Avast now offers ransomware victims 20 free decryption tools to help them get their files back.
A little less than a year ago, we started providing free decryption tools for victims of ransomware attacks. Today we're pleased to announce that we've just released our 20th free ransomware decryption tool: a free decryption tool for the EncrypTile ransomware. We've also updated a few of our older decryption tools, including AES_NI, BTCWare, CrySiS, Crypt888, and XData.
We first spotted a test version of EncrypTile in October 2016. Six months after its initial release, the ransomware now has a user interface and support for multiple languages (although the language translations are very poor). The ransom note is shown in the EncrypTile main window, as well as in the newly created desktop wallpaper.
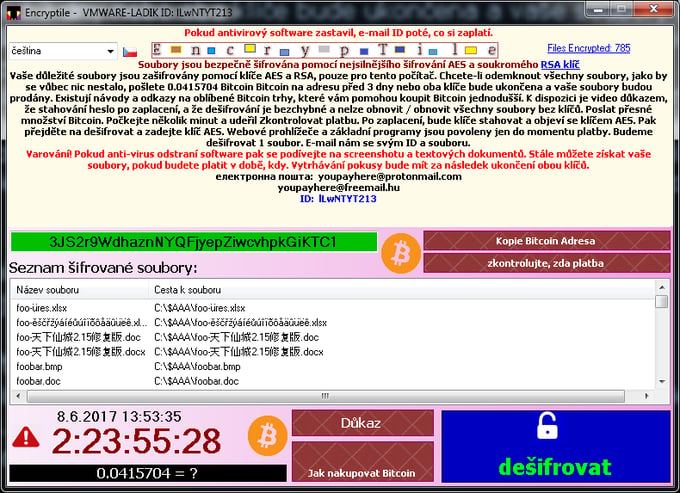
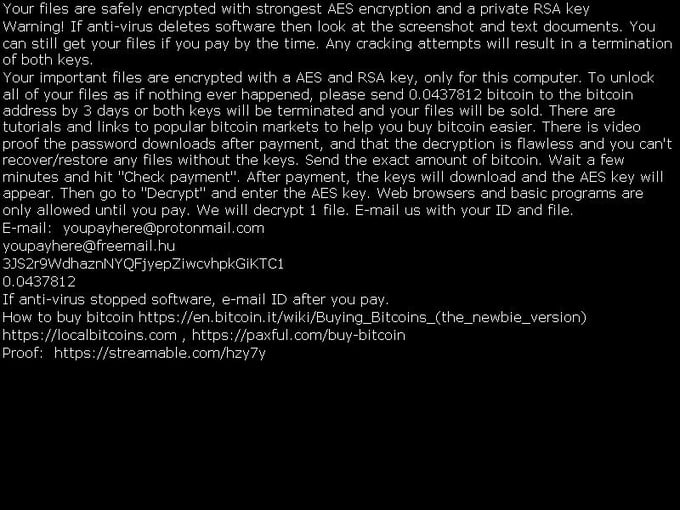
The ransomware also adds the word “EncrypTile” into the file name:
- invoice.pdf > invoice.pdfEncrypTile.pdf
- file > fileEncrypTile
After the files are encrypted, the ransomware creates 4 new files on the user’s desktop. The names of these files are localized. Below is an example of the English version.
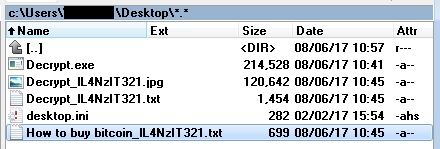
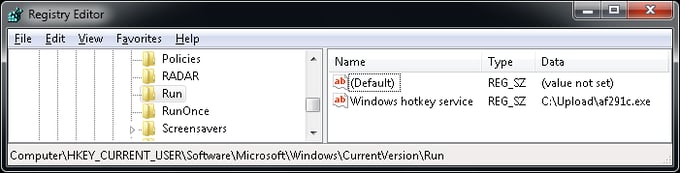
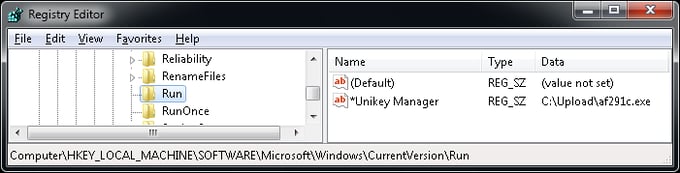
The ransomware also creates an auto-start entry, both for the current user and for all users of the computer:
EncrypTile has a list of whitelisted process names, and anything not on the list is auto-killed when detected. This prevents the user from running any security or diagnostic tools.
|
Equals to: csrss, dllhost, winlogon, explorer, conhost, vbc, dwm, lsm, svchost, services, smss,
spoolsv, system, wininit, wmpnetwk, lsass, sppsvc, chrome, firefox, iexplore, opera, idle, audiodg, encryptile, notepad, mspaint, printisolationhost, powerpnt, osk, acrord32, imagingdevices, mspscan, wmplayer, wscntfy, userinit, schtasks, magnify, browser, cmd, wuauclt
Contains: search, wallet, bitcoin, multibit, word, calc, microsoftedge
Has the name equal to the current (ransomware) process
|
An interesting effect of the above feature occurs with the Admin Approval mode. The ransomware kills the “consent.exe” process, the pop-up window that allows Windows users to approve or decline changes a program wants to make the computer. As a result, no administrator access can be granted and the user is stuck in the Admin Approval mode, unable to carry out any actions as the administrator.
