Avast and ESET worked together to analyze an APT group’s series of cyberattacks on Central Asian companies and government institutions.
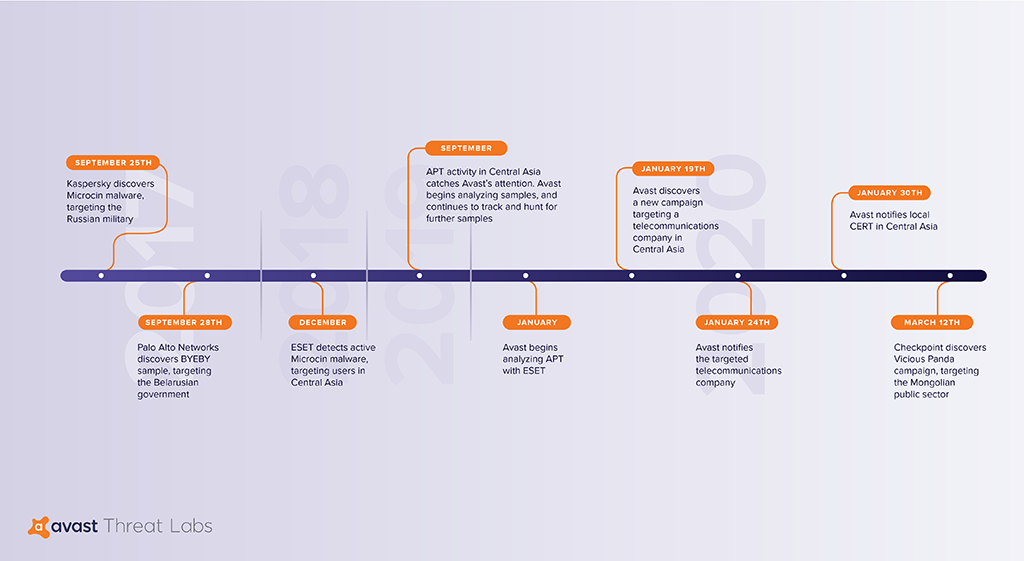
Working together with Slovakia-based security company ESET, Avast researchers analyzed samples used by an APT group to target Central Asian entities including a telecommunications company, a gas company, and a governmental institution. The attackers infiltrated the networks of these organizations and planted backdoors, which they proceeded to use quietly over a period of time, monitoring their victims’ operations and gathering information.
APT groups are typically state-sponsored and motivated by politics and ideals rather than money. The average consumer does not need to worry about being targeted. Espionage, information, trade secrets – these are what fuel an APT group’s actions. “APT” stands for “advanced persistent threat,” which refers to the long-term presence the attackers establish on their victims’ servers.
In September 2019, Avast noticed this particular APT group attacking Central Asian targets. Our researchers began monitoring the group’s action, and in January 2020 we teamed up with malware researchers at ESET to analyze the attack tools that the APT group was using.
We found the campaign relies heavily on Gh0st RAT, the remote access Trojan used most commonly by Chinese APT groups. Further analysis leads us to believe this same group attacked the Belarusian government and Russian military in late 2017. Gh0st RAT gives attackers the ability to install secret backdoors, which can be used to manipulate and delete files, take screenshots, alter processes, and more.
Evidence suggests that these APT attacks are part of a larger campaign. Avast researcher Luigino Camastra predicts we’ll be seeing more from this group. “Based on what we have discovered,” he commented, “and the fact that we were able to tie elements of these attacks back to attacks carried out in other countries, we assume this group is also targeting further countries.”
Avast alerted the affected telecommunications company that it was under attack and reported all these findings to the Central Asian local CERT team. We are continuing to monitor the situation.