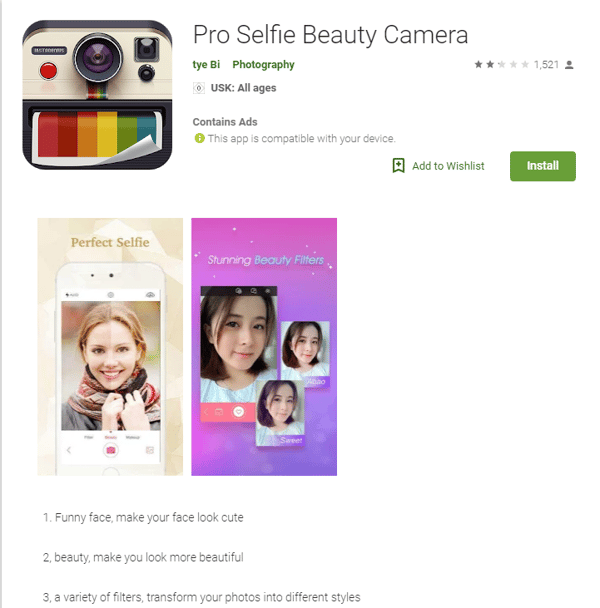
Our mobile threat intelligence platform flagged three beauty apps that have ugly consequences. Over 2 million devices have downloaded these apps.
In February 2019, Avast’s mobile threat intelligence platform (MTIP), apklab.io, discovered a number of “selfie beauty apps” on the Google Play Store posing as legitimate apps, but in reality were filled with adware and spyware. The three apps we found are Pro Selfie Beauty Camera, Selfie Beauty Camera Pro, and Pretty Beauty Camera - 2019. The apps claim to add filters to selfie photos and modify the appearance of the people in the selfies. However, the apps primarily include adware that aggressively displays ads and spyware capable of making calls, listening to calls, retrieving the device’s location, and changing a device’s network state. The apps all have at least 500,000 installs, with Pretty Beauty Camera - 2019 having over one million installs. According to our data, the apps are mostly installed by Android users in India.
The apps have thousands of reviews, most of which rate the apps poorly, commenting that the apps don’t really work but instead display ads. There are, however, some positive reviews of the apps which are most likely fake.
