Most of today’s malware authors create malware for one of two reasons: either to make money or to steal valuable data.
An Android Trojan is spying on its victims and even tricking some into giving up their credit card information.
Most of today’s malware authors create malware for one of two reasons: either to make money or to steal valuable data. In this blog post, we will show how an Android Trojan relies on social engineering.
Social engineering tactics are used to trick people into performing an action, like clicking on a link or downloading an application. The person being tricked thinks they are doing something innocent when they are really clicking on or downloading something malicious. This malware is associated with the banker family as it tries to steal user's credit card information.
Once installed, the Banker Trojan puts an icon in the launcher. The app name shown with the icon can vary from sample to sample -- some of the names we have seen were : AVITO-MMS, KupiVip and MMS Центр (MMS Center).
Hide and seek
Immediately after launching the app for the first time, the icon is hidden from the launcher to make the Trojan a bit more elusive. The app then proceeds to do a simple check for an emulator. If the check confirms that the app is running in an emulator, no malicious activity is started.

The main screen
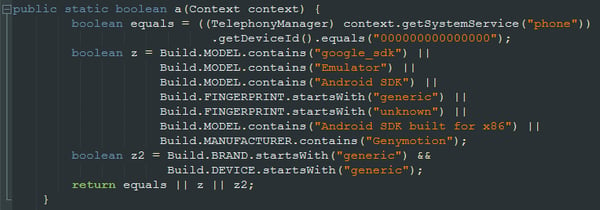
Emulator check
If the Trojan doesn’t detect that it is running in an emulator, it starts a background timer that continually shows the Device Admin activation dialog, until the app receives device administrator rights. This can be very irritating, as the dialog keeps reappearing immediately after clicking on the "Cancel" button.
Once the app receives device administrator rights, the same process is repeated again, but with the set default SMS manager dialog.
On Android Marshmallow, you can try to uninstall the app even with the annoying screens popping up all the time, by going to settings with the top-down swipe. This approach, however, doesn’t work on the KitKat version of Android.
The Trojan wants device administrator rights to be able to achieve two things:
- To be harder to uninstall
- To have the capability to remotely lock the device
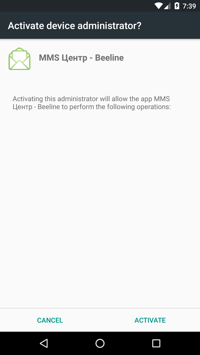
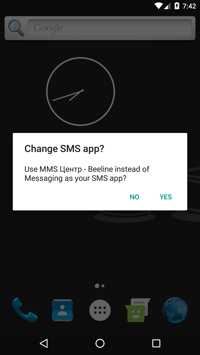
Device admin dialog
The main functionality of the Trojan is to send out information about the device to a C&C (command and control) server and to then wait for the server to respond with new commands to carry out. It can also automatically send an incoming SMS message to the server.
The general information that is sent to the C&C server:
- IMEI
- ISO country code
- SIM operator name
- Android build version
- Phone number
- SIM serial number
- Is this app the default SMS app?
- Is this app the device admin?
- The current version number of the Trojan
- Generated unique user ID for this phone
One of the commands the C&C server sends shows a screen on the infected device that prompts the victim to enter credit card information. The screen includes Google Play, but if you look carefully, ‘Play’ is written with a lowercase ‘p’.
The Google Play logo is probably used to trick people into thinking they are updating their Google Play account. If the victim falls for this, the credit card information is immediately sent the to the C&C server.
In addition to the initial information sent to the C&C server, there are many more functions that can be requested remotely such as:
- Download an APK and prompt user to install it
- Get call logs
- Get SMS inbox
- Get bookmarks
- Get contacts
- Get list of installed apps
- Get GPS coordinates of the device
- Lock the screen
- Redirect calls to a specific number

Fake Google Play screen
Infections: The count of infections we have seen per day can be seen in the graph below, as you can see, the first half of February was the most active period.
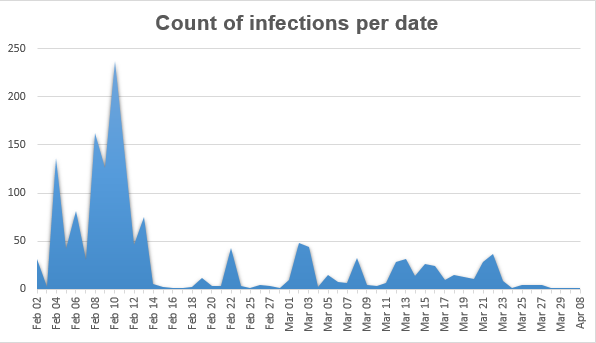
Number of hits seen per day
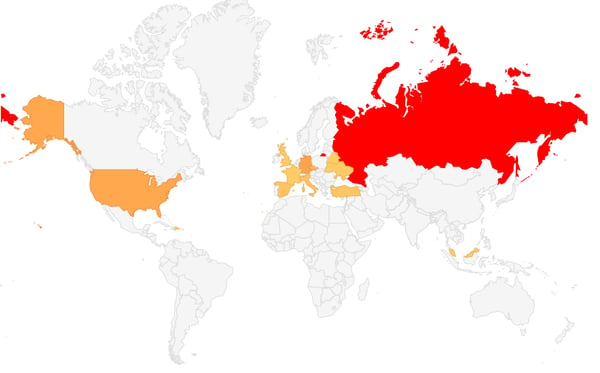
The vast majority targeted were from Russia, followed by Germany, the U.S. and Czech Republic.
How to avoid this Trojan and other mobile malware
Now you are probably wondering, “What can I do to protect myself from Trojans like this?”. Simply put, Prevention is Key.
We cannot stress this enough: Download antivirus software on all of your devices, be it your mobile devices, PC or Mac.
This particular Trojan is detected by Avast Mobile Security as Android:Banker-IR [Trj]. Avast Mobile Security will warn you upon downloading this app’s APK (Android application package) file that it is malicious and that you should remove it before you launch the app and get locked in the flurry of the aforementioned dialogs. Enabling the device admin for the app and disabling it does not help either -- if the app does not have administrative rights, it will continue to flood with request dialogs.
The Banker being detected by Avast Mobile Security
In addition to having antivirus installed, it’s good practice to backup your data either automatically or regularly.
What to do if you are infected
In case your device does get infected and locked by dialogs like the ones mentioned here, you can power down your phone and restore it to its factory settings. Restoring your phone to its factory settings will remove all user data and installed apps, including the virus.
Also, as mentioned earlier, you can access the settings even over the dialog flood on the newer versions of Android.
In some rare cases, particularly on less powerful devices, the dialog request for device administrator rights shows up slower. You may then try to dodge the dialog over and over again by repeatedly pressing the recent apps/home button to try and reach your settings to uninstall the malicious app. This situation, however, happens rarely.
Lastly, if you do have USB debugging enabled and have access to your phone via a trusted PC, you can try to kill the application via ADB (Android Debugging Bridge) and then uninstall it. This option is only for advanced users and generally, leaving your phone with permanent USB debugging enabled could mean that anyone who gets ahold of your phone, even if only for a short time, can get access to all the data located on your phone.
The best way to protect your data is by using an antivirus and by backing up your files on a regular basis. This way, you can get the most from your device without compromising your safety.