Avast now offers ransomware victims 14 free decryption tools to help them get their files back.
In 2016, ransomware once again demonstrated that it is the biggest security threat. In the past year more than 200 new strains of ransomware were discovered, it’s growth of in-the-wild samples were two-fold, but the good news is that hundreds of millions of Avast and AVG users were protected against this popular threat.
We are committed to fighting back against ransomware and one of the ways we are doing so is by providing free decryption tools to ransomware victims.
Today, we released another three ransomware decryption tools for the following strains: HiddenTear, Jigsaw, and Stampado/Philadelphia.
We would like to point out that there are free decryption tools already available for these strains. Security researchers Michael Gillespie and Fabian Wosar did a great job and provided their own decryption solutions for these strains. Kudos guys!
Now you may be wondering why we decided to release tools for these strains, if other tools are already available? Well, it’s always better to have multiple (free) options and to find the one which works best to you.
- All three strains are quite active (and prevalent) and have been for the past few months. The used encryption keys, as well as the inner algorithms change, a lot. This means that we need to update our decryption tools too. Therefore, there is a fair chance that either our solution or existing ones will cover the latest versions of these strains.
- Last but not least, we were able to significantly speed-up the decryption time, more precisely the password brute-force process, so e.g. some of the HiddenTear variants will be decrypted within minutes instead of days. The best results are achieved when decrypting files directly from the infected machine.
All the decryption tools are available, together with a detailed description of each ransomware strain on our free ransomware decryption tools page.
If you are infected by a version of HiddenTear/Jigsaw/Stampado that is not covered by our tools, please, let us know in the comment section below and we will try to update the tools.
HiddenTear
HiddenTear is one of the first open-sourced ransomware codes hosted on GitHub and dates back to August 2015. Since then, hundreds of HiddenTear variants have been produced by crooks using the original source code. HiddenTear uses AES encryption.
File name changes: Encrypted files will have one of the following extensions (but not limited to): .locked, .34xxx, .bloccato, .BUGSECCCC, .Hollycrypt, .lock, .saeid, .unlockit, .razy, .mecpt, .monstro, .lok, .암호화됨, .8lock8, .fucked, .flyper, .kratos, .krypted, .CAZZO, .doomed.
Ransom message: After encrypting files, a text file (READ_IT.txt, MSG_FROM_SITULA.txt, DECRYPT_YOUR_FILES.HTML) appears on the user’s desktop. Various variants can also show a ransom message:
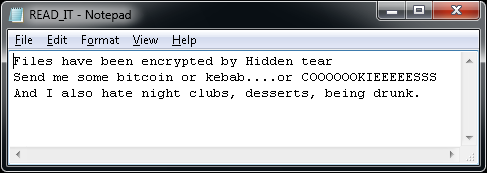
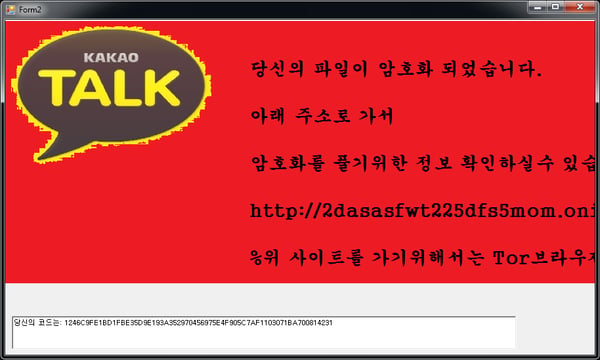
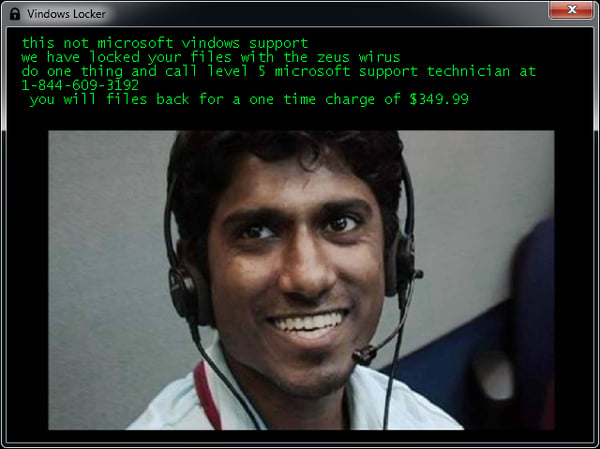
Some versions of the ransom message even scares victims into thinking Windows’ support team locked their computer.
