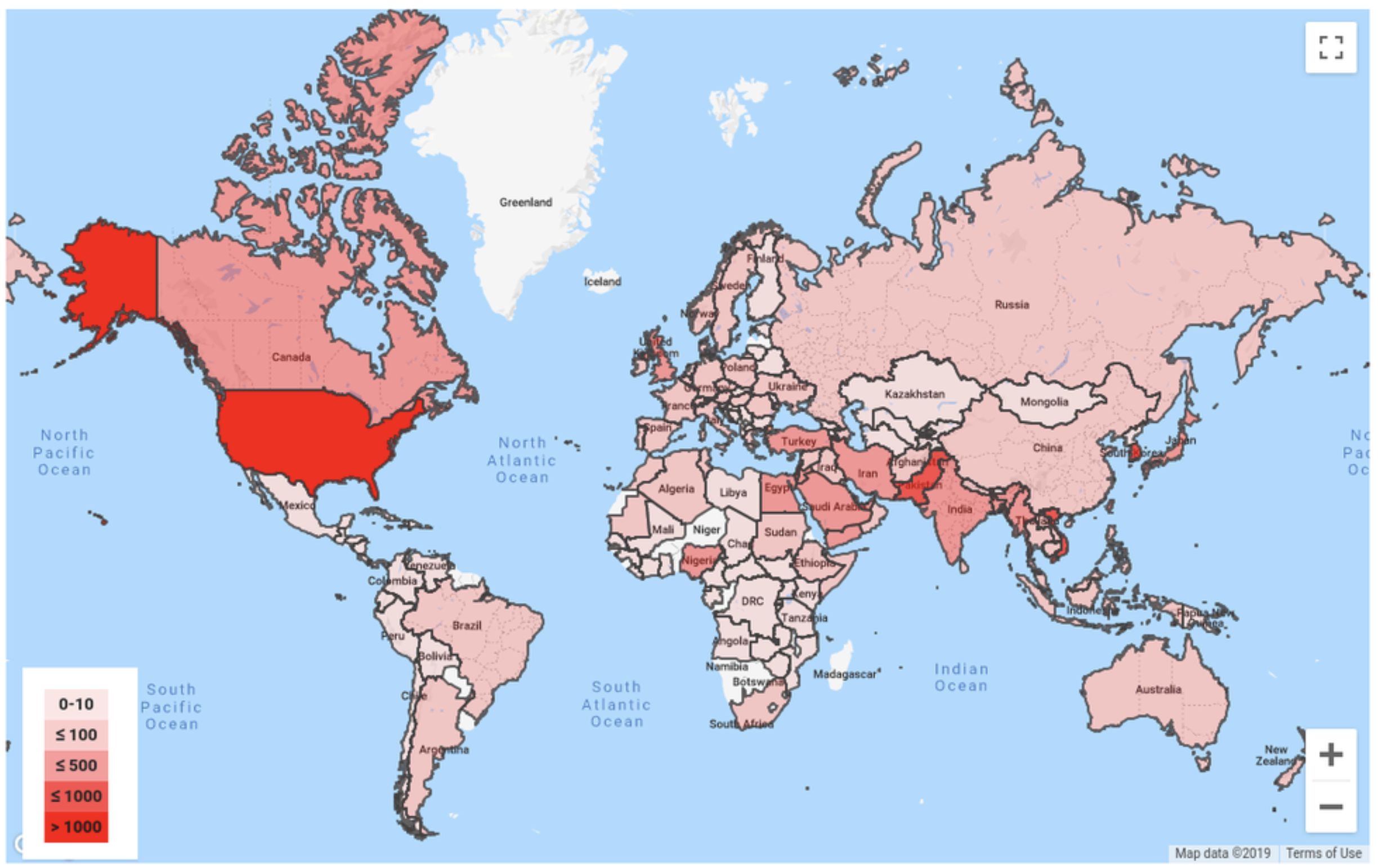 Google graphic
Google graphic
Google gives details on state-sponsored phishing
In a blog post this week, Google explained a security operation the company ran from July through September in which it sent more than 12,000 warnings to users in 149 countries that they were targeted by government-backed attackers. The targets of that hacking are shown in the Google graphic above. Google said over 90 percent of these users were targeted via credential phishing emails. Read more.
Twitter and Facebook say third-party apps harvested data
Social media giants Twitter and Facebook each issued a statement informing users that certain third-party apps have been illegally harvesting user data. The Twitter notice reported that a malicious software development kit (SDK) has been collecting users’ email addresses, usernames, and most recent tweets. An SDK is a prefabricated toolkit that developers can place in their apps or programs to save the time it would take to write that particular code by hand. Users affected by the data collection are those who use their Twitter account to sign into apps that use the malicious SDK. CNBC reported that Giant Square and Photofy are two examples of apps tainted with the malware. Twitter stated there is evidence that the malicious SDK accessed Android users’ accounts, but not iOS users, though it has alerted both Google and Apple so each platform could handle the issue as they saw fit. Similarly, Facebook discovered that malicious SDKs were pulling private information from users. In a statement to CNBC, the company claimed the malware was collecting profile data such as name, email address, and gender. It has removed the tainted apps from its platform and issued cease-and-desist orders to the malicious developers. Both companies said they would alert users whose information had been compromised.
Ransomware attack affects over 100 nursing homes
A Russian hacking network is demanding $14 million in ransom from an IT service provider to over 100 nursing homes across the U.S., The Milwaukee Journal Sentinel reported. Milwaukee-based Virtual Care Provider Inc. (VCPI), a company that provides online security and data storage to nursing homes and other post-acute care facilities, was hit with a ransomware attack that caused certain locations to lose access to patient records, medical files, internal payroll, and internet service. Some residents of these facilities could be at risk if certain critical information such as medication requirements are inaccessible to facility staff. Security experts discovered that the attack was hatched over 14 months through phishing emails. Attackers may have suspected VCPI was a large enterprise because it consists of 80,000 computers throughout 45 states, when in fact it is a medium-size business that does not have $14 million to pay the ransom.
This week’s quote
"Far from assisting in fixing vulnerabilities, Corellium encourages its users to sell any discovered information on the open market to the highest bidder." – Apple in a lawsuit to stop a new open-source security tool that replicates the iOS operating system
FBI details cyberattacks on U.S. auto industry
The American auto industry is a perpetual target of cyberattacks, according to an FBI bulletin obtained by CNN. The bureau disseminated the bulletin to a select group of automotive leaders, informing them that since late 2018, hackers have launched cyberattacks in the form of ransomware, phishing, and brute force attacks against businesses in the industry. Many were successful, exfiltrating sensitive information, conducting fraudulent wire transfers, and locking up computers in a demand for ransom. In one case, the victimized company paid the ransom yet never received the promised decryption key. The FBI did not identify the hackers, but warned that the trend is expected to increase as the amount of internet-connected vehicles and autonomous vehicles grows. Luis Corrons, an Avast security evangelist, said the attacks are pervasive across industries today. “The attacks described by the FBI are the same kind of attacks that other industries are also suffering, from healthcare to finance to government. The cybersecurity challenges are bigger than ever, especially for businesses.”
This week’s ‘must-read’ on The Avast Blog
Black Friday and Cyber Monday bring big sales – and risk to consumers. Make sure your privacy and banking information are protected with our Black Friday checklist.
Avast is a global leader in cybersecurity, protecting hundreds of millions of users around the world. Protect all your devices with our award-winning free antivirus. Safeguard your privacy and encrypt your online connection with SecureLine VPN. Get advertisers off your back and disguise your online identity for greater privacy with Avast AntiTrack.