Don't pay, and don't despair. Instead, unlock your ransomed files using Avast’s ransomware decryptors.
*** UPDATE from May 18, 2017: Avast's free CrySiS ransomware decryption tool now also decrypts .WALLET file extensions***
*** UPDATE from March 2, 2017: Avast's free CrySiS ransomware decryption tool now also decrypts .DHARMA file extensions***
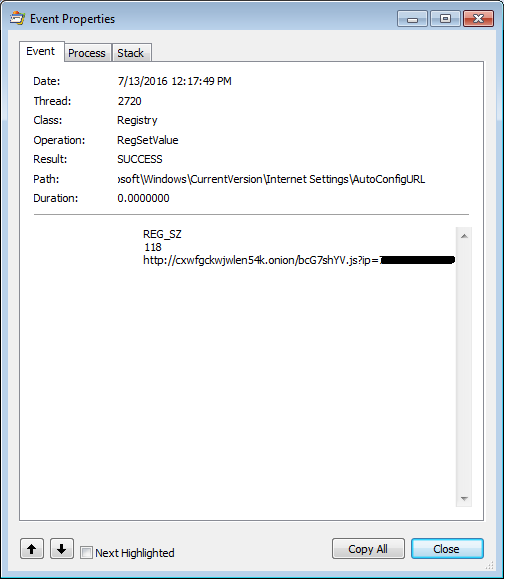
Files encrypted by CrySiS with the .DHARMA file extension name were previously impossible to decrypt prior to March 2, 2017, when Bleeping Computer shared the decryption key. Avast confirms that the key provided to Bleeping Computer decrypts .DHARMA files encrypted by CrySiS.
Original blog post:
Ransomware has become the new 'It Malware,' with a 105 percent year-over-year increase in attacks. Therefore we're happy to announce that we've released four more ransomware decryption tools for the latest ransomware threats: Alcatraz Locker, CrySiS, Globe, and NoobCrypt. All the decryption tools are available, together with a detailed description of each ransomware strain. We now have tools to help you recover encrypted files if your computer has been infected with one of these ransomware strains:
- Alcatraz Locker
- Apocalypse
- BadBlock
- Bart
- Crypt888
- CrySiS
- Globe
- Legion
- NoobCrypt
- SZFLocker
- TeslaCrypt
All these tools are free and, when possible, updated as these strains evolve.
Since we’ve released the first batch of seven decryption tools, we’ve received many messages from ransomware victims thanking us and telling us that these tools saved their digital lives and/or businesses. We hope the four new decryption tools will help more innocent people affected by these ransomware strains, and brief descriptions of each follow.
Alcatraz Locker
Alcatraz Locker is a ransomware strain that was first seen in the middle of November 2016. Files encrypted by Alcatraz Locker have the extension name ".Alcatraz." After encrypting files, a message appears (the message is located in a file called "ransomed.html" on the infected computer’s desktop):
Unlike most other ransomware strains, Alcatraz does not have a list of file extensions that it is interested in. Simply said, the ransomware encrypts whatever it can find and is open for write access. To prevent damage to the operating system (and possibly rendering it unbootable), Alcatraz Locker only encrypts files in the %PROFILES% directory (usually C:\Users).
Alcatraz Locker encrypts files using Windows’ built-in cryptographic functions (Crypto-API):
 The ransom message states that it uses AES-256 encryption with a 128-bit password. Malware analysis showed this to be false (the password is actually 128 bytes, not 128 bits). However, the malware uses 160-bit hash (SHA1) as an initial key for 256-bit AES encryption. In Crypto-API (used by the ransomware), this is implemented with an interesting twist:
The ransom message states that it uses AES-256 encryption with a 128-bit password. Malware analysis showed this to be false (the password is actually 128 bytes, not 128 bits). However, the malware uses 160-bit hash (SHA1) as an initial key for 256-bit AES encryption. In Crypto-API (used by the ransomware), this is implemented with an interesting twist:
- Create 256-bit array, filled by the hexadecimal value 0x36
- XOR the first 160 bits of that array with the initial 160-bit SHA1 hash
- Calculate SHA1 of the XOR-ed array (call it Hash1)
- Create 256-bit array, filled by the hexadecimal value 0x5C
- XOR the first 160 bits of that array with the initial 160-bit SHA1 hash
- Calculate SHA1 of the XOR-ed array (call it Hash2)
- Combine (concatenate) 160 bits from the Hash1 and 96 bits from Hash2
The resulting, concatenated hash is used as the initial key for AES256.
After performing the AES-256 encryption, the ransomware also encodes the already-encrypted file with BASE64, which causes the encrypted file to have a typical pattern:
The ransomware states that the only way to get your data back is to pay 0.3283 Bitcoin (about $240 at the time of writing this article). However, if you use the Avast Decryption Tool for Alcatraz, you can get your files back for free :). The 30 day time limit, which is mentioned in the ransom message, is also a lie; you can decrypt your documents at any time, even after 30 days.