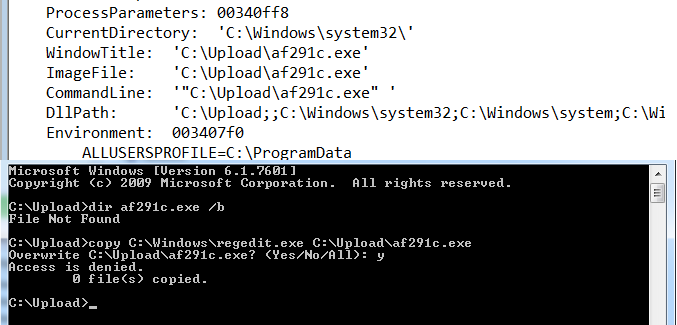
To prevent detection, the ransomware executable is invisible while it is running.
How to run the decryption tool
While running, the ransomware actively prevents the user from using any tools that may potentially remove it. Because of this, it is necessary to follow the steps below to successfully remove and decrypt the infected files:
- Download the decryptor tool and save it to your desktop. In case of an internet connection problem, you may need to download the file to another device and copy it to the infected PC manually.
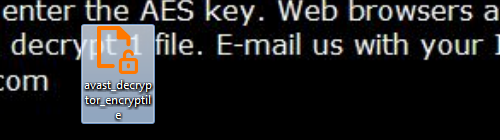
- Create a copy of the decryptor tool using the Ctrl+C and Ctrl+V keyboard shortcuts.
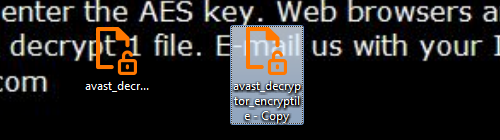
- Rename the newly copied file to one of the following names: notepad, lsass, mspaint, osk. Once you have renamed the copied file, you can run the decryptor.
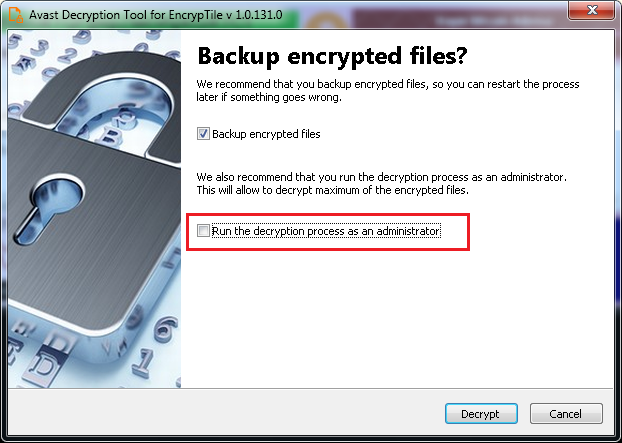
- Follow the steps in the on-screen wizard. On the final page, uncheck the “Run the decryption process as administrator” (if present) and click “Decrypt”.
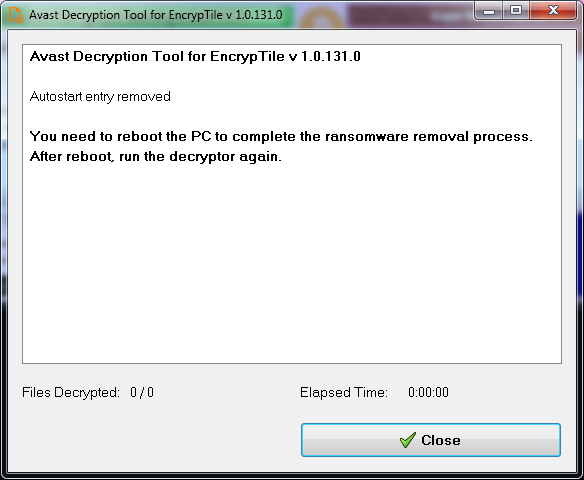
- If the ransomware is active, the decryptor will neutralize it and ask you to restart your PC.
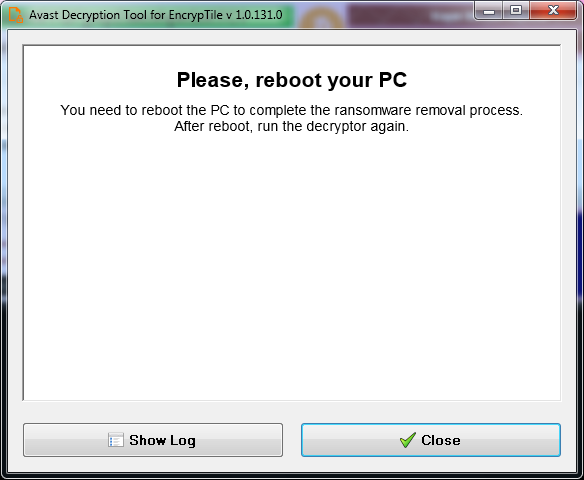
- Finally, restart your PC. After you log in, the ransomware screen should not appear anymore, but your desktop wallpaper will still contain the ransom note. Run the decryptor normally with the default options to decrypt your data. After this, you can change your wallpaper to something nicer than the ransomware wallpaper :)
Special thanks
I would like to thank my colleague Ladislav Zezula for preparing this decryption tool.
IOCs
20ed3d3637da4f753353faced8773d18ded4e032a536ef15364a0cf60dae5070
332084bd5cf73038fea4de37d25bb5bafe80416191db1f8505796b3a9ab95a13
af291c3025c55042669c326db303476b3d0eb183226e319c8c258a7b0be29a15