Microsoft has found that various browsers are being targeted with ad-injection malware called Adrozek. At the attack's peak in August, the malware was observed on more than 30,000 devices every day, according to the researchers.
The browsers at risk include Chrome, Firefox, Edge, and the Russian-based Yandex. That's a lot of different devices and certainly the potential for infection is huge, particularly if users are running older browser versions.
The malware was first seen in May 2020 and is designed to inject phony ads when you attempt to do internet searches. Here is before and after examples of what a typical search results page will look like:
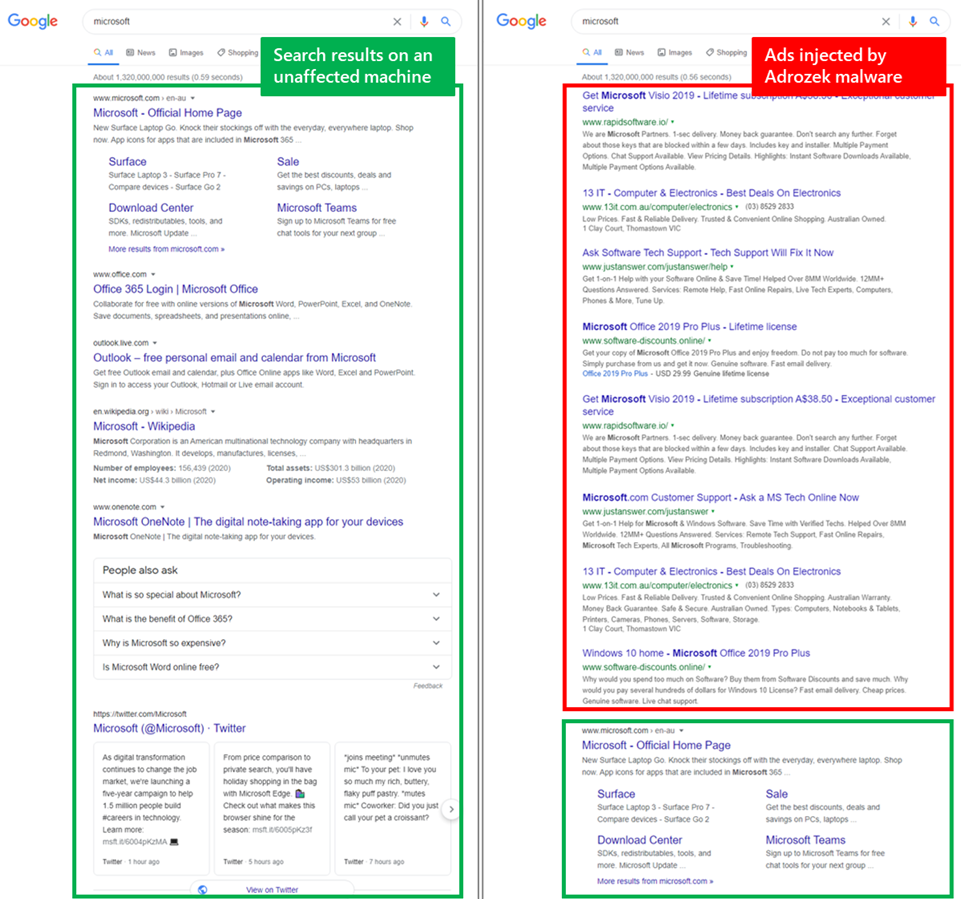
Adware-based malware can run the gamut from relatively annoying (replacing real ads with ones that will generate money through their clickstream) to the dangerous level that Adrozek inhabits. This is because Adrozek is very invasive, disabling your browser updates and safe browsing features, installing and then hiding specialized browser extensions, changing security preferences and (on Firefox) stealing passwords that are saved by your browser. Ouch!
The annoying — and dangerous — end of adware works this way: they insert these bad ads into search results pages through browser extensions that you may not know about that can tamper with these pages. Users that are looking for particular keywords then click on the bad ads and then the criminals earn affiliate payments from the clicks. This isn’t a new effort: adware clickstream hijacking has been around almost since the web became popular. What is new, however, is the level of sophistication and persistence that Adrozek has exhibited.
One of Adrozek’s features, if you can use that word in this context, is that the malware is polymorphic. This means that it changes its code and the executable file name every time it is downloaded, making it harder to detect. Researchers found thousands of different versions, running off of more than 150 different domains. It also has a very dynamic distribution mechanism, with some of the domains hosting the malware only online for a day — although others were up for months.
Microsoft expects that we haven’t seen the last of this malware, and it will be very difficult to eliminate because of its shape-shifting efforts. What makes matters worse is that the malware also can persist after a reboot, thanks to Windows Registry modifications. Double ouch!
The malware is spreading throughout the world, although at the moment, it's concentrated in Europe and southeast Asia.
What can you do to prevent this attack?
First off, ensure that you regularly update your browser and check your installed extensions. Second, if you are running Windows 10, Microsoft’s built-in Defender Antivirus should stop it. Finally, you can use a better browser, such as Avast Secure Browser, for added protection. Avast Secure Browser offers protection against Adrozek as long as Avast Antivirus is installed. You should ensure that the Self-Defense Module is enabled.
If you want more details, Microsoft describes the specifics and how to recognize what the malware has monkeyed with on the link cited above.