Hidden beauty
Once the apps are installed and launched, they aggressively show ads within the app and even display full-screen ads outside of the apps when the phone is rebooted. The frequency of the ads is determined by a file downloaded from a remote command and control server.
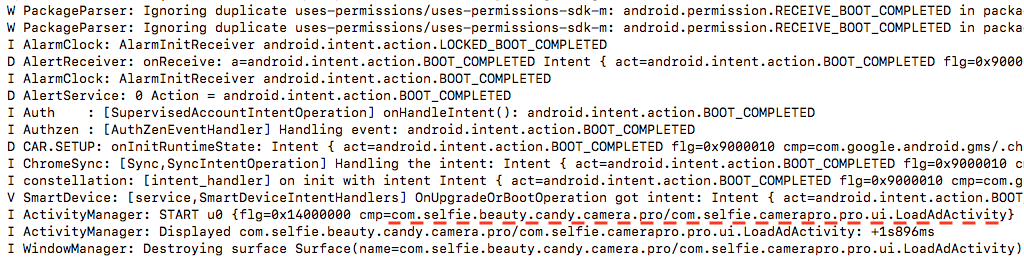
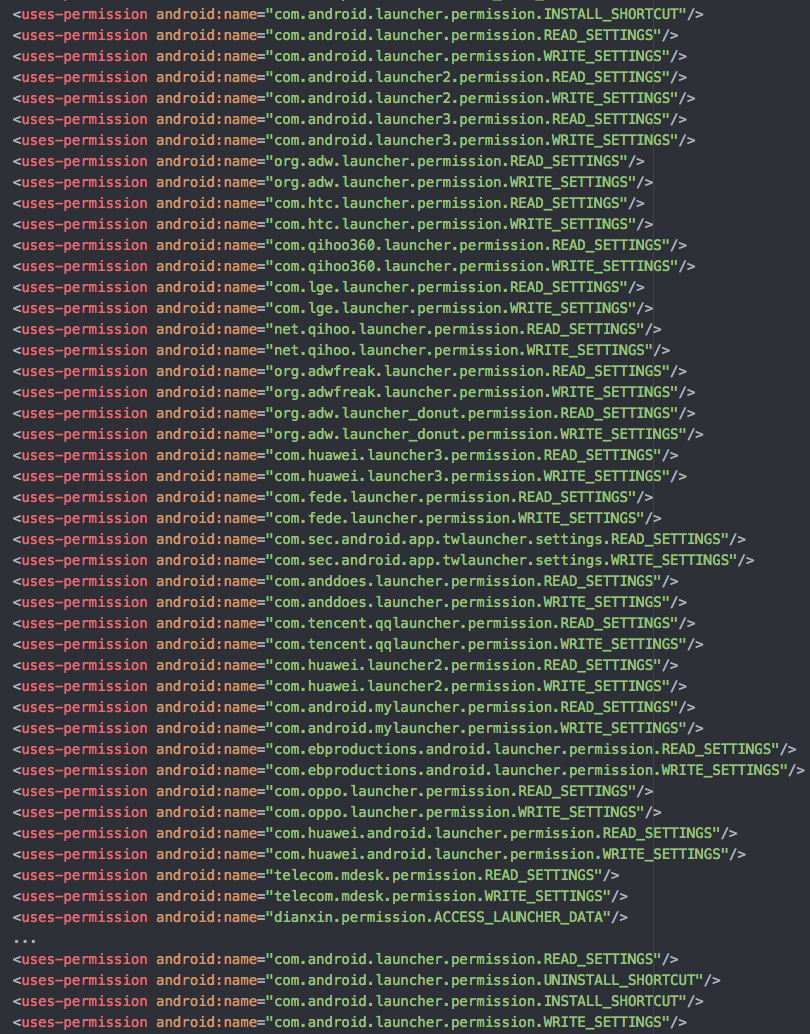
The apps are also difficult to remove as their icons are often hidden from the Android Launcher screen, making it impossible for users of Android with the “drag and drop” function to delete the app by dragging it into the trash bin. This is likely done so that the people behind the app profit from the ads shown to users. For each ad displayed, the bad actors make money from advertisers. So, they make it hard for users to delete the app so that they can show more ads and make more money. The apps check for the following launchers: Apex, HTC Sense, 360 Launcher, QQ Launcher, Huawei, OPPO, LG, Samsung and more. If one of the launchers listed in the screenshot below is found on the device, the app automatically uninstalls the app icon.