CrySiS
CrySiS (also known as JohnyCryptor or Virus-Encode) is a ransomware strain that has been around since September 2015. Its severity is based on the strong encryption (AES and RSA algorithms) it uses and the fact that rather than encrypting selected files, it contains a list of extensions that will not be encrypted.
Encrypted files follow a pattern of: <original-file-name>.id-<NUMBER>.<email@domain.com>.<extension>
While the ID-number and email change often, there are only three different extension names that we have seen being used so far:
.xtbl, .lock, and .CrySiS
As a result, encrypted file names can, for example, be:
- .johnycryptor@hackermail.com.xtbl
- .systemdown@india.com.xtbl,
- .Vegclass@aol.com.xtbl,
- .{funa@india.com}.lock
- {milarepa.lotos@aol.com}.CrySiS
Each encrypted file contains all the data required to decrypt itself. Files smaller than 262,144 bytes are encrypted fully and at the end there’s a structure containing an encrypted AES key along with other data, such as the original file name, which will allow for full decryption. It’s worth noting that files larger than 262,144 bytes are only partially encrypted, which still renders them unusable. This functionality also causes larger files to grow in size post encryption.
After encrypting the files, the ransomware displays a message as an image (see below) describing how the encrypted data can be retrieved. The message is also located in "Decryption instructions.txt", "Decryptions instructions.txt", or "README.txt" on the infected computer’s desktop.
Several examples of CrySiS ransom messages:
Globe
Globe is a ransomware strain that has been been around since August 2016. It is written in Delphi and usually packed with UPX. Some of the variants are also packed with Nullsoft Installer:
- bc4c0b2f6118d36f4d476db16dbd6bcc0e393f2ad08429d16efe51f3d2870d58
- fdc8de22653ebcf4cb8f5495b103e04079b0270efa86f713715f0a81f1b2e9b0
In the unpacked binaries, there is a global “configuration” structure, where the ransomware author can modify some of the features:
- Target name of the executable in %APPDATA% folder
- The extension of the encrypted files
- List of file types (extensions) to encrypt
- The ransom message in HTML format
- Whether the ransomware should encrypt file names or not
- Whether the ransomware should check for sandboxes (VirtualBox, VirtualPC, Vmware, Anubis)
- Whether the malware should auto-start or not
- Whether the malware should delete restore points
- ... and more
Because distributors can modify the ransom, we have seen many different variants creating encrypted files with various extensions.
Interestingly enough, the ransomware has a built-in debug mode, which can be enabled by the following registry setting:
When enabled, the ransomware will ask about each particular step:

Based on sample, the ransomware encrypts files either with RC4 or BlowFish encryption. When the ransomware is configured to encrypt file names, it does so with the same encryption like the file data, and the encrypted name is then encoded with an own implementation of Base64 encoding.
A few examples of created extensions that can be decrypted using Avast Decryption Tool:
- .globe
- .GSupport3
- .siri-down@india.com
- .zendrz
- .decryptallfiles@india.com
- .MK
Typically, the ransomware creates a file named “Read Me Please.hta” or “How to restore files.hta”, which is displayed after the user logs in:

Do not pay! Use our Globe Decryption Tool instead.
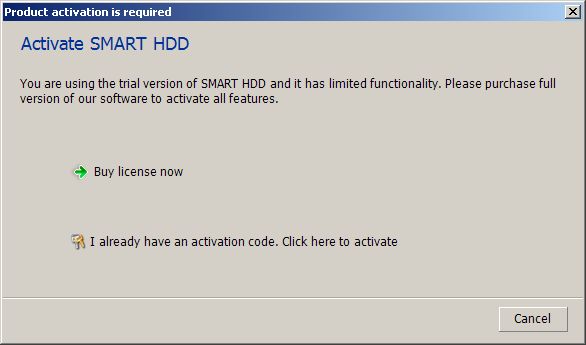
NoobCrypt
I discovered this strain back in July 2016. It is a project created in C# and utilizing the AES256 encryption algorithm. It also has an expressive graphical interface, which appears once the victim files are encrypted.
