Malicious Chrome extension attempted to infect tens of millions of users to mine the Monero cryptocurrency.
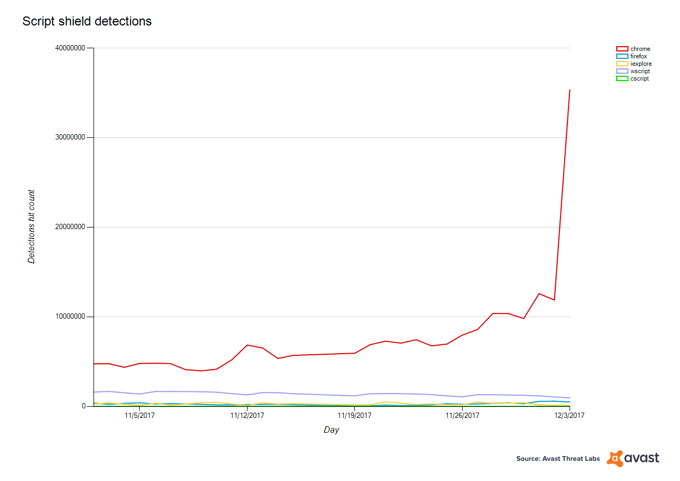
On Sunday, December 3rd, we saw a peak in one of our detections, JS:Miner-I, which blocks a cryptocurrency miner that uses the cryptonight algorithm to mine Monero, a popular cryptocurrency. The algorithm is suitable for using PC CPU for mining, and the miner is run using JavaScript. We blocked JS:Miner-I from launching on our users’ PCs, preventing 34.7 million attacks in just one day. The extreme peak wasn’t the only thing that caught our attention; all the detections were launched within Google’s Chrome browser.
Cryptocurrencies are trending and with the rise in popularity has come a rise in its mining. Cryptomining partly determines currency value, however, mining can be expensive, as it requires high amounts of processing power, which can be achieved through huge server farms. Constructing and maintaining the infrastructure, and accessing the electricity necessary to run these farms requires enormous financial investment. To save on costs, cybercriminals instead resort to using the power of your PC or smartphone to mine, and in many cases, they aren’t asking your permission.
In terms of the cryptomining attack on Sunday, we suspect the Javascript code was injected into a Google Chrome extension, as the files blocked as JS:Miner-I were in Chrome’s blob_storage, which is a folder used by extensions and add-ons to store data. While we cannot say for sure, we believe two things could have happened here: either this is a malicious campaign that was effectively spread, or a popular extension was modified to include the miner.
Nearly 35 million was a huge spike, compared to the number of times we blocked this miner from mining on our users PCs in the days prior, as can be seen in the chart below.
Why Monero?
We have seen several types of cryptomining malware this year, including Adylkuzz which peaked in May, and cryptomining malware that targeted mobile users last month. These examples and the miner that peaked on Sunday have one thing in common: They mine the Monero cryptocurrency. So the question is, why do they all mine Monero and not Bitcoin or any other cryptocurrency?
One reason might be that Monero keeps transactions private, which also comes in handy for the cybercriminals if they want to obscure their activities. Monero uses three different privacy technologies to hide the sender, amount being sent and the recipient, obscuring transaction details. Therefore, Monero has become very popular in general, and its value has grown from under $2 to over $200, which is probably another reason why Monero is the cybercriminals’ currency of choice. While Bitcoin is widely used, it doesn’t keep transactions private and is more difficult to mine compared to Monero, which can be reasonably mined using a browsers’ CPU power.
How to find out if your browser is secretly mining, and what you can do about it
Avast antivirus products detect these embedded miners. In addition, there are a few other strategies you can employ to see if your browser is mining:
- Check to see what scripts your browser has loaded. If you are registering significant CPU load yet there is only one tab in your browser and you are not running anything that should put significant load on your CPU, then odds are you’re being used to mine cryptocurrency.
- If you discover that a site you visit is mining, and you use an ad blocker that lets you add additional URLs to their “block” list, add this website to your list.
- Search the Chrome Web Store—or something similar—for “miner blockers” and see what comes up. Developers have already created ways to automatically detect mining and stop it from occurring.