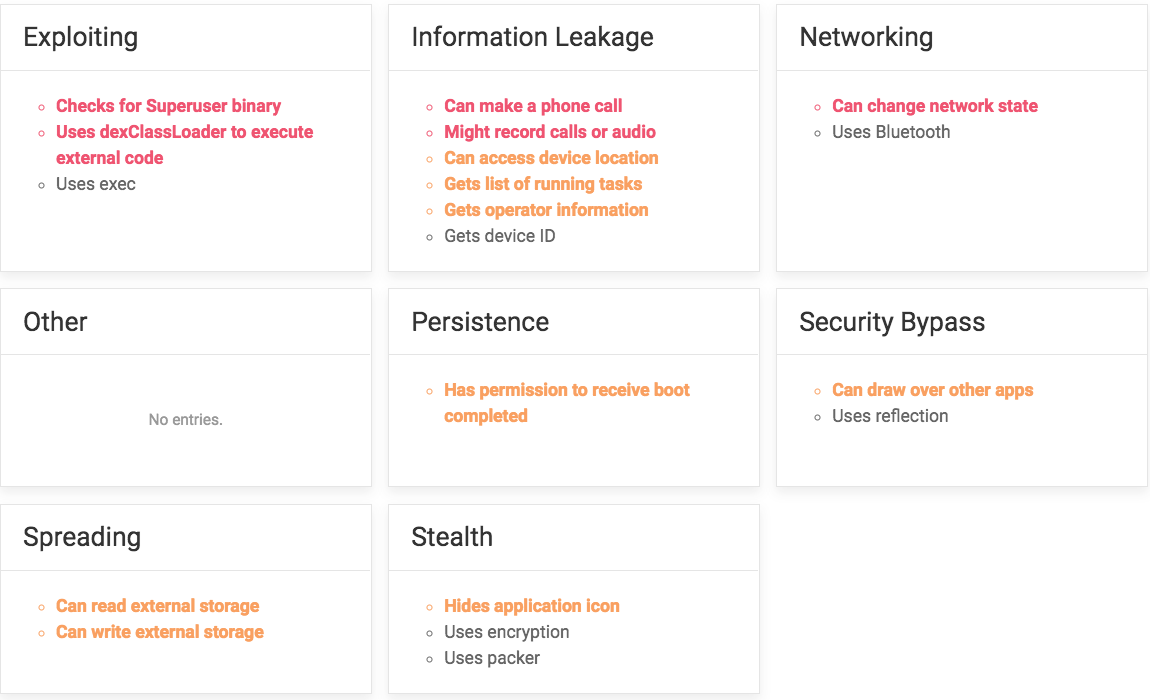
In addition to displaying ads, the apps are also capable of making phone calls, recording phone conversations, changing the network state, drawing over other apps, and reading the device’s external storage and more.
Below is a summary from Avast’s apklab.io, showing a full list of the apps’ capabilities.
A Chinese Author
We noticed a few things that make us believe the app’s author(s) might be Chinese. For example, one of the developers’ email address is songshijie19711110@gmail.com, which is the Romanisation of a Chinese name and there are also some simplified Chinese words in the code, more specifically in the params.txt file under assets.
The apps also use the Tencent Bugly tool, which is a tool that provides developers with crash reports and allows them to push update notifications to their apps. Finally, the launchers that the apps check for in order to hide their app icon include launchers available in China.
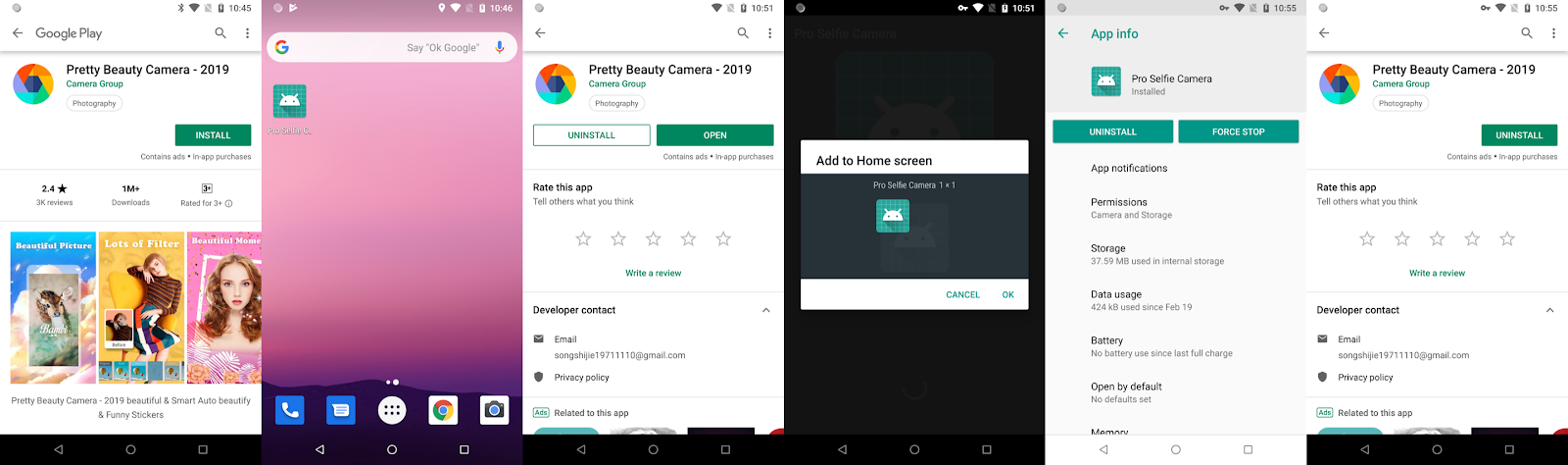
Screenshots of Google Play Store on Launcher
According to our internal telemetry of apklab.io and to the reviews on Google Play Store, it appears that most victims are from India, with other victims being located in Myanmar and Indonesia, among other locations.
