Avast Threat Labs finds Android device firmware that reroutes ad network revenue to unknown accounts.
After publishing our story about pre-installed malware on Android devices, we continued to analyze the firmware images of cheap Android devices. It is a rather sad endeavour, as our statistics put pre-installed malware as one of the top infection vectors. But, today we have a bit of a lighter story.
It is not important which device’s firmware we’re examining today, because it is an old one (Android 6.0) and the device received a software update that removed the “feature.” We are not sure whether the device was certified by Google, but it had Google Apps installed and was sold in Europe. It had the usual issues that cheap Chinese devices tend to have: an insecure update mechanism, ad networks that automatically install more apps on the phone, ads on the lock screen, you name it. But hidden in the device’s firmware was something more nefarious.
The firmware was replacing ad network tokens in applications the user installed with its own. The tokens work a bit like bank account numbers: they tell the ad network where to send the money generated by displaying ads in your application. In this case, all of the money generated by certain ad networks on this device were redirected to an unauthorized account.
Analysis
DeviceFocusUtil class
Hidden in the /system/framework/arm/boot.oat file is a class called com.android.internal.os.DeviceFocusUtil. Despite its name, it is not a part of the Android OS. It was added by somebody preparing the firmware for this device.
The code is not obfuscated at all, so it’s easy to see the class is parsing a configuration file from /system/framework/framework.jar, com/android/security/security.properties. This file is base64-encoded JSON, “encrypted” by mapping the alphabet to a slightly shifted one. When decrypted, it contains information about which ad tokens to replace with what value and where to find the ad token.
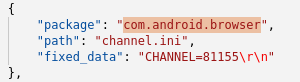
 excerpt from the configuration file
excerpt from the configuration file
The packages mentioned inside the configuration file tell us this feature was targeted at the Chinese market, as it hijacks mainly the Chinese Umeng ad network.
The configuration file is auto-updated from the internet, but the server is already dead. The suspicious URL is how we noticed something wrong with this part of the firmware. This is the URL:
hxxp://service-safemgr.yy845.com:8082/safeconfigmanager/services/SafeConfigWebService
Every app stores the ad token in a different place, so this firmware modification has to be smart and hijack all of them.
SharedPreferences
SharedPreferences are a way for an application to store key->value data. Some apps store the ad token there, so the internal method in class android.app.SharedPreferencesImpl, which loads preferences from the disk, is injected with a call to the DeviceFocusUtil class.
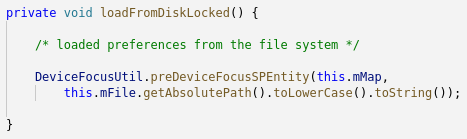
Inside, the app’s package name is matched against the shared_preference section from the configuration file, and the ad tokens are replaced.
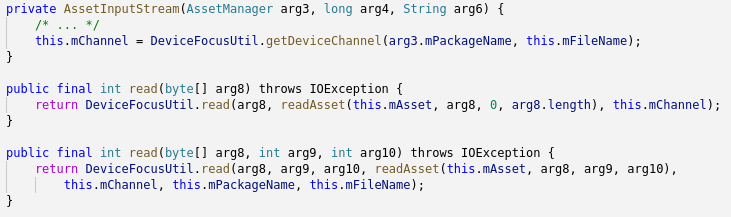
AssetManager
Some apps store the ad token inside their APK files as so-called “assets.” The Android OS provides an API to access these files easily, and it is injected with calls to DeviceFocusUtil too. Contents of the file that the app requested are replaced with the fixed_data value from the configuration file if the channel_file value matches.
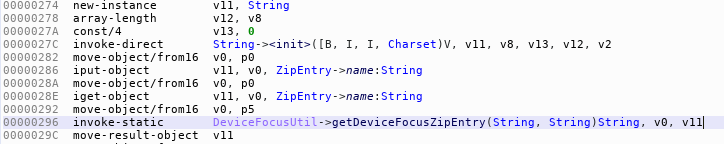
ZipEntry
If the file with the ad token is stored elsewhere in the APK, the app may load it using the APIs to access ZIP files. The java.util.zip.ZipEntry class is again injected with DeviceFocusUtil, so only the forged data from the configuration file is loaded.
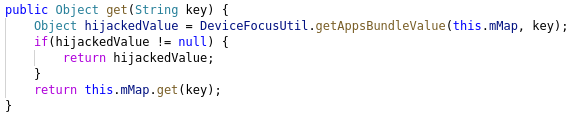
Bundle
Bundles are a way to pass data around for Android apps. They work like a key->value mapping, so the methods to get data from the bundle are injected.
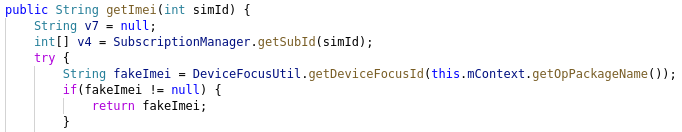
Fake IMEI number
As if redirecting the flow of money from ads was not enough, this feature also attempts to deceive the ad networks into generating more money for it. Usually, ad networks track the user across different apps, so they can distinguish between unique views (which generate more money than multiple views by a single user). They commonly use the IMEI and/or MAC address of the phone to do so.
So DeviceFocusUtils simply makes the API calls to get the IMEI or MAC address to return a different value for each app. The ad network thinks every ID is a different user, and therefore it can generate more money. Unfortunately this function appears to be broken, and seems to be returning “0” as the IMEI every time instead.
Conclusion
From the amount of hijacked apps, we can tell that this is no quick hack, but a purposefully developed feature. The ad situation in China is entirely different than what we usually encounter elsewhere. And, it unfortunately affects cheap smartphones sold in Europe as well.
Consider this - the configuration file assumes that the pre-installed web browser is modified to show ads too, and attempts to steal the revenue from them.
Presumably though, it did not work very well, as we can’t imagine ad networks not catching onto this. The feature was removed from the next version of the firmware and the update server is no longer operational.
Cyber criminals targeting Android devices to rake in money in fraudulent revenue is nothing new. But, the ways they target change often. As always, our team will continue monitoring for new threats to keep Avast users safe from hackers and malware.