Jigsaw
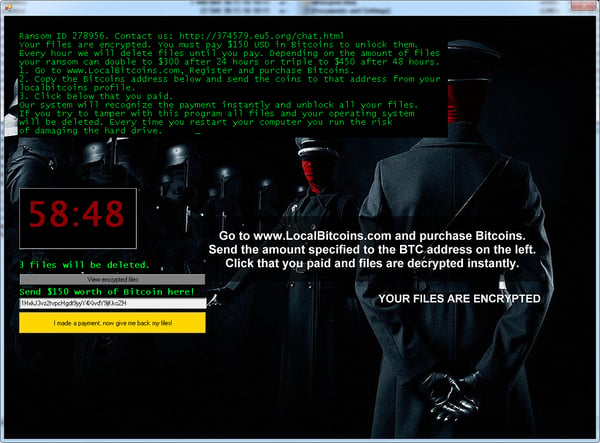
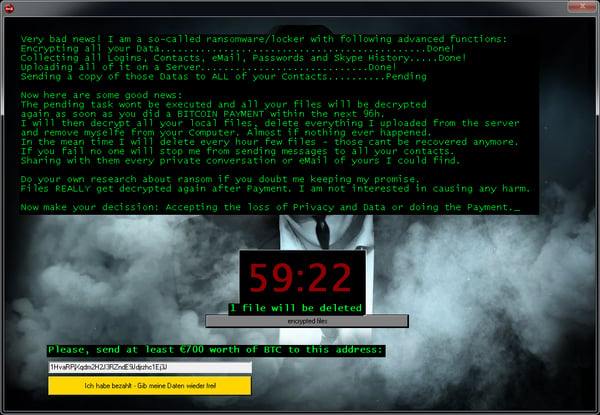
Jigsaw is a ransomware strain that has been around since March 2016. It’s named after the movie character “The Jigsaw Killer”. Several variants of this ransomware use the Jigsaw Killer’s picture in the ransom screen.
File name changes: Encrypted files will have one of the following extensions: .kkk, .btc, .gws, .J, .encrypted, .porno, .payransom, .pornoransom, .epic, .xyz, .versiegelt, .encrypted, .payb, .pays, .payms, .paymds, .paymts, .paymst, .payrms, .payrmts, .paymrts, .paybtcs, .fun, .hush.
Ransom Message: After encrypting your files, one of the screens below will appear:
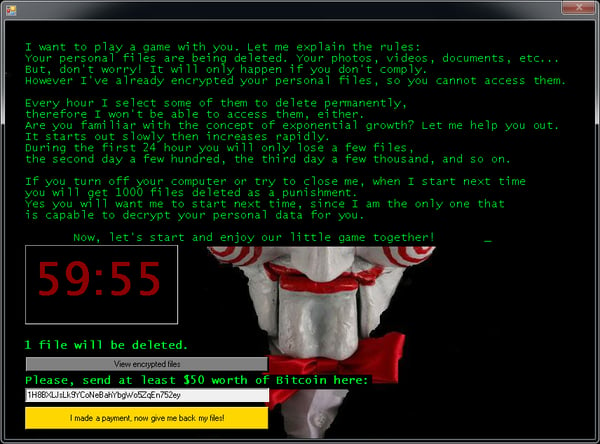
Stampado
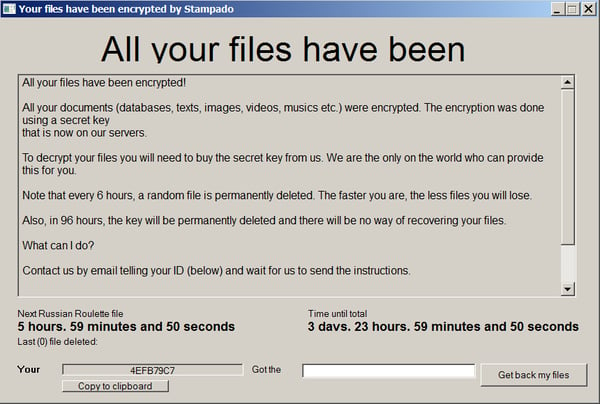
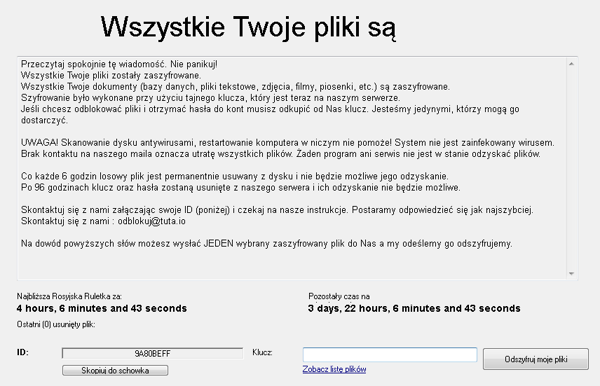
Stampado is a ransomware strain written using the AutoIt script tool. It has been around since August 2016. It is being sold on the dark web, and new variants keep appearing. One of its versions is also called Philadelphia.
File name changes: Stampado adds the “.locked” extension to the encrypted files. Some variants also encrypt the filename itself, so the encrypted file name may look like this “document.docx.locked” or 85451F3CCCE348256B549378804965CD8564065FC3F8.locked.
Ransom Message: After the encryption process is completed, the following screen will appear:
How to protect yourself from falling victim to ransomware
First and foremost, make sure you have antivirus, like Avast, installed on all of your devices (even smartphones can become infected with ransomware). Antivirus will act like a safety net and block ransomware before it can cause any damage, in case you accidentally try to download it.
The next thing you can do to protect yourself is to be smart and alert. Ransomware distributors often use social engineering tactics to trick people into downloading the ransomware. Be careful which links and attachments you open and what you download on the web. Make sure you verify the source of emails including links and attachments and only download software and visit trusted sites.