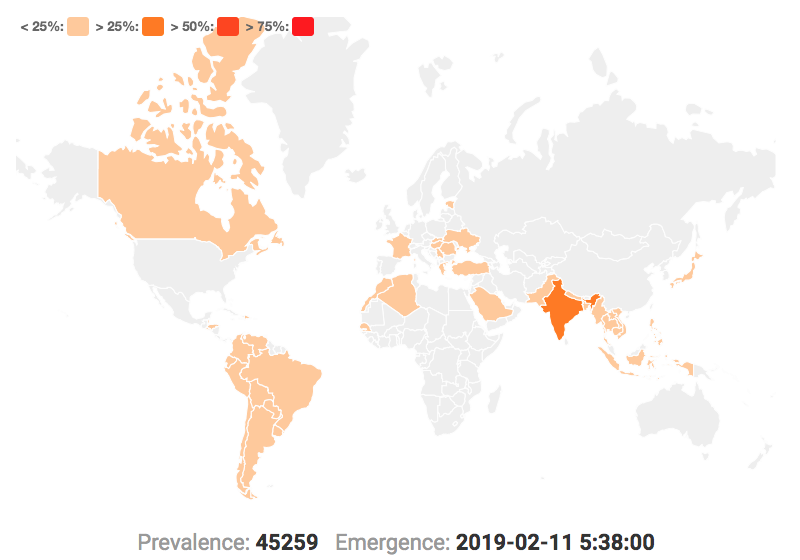
Internal telemetry results of latest version of “com.selfie.beauty.candy.camera.pro” app showing where the app is downloaded the most.
Some of the apps still use HTTP to update the advertising configuration from the remote server and it's easily recognized.
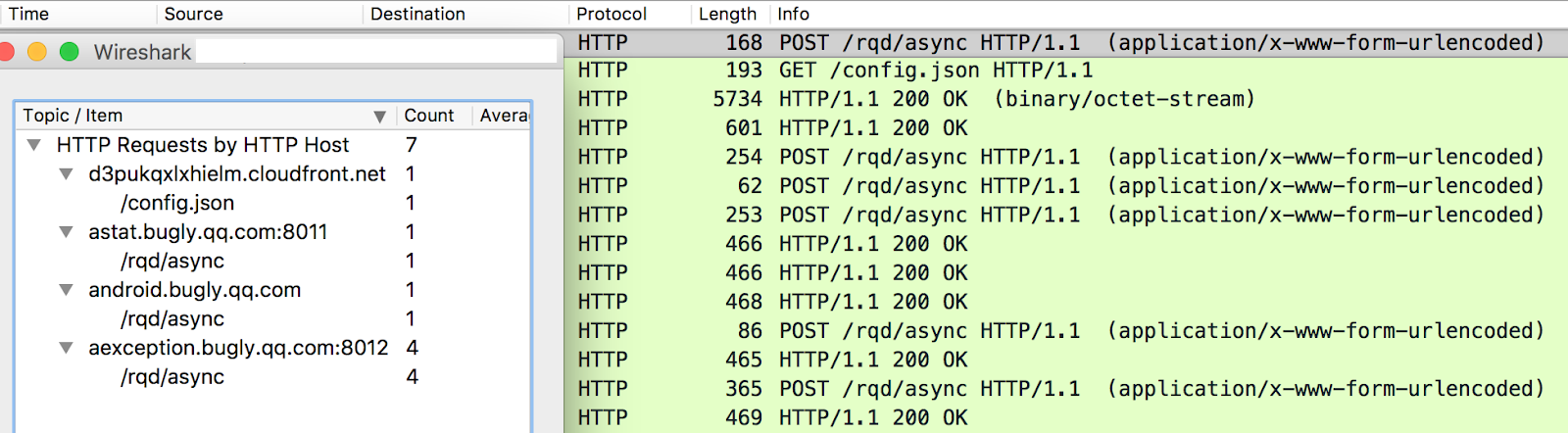 Screenshot of network trace mixing with the advertising and Bugly analytics
Screenshot of network trace mixing with the advertising and Bugly analytics
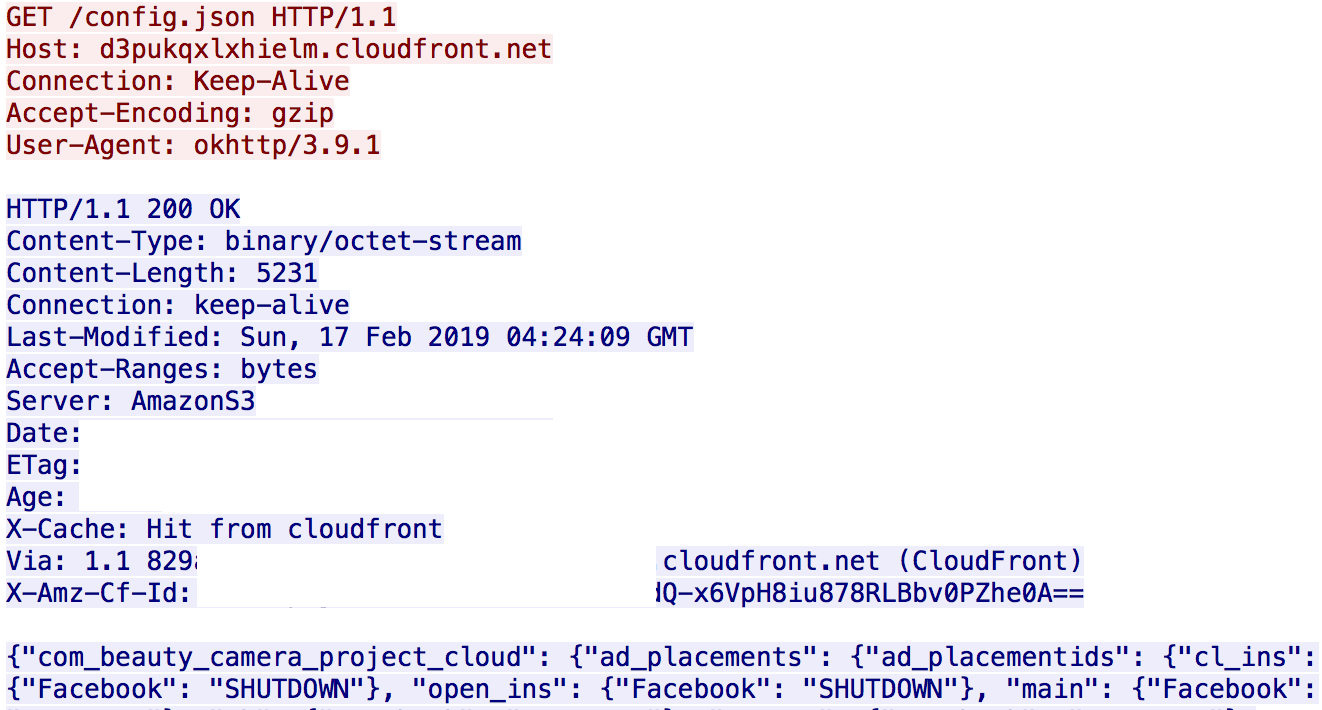 Screenshot of configuration update from remote server d3pukqxlxhielm.cloudfront.net
Screenshot of configuration update from remote server d3pukqxlxhielm.cloudfront.net