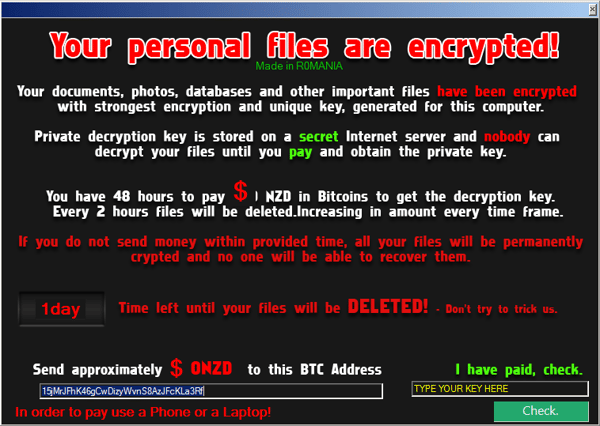
This screen with the extortion information is an odd mixture of messages. For example, it requests payments to be made in a certain amount of New Zealand Dollars (NZD), but requests the payment be made to a Bitcoin address, while at the same time it proudly claims to be “Made in Romania”. An odd combination, if you ask me.
The name NoobCrypt has been chosen based on messages found it its code:
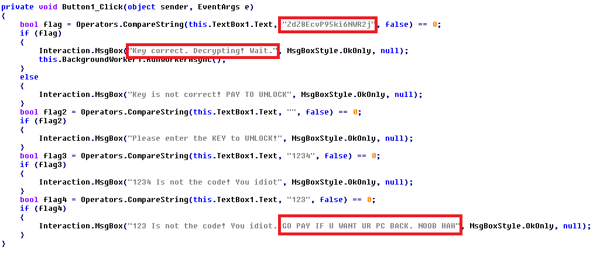
The code quality is quite poor, but its author compensates for this lack of quality by using strong words, such as calling victims Noobs (i.e. newbies).
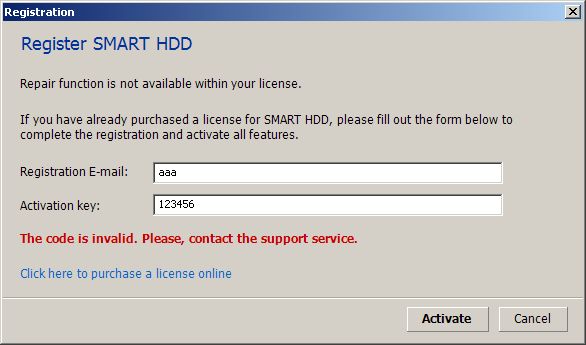
NoobCrypt provides an “unlock code” to decrypt the files, which has to be purchased. I already posted free unlock codes for all known NoobCrypt versions on Twitter (e.g. 1, 2, 3), but it was up to the affected person to distinguish, which of them had to be used. However, with our decryption tool you no longer need to figure out which code needs to be used.
Shortly after this defeat, a malware researcher called xXToffeeXx notified us about the discovery of a new NoobCrypt version advertised on multiple darknet markets. This version is on a sale for $300.
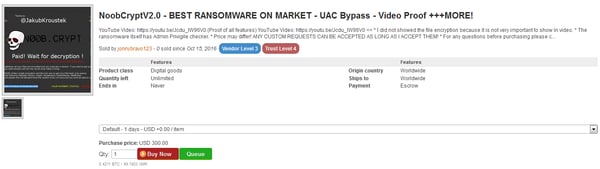
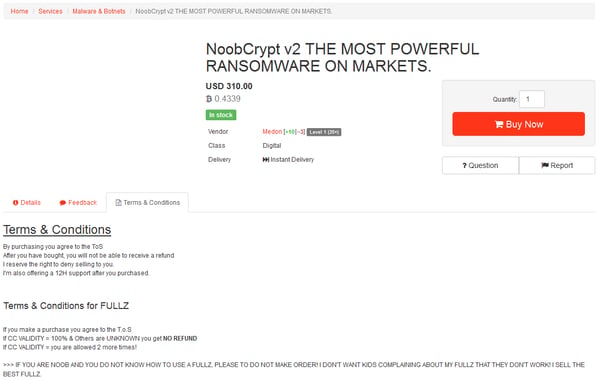
The author even prepared a demonstration video with features he or she claims are new, such as the usage of “Military Grade Encryption” or being “undetectable by any AV (except of AVG)” (which is not true… many AVs detect this).
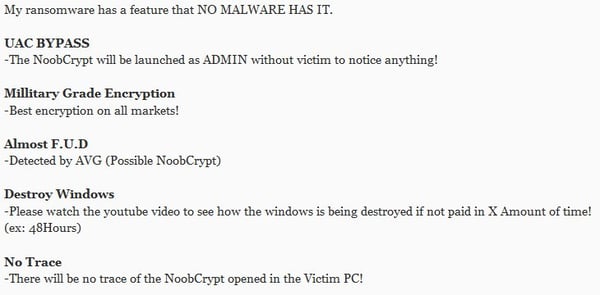
(Source: xXToffeeXx)
As you can see from the following screenshot, the author even used my name on a screen with ransom instructions and thanked me for something. Probably for giving a proper name for this piece of low quality code (this name is now being officially used).
