Several block puzzle games in the Google Play Store now come with a side of malware.
Authored by Alena Nohová
Google Play Store advertises various versions of block puzzle games — Block Puzzle Jewel, My Blocks, Block Puzzles, Block Puzzles Free, My Puzzles, etc. — and aside from all of them being easy-to-understand games with very simple graphics, they share another trait, a hidden one. When a user downloads one of these games, they get the game they chose … but with a little extra.
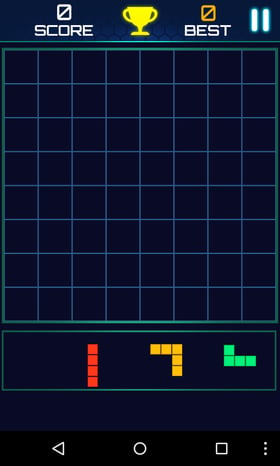
Getting a foot in the door
After downloading and installing one of these game apps from the Play Store, the user can launch and play a simple block puzzle game — just as they expected. While the user is playing the game, however, the app starts a countdown. After a certain amount of time, gameplay is interrupted by a system alert window.
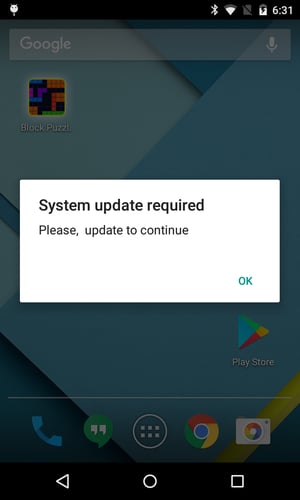
What the user doesn’t know is that the game included malware that will try to convince him or her to download an “update,” which is actually not an update at all. In fact, it’s a new app disguised as an update, and it carries a malware payload that can affect the user’s system in many ways.
How cybercriminals get a fake update installed
The fake system alert and following fake update prompt take over the screen. The app is trying to make the user believe that, while he or she was playing the game, Google Play Games decided to check for updates and found one, and now Google Play Games wants to install the update. In this case, the user should notice the suspicious behavior: The game was closed without warning, and there is no option to dismiss the system alert and install the (fake) update later.
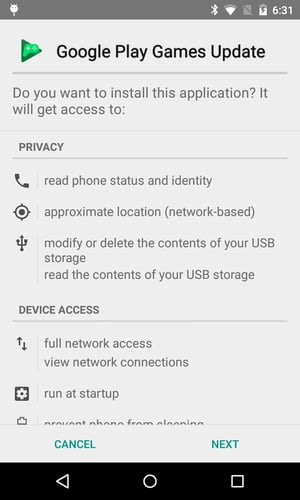
Update alert window with Presented with an “Update”
no way to close out but it is a fake app
Developers know that we’ve all gotten used to frequent app updates – you see them on your phone all the time. There's usually at least one every day or two, and it always works the same way: There’s an update, you confirm installation, it's downloaded in the background, and installed. If things go smoothly, your interaction with the updated app will only be interrupted for a few seconds, because that's what REAL developers want to achieve.
So, the fake app developers are taking advantage of this and attempt to use the “update” process to get their malware onto a phone without alarming the user. And there’s a good chance that the installed malware payload won’t be noticed for weeks, or even months.
Another approach is to scare the user. If they are presented with a decision under pressure that will either save their precious phone data or make it disappear within 16 seconds, that user may very well go through with the installation of the fake update, but will regret it soon thereafter. When the stress is over, the user might question their decision. A quick Google search on the symptoms the phone is exhibiting will show that something malicious has indeed happened to the device.
Scaring a user is easy, but walking through the front door dressed like a delivery man with a package for a user who is used to receiving packages on daily basis is smart. The only requirement is that the app attempting to smuggle the payload as an update onto a user's phone has to mimic the interface of the phone.
The most important decision the developer needs to make in order to successfully sneak onto an unsuspecting user’s phone is picking the right app to “update.” It’s usually an app that’s either preinstalled on all Android devices (Google Play Games, YouTube, Hangouts, Maps) or a very popular app among users in the targeted region (Facebook, WhatsApp, Messenger). Avoiding the system apps and apps that use the custom icon designs across different versions and GUIs (Camera, Calculator, Clock, Gallery) is a safe bet, but even those can be piggybacked on if the user is not vigilant.
How to determine if you have installed a fake app
If you want to be sure you did not install a fake update, you can check your app list from your phone’s Settings. If you see an app name followed by another app of the same name with “Update” appended to its title, it’s most likely a fake update app that you should uninstall.
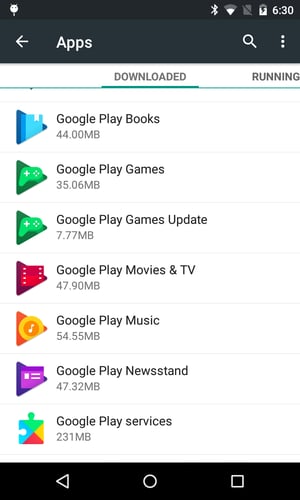
List of apps on Android phone Fake app
Update your apps safely
If there is a real app update available from Google Play, you would see either:
- a notification from the Google Play app that can be dismissed, or
- an in-app notice letting you know that a new version is available in Google Play.
Interrupting the user interaction while in another app without any option to dismiss the update alert is not standard protocol and should always be a red flag. If the update alert contains lots of exclamation marks, warnings and threats to your device ("Install this critical system update to prevent your battery from exploding now!"), or a countdown that claims your phone’s data will be lost ("Your SIM will be corrupted and all your data lost in 54 seconds"), do not install "the update.”
Apps never install a standalone update app when they push new features or bug fixes. If that were true, after a few months, your phone would be plagued with hundreds of WhatsApp Update Update Update apps.
If you are unsure about an update, you can always go to the Google Play Store on your device and check for available updates manually. If the app was downloaded from the Google Play Store, the updates will also be distributed via the Google Play Store. Most importantly, the updated version will replace the current version.

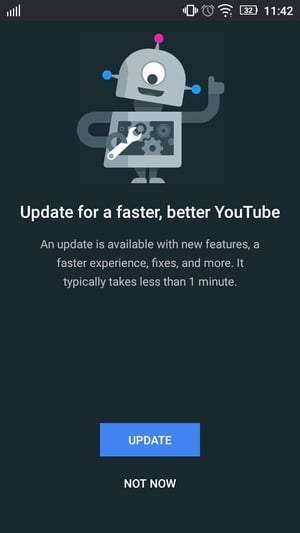
Updates screen on Android Example of a legitimate app
update screen
In the case of in-app alert, the app should not force you to update immediately by showing the same dialogue every minute, and it definitely should not prevent you from closing it.
All that work for a few ads
These puzzle games and their fake updates were collecting location and personal information about the user’s phone and uploading it to a remote server. Many apps use advertising frameworks and networks that profile the user in order to offer targeted ads, which is fine as long as the user gives consent. A legitimate app would never go around permissions and query some IP-based location service instead, which is what these puzzle games apps did.
The worst offense of these puzzle games is their ability to download any malicious code from a remote server and run it on the device. This capability opens the door for further exploitation of the device. In the case of these block puzzle apps, the malicious payload floods you with ads. But that payload can change any time, for instance, when this monetization model becomes less effective for the developer. If the remote server gets compromised, the app may actually update itself, becoming a cryptomining malware or ransomware in the future.
What starts as a simple diversion to waste a few minutes can turn into a full device lockdown, affecting you for much longer than a few minutes. For now, leave the block puzzle games alone.