Avast releases new ransomware decryption tool for the AES_NI ransomware.
Special thanks to Ladislav Zezula for working on this blog post and the decryptor tool!
If your files have been encrypted by the AES_NI ransomware, you can now recover them without paying the ransom. To decrypt your files, download Avast’s free decryptor tool.
The AES_NI ransomware was first spotted in December 2016. We have seen multiple variants since then, that can be distinguished by the file extension of encrypted files:
- example.docx.aes_ni
- example.docx.aes256
- example.docx.aes_ni_0day
When encrypting files, the ransomware generates an RSA session key (one per machine). This session key is then encrypted and saved to a file to the %ProgramData% folder (e.g. “C:\ProgramData”). The name of the file looks like this:
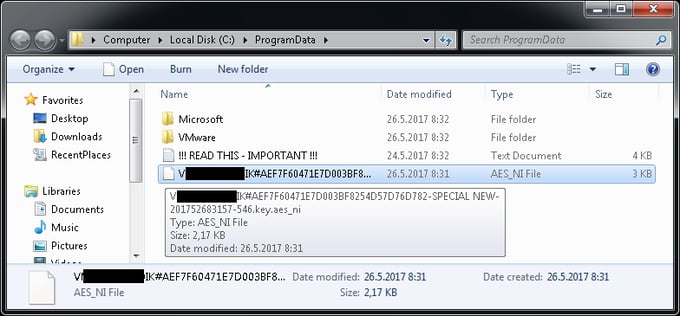
Unlike rest of the encrypted files, this file’s AES key needs to be decrypted using a master private key, which was published on May 25 2017 by the Twitter user @AES___NI. With this, security researchers can now create a universal decryptor.
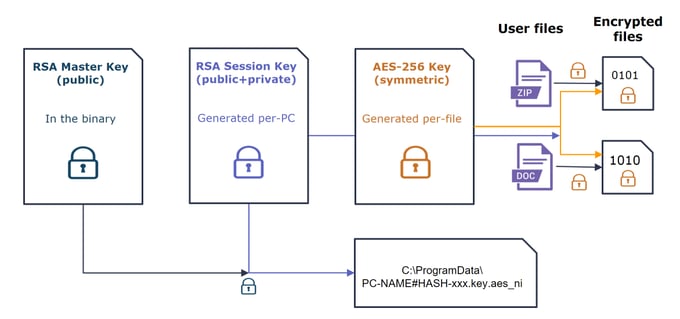
When encrypting a file, the ransomware generates a per-file random 128-byte number (using the CryptGenRandom API). This number is then cut down to a 256-bit AES key, and used for encrypting file data. The ransomware encrypts the file data in-place (using memory mapping), encrypting up to 15,728,640 bytes. The AES encryption key is then stored at the end of the file, together with user ID and original file name.
The encryption scheme can be summarized by the following picture:
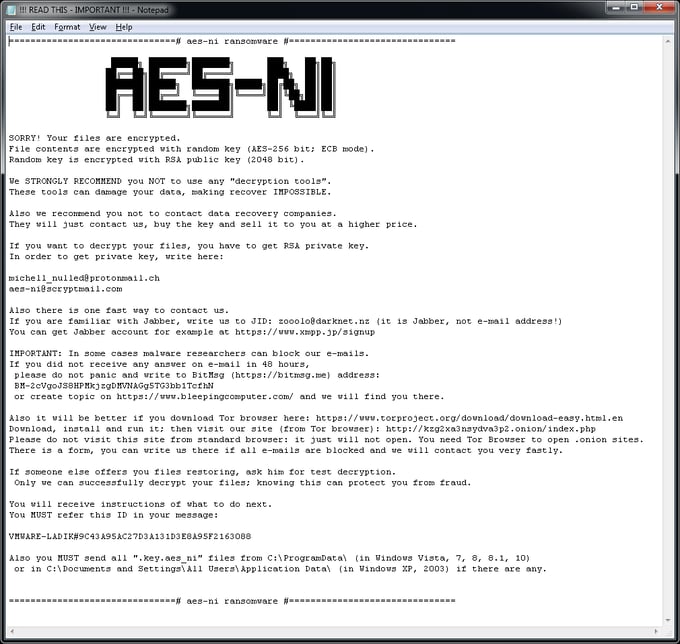
The ransomware creates a file “!!! READ THIS - IMPORTANT !!!.txt” within each folder that has at least one encrypted file in it. The content of the file looks like this:
Tips on how to avoid ransomware
- Install antivirus on all devices possible, including on your smartphone. Antivirus will block ransomware, should you encounter it.
- Updating all of your software whenever a new version becomes available can help prevent ransomware from exploiting a software vulnerability to infect your device.
- Being cautious can also greatly help avoid ransomware. You should stay away from shady websites, be careful what you download, and not open any links or attachments sent to you from a suspicious or unknown sender. Many people don’t think an ordinary Word or Excel document can lead to something malicious downloaded, which is why cybercriminals like using them for their attacks. Malicious attachments, sent in the form of a Word or Excel document, often request macros to be enabled, which allows the document to download malware, including ransomware, from the internet.
- While it cannot help you avoid ransomware, backing up your data on a regular basis will help avoid data loss, in case you fall victim to ransomware. If you regularly backup your data, while offline, to an external hard drive that is not connected to the internet, you greatly lower the risk of anyone touching your data through the internet.
IOCs:
.aes-ni
157D7AD2664AA2B7F534A628D56026B0DF9F5FFCCE7CC1F1943A9F939B3F4CF0
A9E2D14DC0F3CF022D52C671675961489592D5F90F97791FBD99007A4F494BD3
.aes_ni_0day
4142ff4667f5b9986888bdcb2a727db6a767f78fe1d5d4ae3346365a1d70eb76