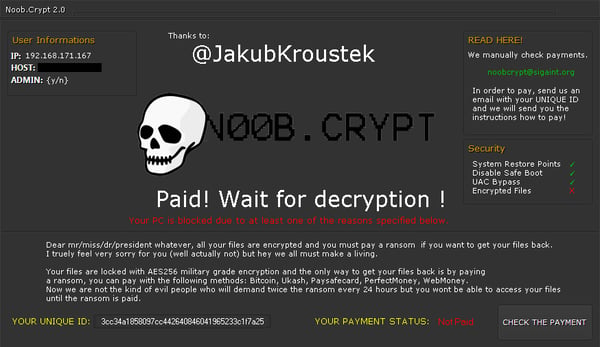
Today, we present a NoobCrypt decryption tool for all known NoobCrypt versions. The decryption process is now much easier than finding a proper unlock code and you no longer need to depend on the decryption code from NoobCrypt (you shouldn’t trust ransomware to decrypt your files, right?). Read more about NoobCrypt and our decryption tool.
How to protect yourself from falling victim to ransomware
First and foremost, make sure you have antivirus, like Avast, installed on all of your devices (even smartphones can become infected with ransomware). Antivirus will act like a safety and block ransomware before it can cause any damage, in case you accidentally try to download malware.
The next thing you can do to protect yourself is to be smart and alert. Ransomware distributors often use social engineering tactics to trick people into downloading the ransomware. Be careful which links and attachments you open and what you download on the web. Make sure you verify the source of emails including links and attachments and only download software and visit trusted sites.
Backing up your data properly on a regular basis is also crucial. Be sure to not keep your backups connected to your devices all the time, otherwise, your backups could be held ransom as well.
If you are unlucky and do become infected with ransomware, make sure to check out our decryptor tools to see if we can help you get your files back!
Special thanks
I would like to thank my colleagues Ladislav Zezula and Piotr Szczepanski for preparing the decryptors and to Jaromír Hořejší for his analysis of the Alcatraz Locker.
IOCs
Alcatraz Locker
918504ede26bb9a3aa315319da4d3549d64531afba593bfad71a653292899fec
b01cfc16f9465fd67a6da91d5f346ed3f07eb76b86967758ab1089d4e6399971
b8949ae0d1a481af1cae9df5e01d508d1319b6d47fb329e9b42627e4e2a72a3d
be3afa19c76c2270ccac7eacf68f89603032c0588f721215e15a9d1421567969
CrySiS
04c2ca82353deeb7e007fbba40de82cd4fac516bfe760cfb8dae1e78d568ff4f
0629ea3504e6cb577c961c6f0d37392b70b15d84b4df51a05a16d69304d8aa4d
2437e179229b7240ca2db1a7a520bc194c1ce0992c015e79cc8af611e97667f7
44c8ebd4d36950d836449df3408f6511b7256dc63c379b9835517d80a33eb8f5
47035f9e75be0a29c07c05fe54e6cacf05e18bdc5ab770efabd7f594a6b05a22
4c3f02aec4e1797f2853bb2255766cddc4edc716e8f7310909ba68676d651637
bdadaec64745f609aed3eac457046849aa6d96c1c6a2863f3c8007da6b56d1f2
e9744e8eb6c7108c74918d02810a5608082663cccd8f2708c59399089693b31e
Globe
5e714797afc35196be1f7d0bb536c2dcd4f5a18df15975ab283e353ef1f37176
6a7d674f5a587655ee22093d17a958e01131675dda73502efc0a082be6970fc5
82cdae2b1866f2c536a21ee60e1c74a6b94c12bc3b13c38be2d0c3689ce5f0c8
9727aca489a72eecacbfd00b451aaf91a56e061856a7f1989792cf9557156749
eda8b8af7b8d7d00da49f5f0a2dfa21b35ab510e4d9a625985eaef0e1d5ecbbf
f365425e42fc2fa4c0eac4a484ca9f8ef15d810de6a097ac8b071a13e803e117
NoobCrypt
571434bcc4cf4fadba142967a5ee967d907bd86adf1a380fccbb8c4c9995dd0f
8c341a114a229e75d4b4342c4288f18dc059bfb0c7740fc59789414c811c3a9e
974d2a36971b0f05c8a2d5b0daaee93732b78f0edeb4555aadbc1b7736ce995f
b34aac65a853b975810ef026d7ce8ed953d6b5d4c6279bda38f58eaff2fa461c
bb00898bc70469b39dfd511163b2b8a75e36d7ec4a455f0db6c6cfb9a26600ed
d2d2b0a4e51c185ac032cd32576ae580d885f89a23e3886a04f38fb424e6a17a
f5329b87967aa978cd47ec7c6332fd013062593d05d65f28a46f3106a9ad894a