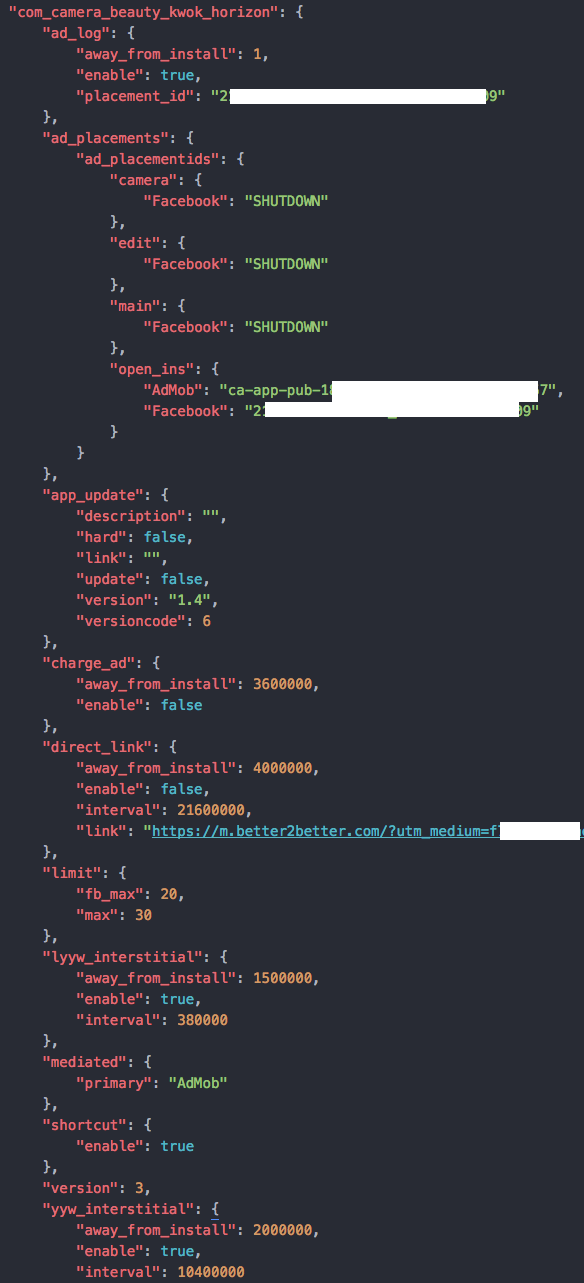 Screenshot of config.json from d3pukqxlxhielm.cloudfront.net
Screenshot of config.json from d3pukqxlxhielm.cloudfront.net
Google Play Store links for the adware and malware apps discussed in this blog
https://play.google.com/store/apps/details?id=com.selfie.beauty.candy.camera.pro
https://play.google.com/store/apps/details?id=org.selfie.beauty.camera.pro
https://play.google.com/store/apps/details?id=com.selfiepro.camera
The app genre and remote server used by the adware lead us to believe that they may be related to the malicious apps reported by Trend Micro in late January.
What can you do?
1 - Get antivirus software like Avast Mobile Security which detects these types of apps, protecting users from the annoying adware.
2 - Download apps from reputable developers. Even though Google Play Store is considered to be a reputable app stores, you should still be careful to check the reputation of the app developers.
3 - Read the app description and read reviews. If there are lots of typos, that should give you a clue that the app may not be legitimate. If the reviews are mostly negative and mention adware, that is another signal to not download the app.
4 - Uninstall apps immediately when any abnormal behaviors observed.
Files Analyzed