Backing up your data properly on a regular basis is also crucial. Be sure to not keep your backups connected to your devices all the time, otherwise, your backups could be held ransom as well.
If you are unlucky and do become infected with ransomware, make sure to check out our ransomware decryptor tools to see if we can help you get your files back!
Special thanks
I would like to once again thank my colleagues Ladislav Zezula and Piotr Szczepanski for preparing these decryptors.
IOCs
HiddenTear
009493fb23fe093b98d75aef62bb9301db13d9c1a8e63298f69b22719ac7bd92
08251816bab3878e2c38286e64d9b9e3e1337c97d392437dad2f9f1586e2075d
0f725b48b8645e64f8d8f80227aaf9549ac85b05b1402e0ff313044d18f8b353
1ad95b74b1e10f41b4ac7d2ee96c74e99f237e1e5717d9e59273a81477d8c9b6
3431689099074abd6b0ad5aee7aba0ef936a2d2007c1b5e7f6f3f4cb6d2a008e
355318e5fcc6f07bf41d27ef4832df2222919ad095f64b4080fd48e597b5ef44
38ea46b098257205aae48f1b9097df051c8f00688fa14016d062ba123d44a490
4219f9102b60530a6f99682e27aa047a6b1ecbf5461e325903fb0cce19d4c3b5
42b874dd426329d6c0616464f281439f3e122efa513127a69b349b79d583118c
57361eebd913854f4217a1c99397ddcd29c18d54a36421f42006b1a94a3bfef9
73a7ab4dd80364a090bc41971d6ebe95a4451f9bbd8340dc07af4dc86071999c
9bc81280113473de9ebfe54f689b4440287c37fff562e070d3a28f5269cadcf0
a1a1f810fa0860197cb5e4240f9a734ed1a066b6e5d7dd749eec101b73c72dfe
a34543a1a70531b406197e2c4cd5b96eaf4eff1527fb6378aa7ea32ccd1db1a5
abfcaab8e584bb18eea79083d0813e843b6107b60ca656f89c684fa26d1d3ae9
b32f1be576aed44a342cdb0c0ad56bf64527e0b40d558cdfb2e70a10a3d843fb
c4d97c6dd3ffbae1255bea202c73ba8b87cf7c681a2ec4aad8a079df14824bc8
cbea97aa1531aae2186bbdbc7caff7c6286f77504d78925736339bf6de669583
d5e5893687751c82ebd560828d89aff973cd319583e9d5e61778e18f3b2012c2
fd291b48c263a22e7af9cc44e311cb1b7b5a4bf8a109ccc06a7a9db6cc72b33f
Jigsaw
08c75d3d92d70a390543c600baadcbdcc6b43c92a9553751d4b9e32fad4e691f
0e125c4a6f127e6f1c7da07f820ea04daccb54c50cdb1583c6d177b2ec7e8a06
153b85a9f9f65f7e00d2bb4b812fbc1bc247f8d6ba6e14f971f71737b439b60c
1a9a9c198aaec440318eae2e1a34d418f89ff37dc8dd24380f2656b5e5cd17fa
61aa800584b170ffe9959acd057ccaf784bf3088e1d3aab39d07c0793f6c03df
6a60a514a5f279c529ae8be657ce501a64fc0c591bd2b47d1526f6fb347512fc
917809beb6566079dbb6b686107756d9eb3ff4543f6b41ef327cea7497118457
9580e6c4deba3bd46419a402b6309f77c2ed47ad62299c82ec8578400c2a3a64
bc83ef30422eb7b0c8903d3b4f1d4258e25cf78e9357a30dac773f8d2c17aa28
Stampado/Philadelphia
04a265124ae0e20b7cad58a19dad3d06f09118d6b05723f824d9ac9e20f6872f
09355d3237d203a9421f424df654444fdb7f5b9288bf57530980ac73545f1590
30b98ee321697be990136962e481d2cfeae295544550adbe887e88d5e01b7244
31d1f65dfca61b632d7decffa25d69c82c893bf6d5700347d7af46fa0779f284
4f6549c4bf5a644db47e1f38ab1facac7e48b604de571250523f3f7c9fd9ae25
655f577d28fe7eac077e728d3f081d2742aa5b476110133e9a0a1358bfe2f0d5
7d0ff206f60fe8144c28ed660be40d106b387896f652f3a0509db5fab1406b07
91cfffaee36715df953829dfd1b2353b274a374a9682c9b6d74cd5d915aec193
959d81795254f8462a56a40fc184f9ae327e360680a0c167d4e087cd52f6df4d
b2987914e8813e3fb4b71fa1e52b35e5581abe7107b765761569dda2949bea93
d369a5f0cfbc0b88d3a98e3ebe4fbe4f6e011cc2714fe79cb7d6a554c413dc95
daa4d154409a25b29b5cff5b7ff6ff218ded80ec3fc4694365b42bc216ef2f80
dd4aa2c3e398533759d44fe1e39fb1eba9151a780c2f76ad5ee32db79e5b36d0